剧情
在一次成功的社交工程参与后,你获得了企业工作站的用户级凭证。你的目标是利用这次初始访问权限对内部Windows主机进行深度侦察。最终目标是升级权限并从管理员目录捕获根标志,以展示系统全面被攻破。
初始凭证:tyler.ramsey:P@ssw0rd!
原文:
Following a successful social engineering engagement, you have obtained user-level credentials for a corporate workstation. Your objective is to leverage this initial access to perform deep reconnaissance on the internal Windows host. The final goal is to escalate privileges and capture the root flag from the administrator's directory to demonstrate full system compromise.
Starting Credentials: tyler.ramsey:P@ssw0rd!
远程桌面
由于已经有初始凭证了,我们直接连接远程桌面即可
xfreerdp3 /v:10.0.21.24 /u:tyler.ramsey /p:P@ssw0rd!
提权
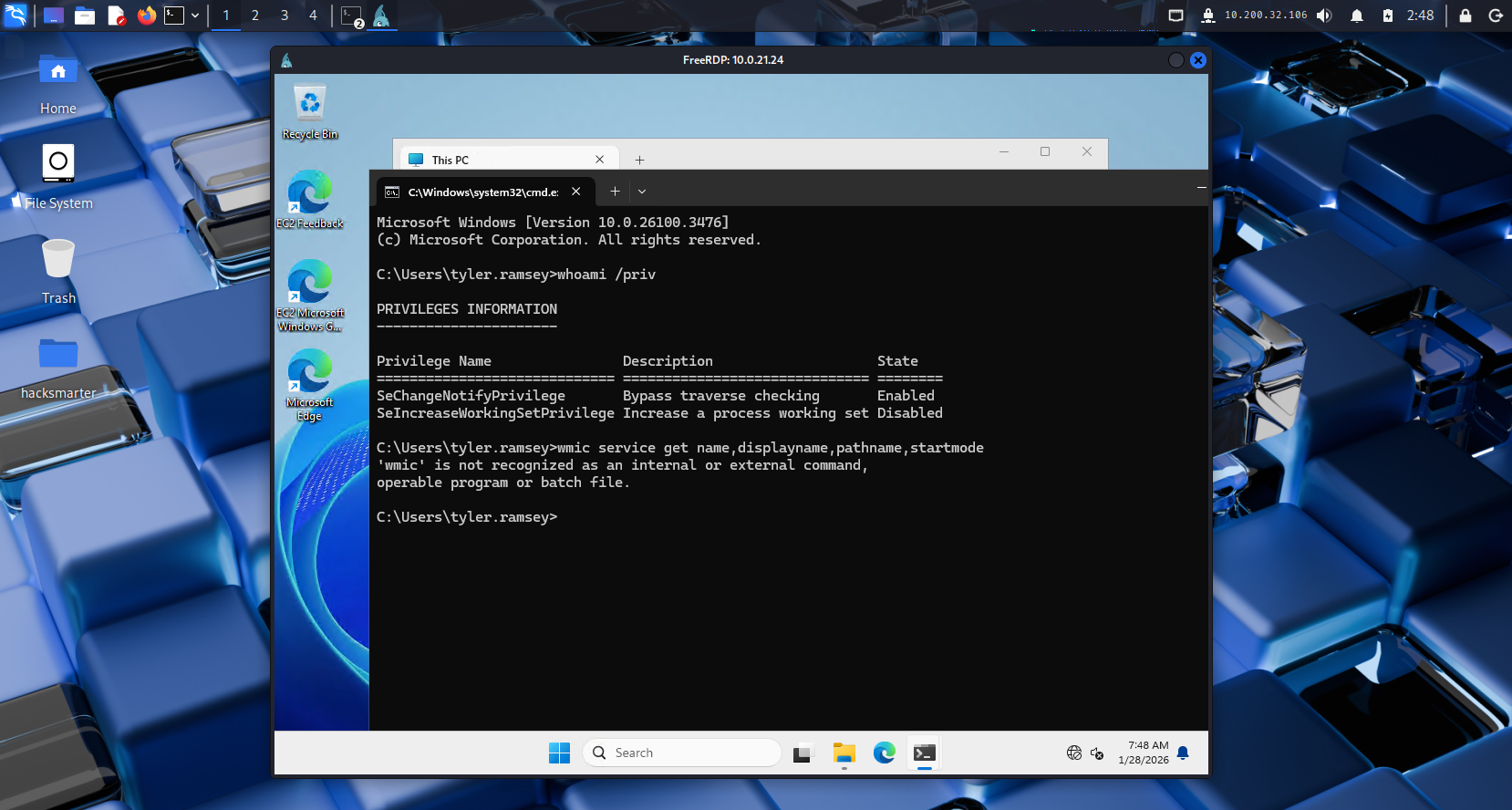
查看当前账户有没有特权
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
借助ai总结了一下这里可能出现的结果
| Privilege | 能否直接提权 |
|---|---|
| SeChangeNotify | ❌ 不能 |
| SeIncreaseWorkingSet | ❌ 不能 |
| SeImpersonate | ✅ 能 |
| SeAssignPrimaryToken | ✅ 能 |
| SeDebug | ⚠️ 偶尔 |
| SeBackup / Restore | ⚠️ 文件提权场景 |
根据表格判断这里无法直接使用土豆家族(利用token)进行提权。
枚举服务(是否可以修改)
查询有提权价值的服务
PS C:\Users\tyler.ramsey> Get-CimInstance Win32_Service |
>> Where-Object {
>> $_.PathName -and
>> $_.PathName -match '\.exe' -and
>> $_.PathName -notmatch 'svchost.exe' -and
>> $_.PathName -notmatch 'C:\\Windows\\' -and
>> $_.StartMode -eq 'Auto'
>> } |
>> Select Name, StartName, StartMode, PathName
Name StartName StartMode PathName
---- --------- --------- --------
Amazon EC2Launch LocalSystem Auto "C:\Program Files\Amazon\EC2Launch\service\EC2LaunchService.exe"
AmazonSSMAgent LocalSystem Auto "C:\Program Files\Amazon\SSM\amazon-ssm-agent.exe"
edgeupdate LocalSystem Auto "C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.ex...
MDCoreSvc LocalSystem Auto "C:\ProgramData\Microsoft\Windows Defender\Platform\4.18.25090.3009...
WinDefend LocalSystem Auto "C:\ProgramData\Microsoft\Windows Defender\Platform\4.18.25090.3009...
WSLService LocalSystem Auto "C:\Program Files\WSL\wslservice.exe"
一共六个服务,去除掉edgeupdate、WinDefend、MDCoreSvc这几个系统自带的服务后,检查剩下的三个服务对应的目录是否有可写权限
PS C:\Users\tyler.ramsey> icacls "C:\Program Files\Amazon\EC2Launch\service"
C:\Program Files\Amazon\EC2Launch\service: Access is denied.
Successfully processed 0 files; Failed processing 1 files
PS C:\Users\tyler.ramsey> icacls "C:\Program Files\Amazon\SSM"
C:\Program Files\Amazon\SSM NT SERVICE\TrustedInstaller:(I)(F)
NT SERVICE\TrustedInstaller:(I)(CI)(IO)(F)
NT AUTHORITY\SYSTEM:(I)(F)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(IO)(F)
BUILTIN\Administrators:(I)(F)
BUILTIN\Administrators:(I)(OI)(CI)(IO)(F)
BUILTIN\Users:(I)(RX)
BUILTIN\Users:(I)(OI)(CI)(IO)(GR,GE)
CREATOR OWNER:(I)(OI)(CI)(IO)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(OI)(CI)(IO)(GR,GE)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(I)(OI)(CI)(IO)(GR,GE)
Successfully processed 1 files; Failed processing 0 files
PS C:\Users\tyler.ramsey> icacls "C:\Program Files\WSL"
C:\Program Files\WSL NT SERVICE\TrustedInstaller:(I)(F)
NT SERVICE\TrustedInstaller:(I)(CI)(IO)(F)
NT AUTHORITY\SYSTEM:(I)(F)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(IO)(F)
BUILTIN\Administrators:(I)(F)
BUILTIN\Administrators:(I)(OI)(CI)(IO)(F)
BUILTIN\Users:(I)(RX)
BUILTIN\Users:(I)(OI)(CI)(IO)(GR,GE)
CREATOR OWNER:(I)(OI)(CI)(IO)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(OI)(CI)(IO)(GR,GE)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(I)(OI)(CI)(IO)(GR,GE)
Successfully processed 1 files; Failed processing 0 files
AmazonSSMAgent和WSLService,BUILTIN\Users:(RX),只有读权限,没有写权限,不能EXE替换,不能DLL投放
Amazon EC2Launch,Access is denied,连“列目录权限”都没有
自动化工具
简单尝试了一些手工操作后,感觉这台机器可能并不容易手工提权,所以我尝试使用PEASS-ng来进行自动化操作。
直接将exe拷贝进目标机器被windows defender给杀了,尝试运行bat文件倒是没被杀。
winPEAS.bat > 1.txt
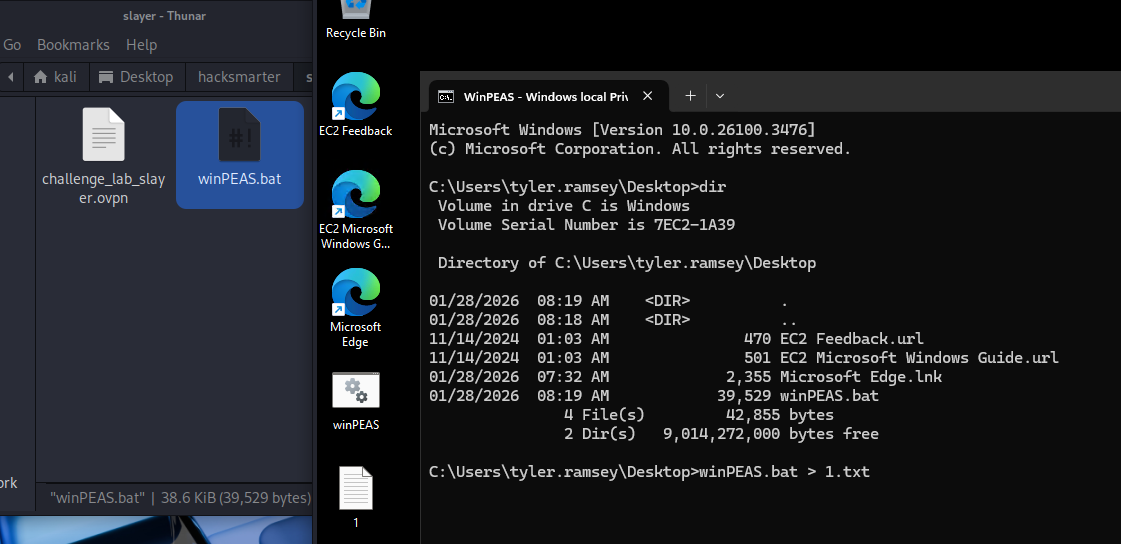
在结果内显示有powershell的历史记录,并且文件有大小,应该不是误报,尝试读取
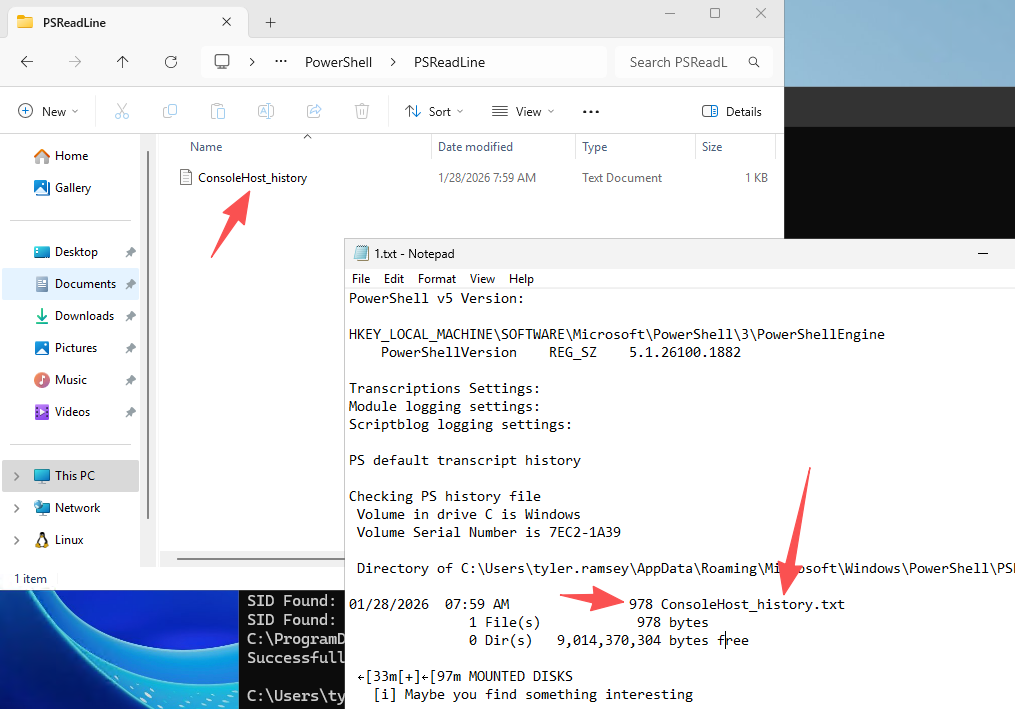
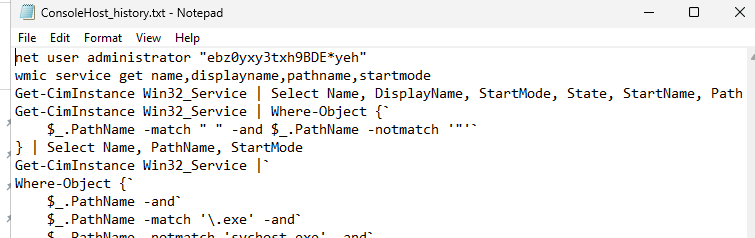
第一条命令记录就是在重置管理员密码:administrator/ebz0yxy3txh9BDE*yeh
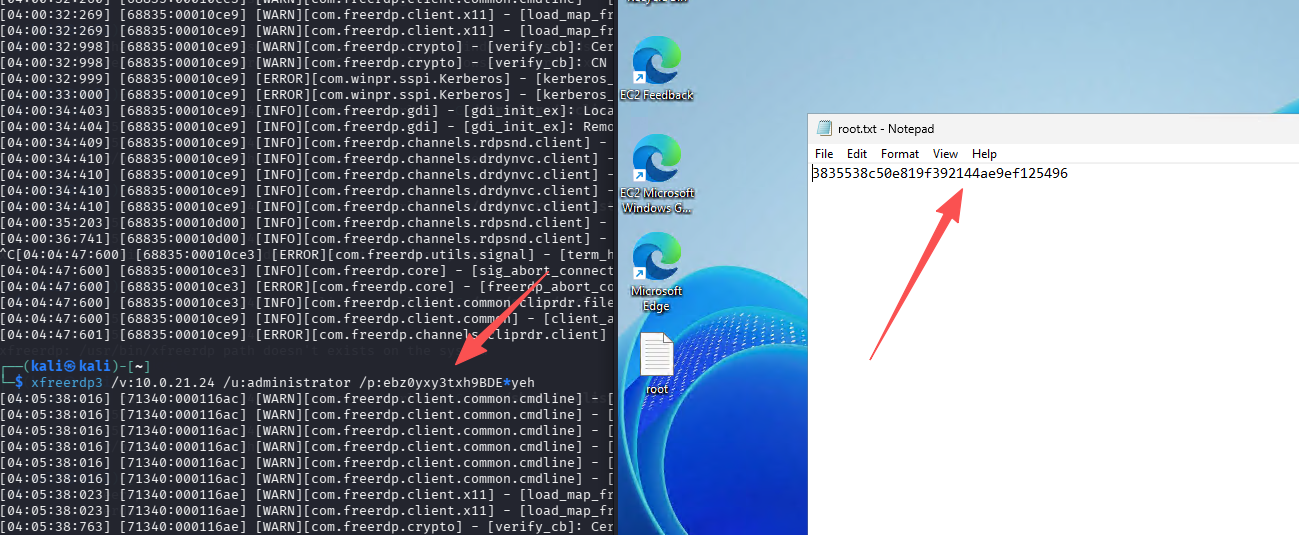
尝试上号:xfreerdp3 /v:10.0.21.24 /u:administrator /p:ebz0yxy3txh9BDE*yeh,在管理员桌面成功拿到flag

后话
查了一些writerup后发现,其实在登录低权限用户后,打开powershell,一直按↑键就能找到改管理员密码那条命令
复现一下:
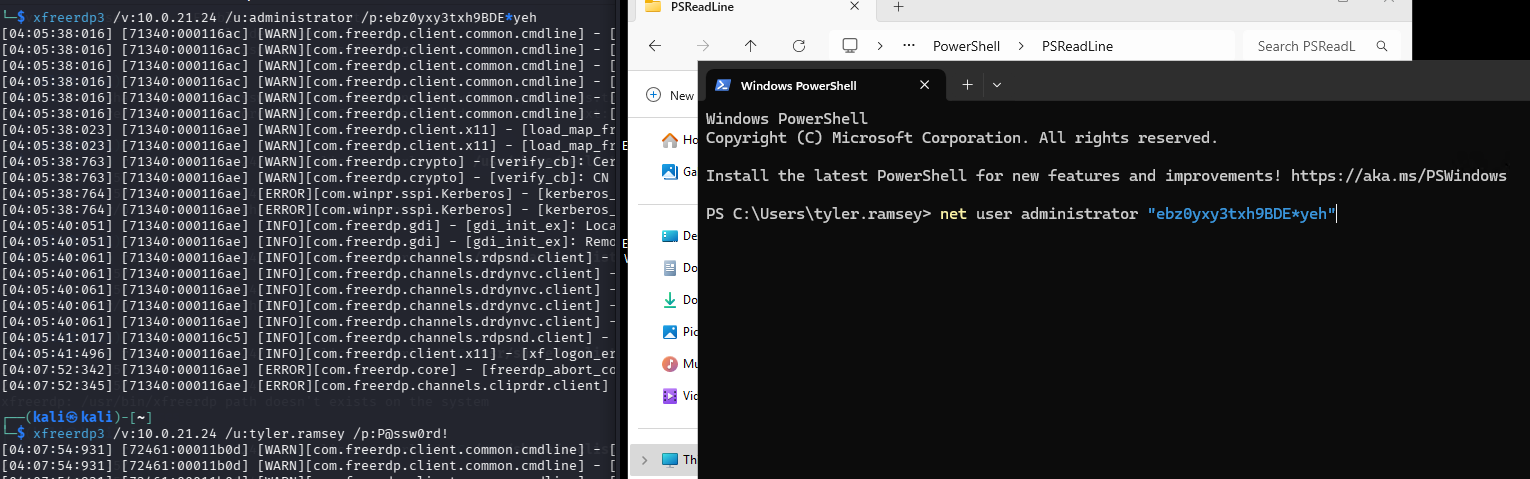
只能说,记住了…在linux上倒是经常查看history,Windows上因为cmd没有记录就忘了这回事。